Cyber Teams
Thinking Purple: A new HTB Academy category merges red and blue teaming
Learn purple teaming with HTB Academy’s newest category—build awareness of red and blue operations to boost your threat response times

JXoaT,
Jun 27
2025
Table of Contents
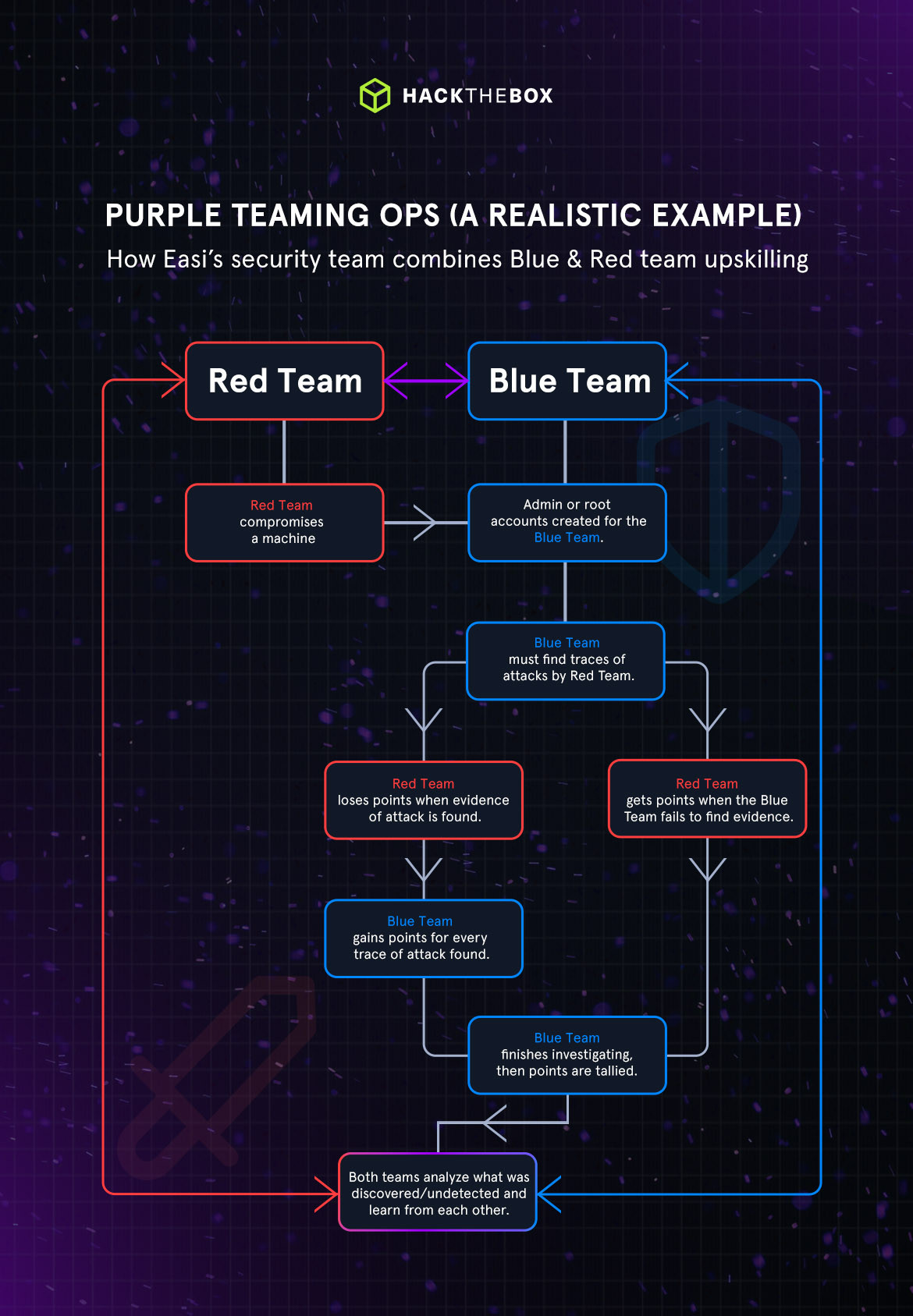
Purple Modules are now available on HTB Academy for individuals and teams. An exciting step for anyone looking to engage internal threats and buff security departments with fresh intel.
HTB Academy casts a wide net over a variety of individualized blue and red content, but Purple Modules utilize both sides to tell a story, one that merges both perspectives to dig for suspected threats.
Blue, red, purple? We get it. Our field goes a little overboard on color coding. Some of us can get a little sick of it, but just in case you haven’t got a taste for this particular flavor of security, give this a read.
Who is purple, and why do we care?
Traditional security roles typically split into clear-cut offensive (red team) and defensive (blue team) responsibilities. While specialization remains valuable, modern threat actors have grown increasingly evasive, exploiting gaps and communication breakdowns within large, complex enterprise environments.
Purple Teaming includes more easily identifiable roles, such as threat hunters or threat intelligence analysts, who are constantly digging up new information.
But here’s a common problem.
Security teams may lack structured channels for clearly communicating threat data and translating that data into defensive actions. It becomes significantly more important when the concept of dwell time, a measure of how long an attacker remains undetected, is taken into account.
Training to track, classify, validate, and communicate threats might roam across departments, but it is a job on its own. It isn’t just a role, it’s a methodology that should be practiced among teams.
The solution: Purple teaming (regardless of role or practice) bridges this gap by fostering clear communication, active collaboration, and actionable intelligence-sharing between offensive and defensive perspectives.
For threat hunters, SOC analysts, and internal security stakeholders, this comprehensive approach creates essential 360-degree visibility, enabling quicker, clearer, and more effective responses to emerging threats.
Whether you’re looking to be the first on your team to spot an internal threat in the wild or become a new source of truth for teams to build around, our Purple Modules offer a structured, practical way forward.
What can our current Purple Modules prepare you for?
1. Intro to Purple teaming
This foundational Module introduces you to the essence of HTB Academy’s Purple Modules. You’ll explore how bridging offensive and defensive tactics provides a holistic understanding of cybersecurity incidents.
One of the core strengths of this Module is that it is a Threat Spotlight Module. This means it utilizes recent vulnerabilities and breaches to give you a direct view of how critical vulnerabilities are being exploited in the wild.
You will practice forensic techniques, including detailed logging, comprehensive traffic and memory capturing, while getting hands-on experience with Digital Forensics and Incident Response (DFIR) tools.
Who should take this?
-
Cybersecurity learners looking to bridge red and blue skillsets.
-
Practitioners curious about modern vulnerabilities and their impact.
-
SOC analysts and threat hunters aiming to sharpen investigative capabilities.
-
Internal security stakeholders seeking a unified threat response strategy.
2. Windows Attacks and Defense

For over two decades, Microsoft Active Directory (AD) has remained at the core of enterprise identity management. However, increased integration of applications and sensitive data into AD environments has amplified vulnerability to large-scale compromises.
In this advanced Module, you’ll methodically explore the most prevalent and critical attacks against Active Directory infrastructures, including techniques for horizontal and vertical privilege escalation and lateral movement.
Equally important, the Module prioritizes defensive methods, clearly outlining actionable prevention and detection strategies to counteract each attack type covered.
Who should take this?
-
IT and cybersecurity professionals managing or auditing Windows and AD environments.
-
Threat hunters focused on proactively securing enterprise networks.
-
Teams interested in detailed methods to detect, respond to, and prevent AD-centric threats.
Learn to follow Windows threats
3. Detection & OpSec Cyber Range

Now that you’re armed and ready for the hunt, it’s time to put yourself straight onto the playing field. This Module is a major advancement for teams looking to supercharge their threat detection capabilities and operations broadly!
The Detection & OpSec Cyber Range Module brings you into a pre-built enterprise network with Windows & Linux machines, actively generating real logs as attacks occur. Logs are aggregated into Splunk (industry-leading SIEM) or Wazuh (open-source SIEM/XDR) for a central view.
It being a Targeted CyberOps Module means the space can be utilized for red, blue, and purple teams to practice together! And the use cases can vary depending on need and desired training.
Want to test yourself for adversarial malware?
The red team can engage in anything from evasion to deploying malware for low-detection training. In the case of a malware drop, the blue team can respond by leveraging the suite of tools to begin detection and response, to catch the malware for analysis.
Ultimately, a macroscopic view of team activities and actions can be turned into fuel for developing a stronger security posture, preparedness for threat hunters, but also provide a great space for teams to conduct attack-and-defend scenarios—the purple.
The setup has never been easier.
Who should take this?
-
Pentesters and red teamers looking for field testing techniques and
-
SOC analysts looking for a proving ground for accessing incoming attack data.
-
Threat hunters and detection engineers set on turning attack logs into threat intelligence.
-
Teams ready to run realistic drills and verify if you’re vulnerable to the next attack.
Ready to begin?
Purple Modules equip learners and teams alike to think, respond, and communicate clearly in the face of complex scenarios. Dive into our new category now to sharpen your skills, protect your environment, and boost your team's effectiveness.
Purple teaming creates impact by empowering security practitioners with a focused perspective on threat activities, leveraging both offensive and defensive knowledge to unify team readiness. Actions by a purple practitioner provide utility to multiple teams under security operations by making the unknown or vague known.













