Quantify and manage your
cyber risk exposure
Think like attackers—simulate threats, track progress and prove
readiness with courses, ranges, or team exercises.



Trusted by 1,000+ cybersecurity teams
Why offensive skills matter now
Of companies have in-house exploit expertise to meet today's threat landscape.
Skill gaps triple mean time to respond,
extending breach
impact windows
and costs.
Decrease in risk and security incidents with
threat-led pentesting programs in place.

Hands-on-first learning methodology
Our platform focuses on practical skills development in real-world environments, not theoretical knowledge that doesn't transfer to actual red team engagements.
3x
Faster ramping time
for new hires
90%
MITRE and NIST
coverage in 6 months
50%
Decrease in time
patching CVEs

Full-scope adversary
Replicate full kill chains, from open-source recon to final data exfiltration, to understand how early actions cascade into business critical impact.

Continuous skill measurement
Use advanced reporting and analytics to have accurate, real-time visibility into teams' skill proficiency at any time. Identify critical gaps and build future plans.

Framework alignment
All our content library maps to NIST and MITRE frameworks, ensuring your team builds skills keeping up with the threat landscape and regulatory requirements.
How red teamers
use Hack The Box
Training Plans
Combine job role paths with more than 1,200 labs simulating the latest security vulnerabilities and vectors, with new scenarios added every week.
Ranges
Jump into full enterprise-scale networks with realistic pivoting, IDS evasion and exploitation techniques proving real-world offensive capability.
Team Assessments
Test and benchmark pentesting skills with pre-made or custom CTF events. Build and deploy your event in less than 10 minutes, choosing between 180+ scenarios.
Training Plans
Use 1,000+ courses and labs to progress from fundamentals to advanced adversary emulation while learning how to adopt new technologies in your engagement - including AI.
Ranges
Premium red team scenarios designed to provide an accurate adversary simulation against fully patched, enterprise technologies to replicate real-world cyber attackers' TTPs.
Team Assessments
Spin up custom red team assessments (jeopardy or AD chains) for cyber teams, with live leaderboards, time scoring, and post-event analytics that spotlight collective strengths or skill gaps.
Training Plans
Combine threat-informed courses with CVE scenarios and learn how to conduct penetration tests against modern and highly secure applications.
Ranges
Use cyber ranges to deploy malware and to observe the behavior from a defender's viewpoint. This is invaluable for red teams aiming to craft low-detection tools and sharp techniques.
Team Assessments
Host custom events loaded with reverse engineering and full-pwn scenarios with latest exploit techniques – live leaderboards and analytics spotlight strengths and gaps across the team.
Training Plans
Combine job role paths with more than 1,200 labs simulating the latest security vulnerabilities and vectors, with new scenarios added every week.
Ranges
Jump into full enterprise-scale networks with realistic pivoting, IDS evasion and exploitation techniques proving real-world offensive capability.
Team Assessments
Test and benchmark pentesting skills with pre-made or custom CTF events. Build and deploy your event in less than 10 minutes, choosing between 180+ scenarios.
Training Plans
Use 1,000+ courses and labs to progress from fundamentals to advanced adversary emulation while learning how to adopt new technologies in your engagement - including AI.
Ranges
Premium red team scenarios designed to provide an accurate adversary simulation against fully patched, enterprise technologies to replicate real-world cyber attackers' TTPs.
Team Assessments
Spin up custom red team assessments (jeopardy or AD chains) for cyber teams, with live leaderboards, time scoring, and post-event analytics that spotlight collective strengths or skill gaps.
Training Plans
Combine threat-informed courses with CVE scenarios and learn how to conduct penetration tests against modern and highly secure applications.
Ranges
Use cyber ranges to deploy malware and to observe the behavior from a defender's viewpoint. This is invaluable for red teams aiming to craft low-detection tools and sharp techniques.
Team Assessments
Host custom events loaded with reverse engineering and full-pwn scenarios with latest exploit techniques – live leaderboards and analytics spotlight strengths and gaps across the team.
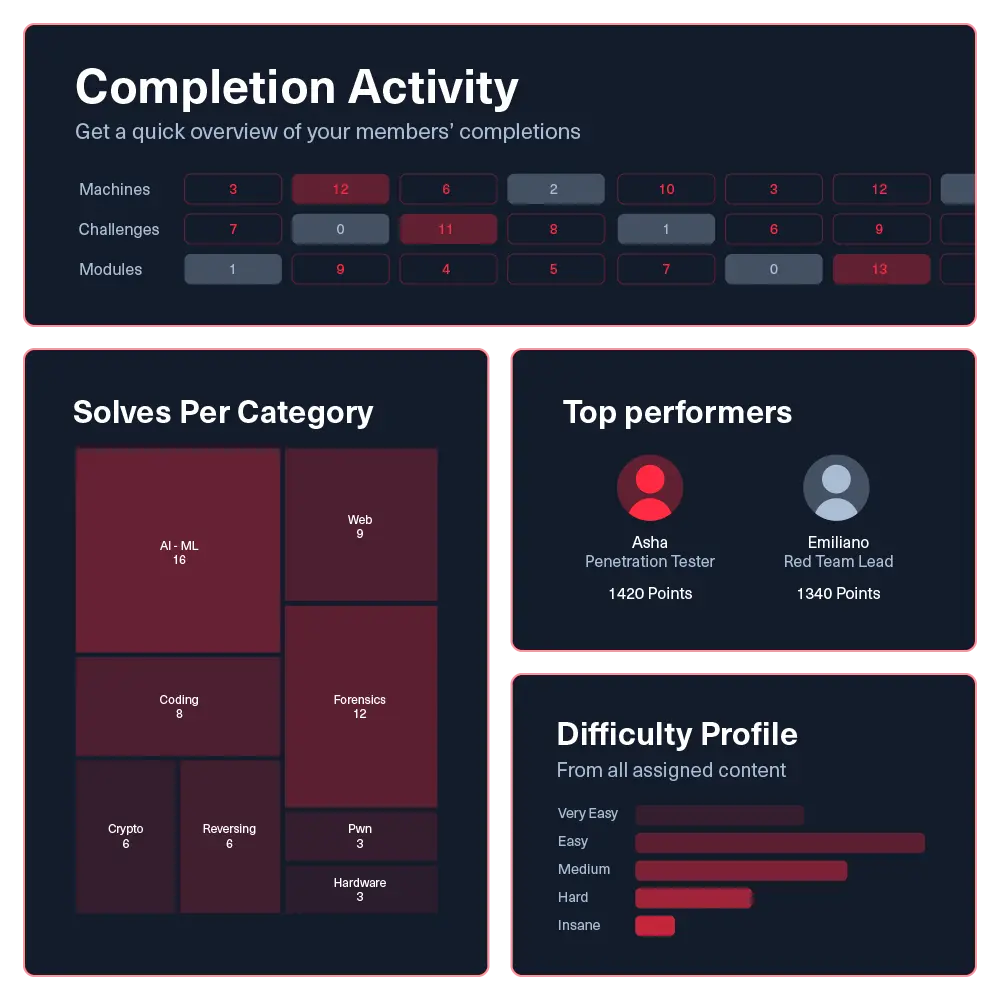
Data-driven cyber resilience
Measure security team performance with reporting features that
demonstrate skill growth and operational readiness.
Individual & team analytics
Track key metrics like MTTD, alert precision, and investigation quality at both the individual and team level.
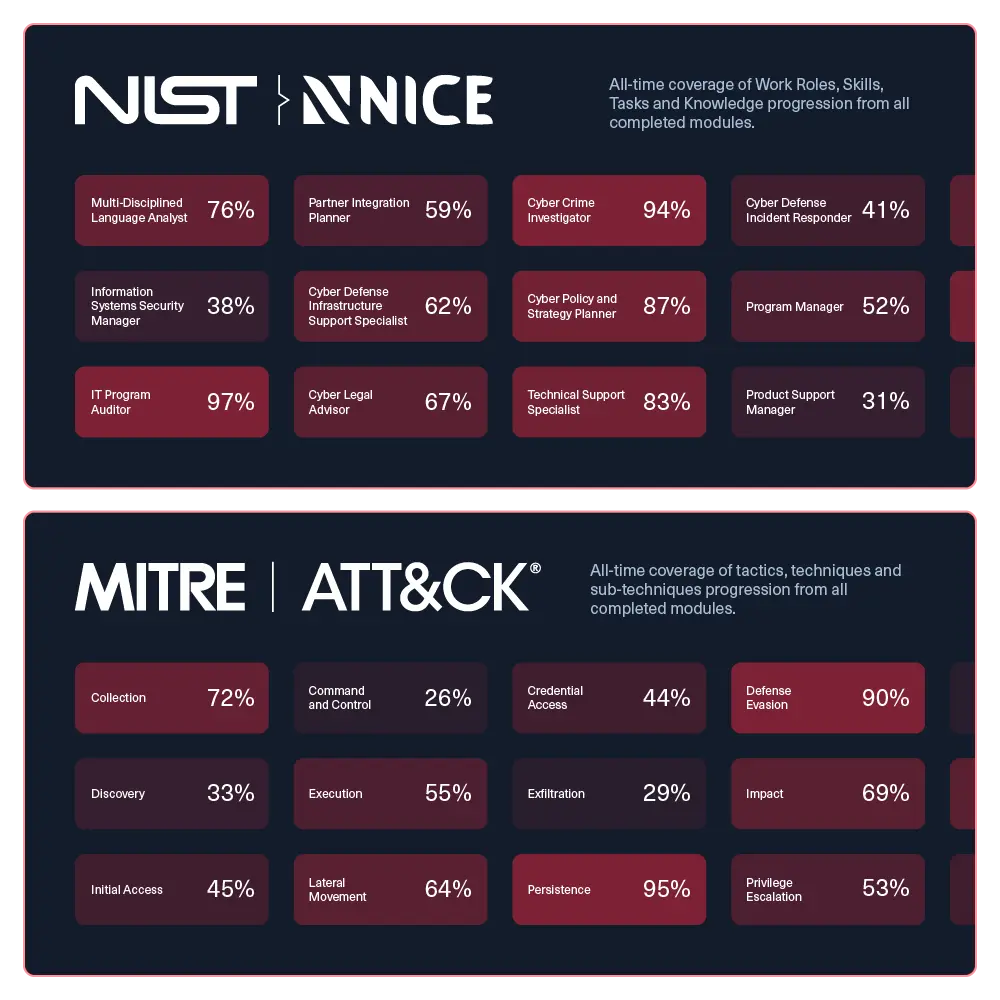
Skill coverage heatmaps
Visualize team proficiency against MITRE ATT&CK and NIST NICE framework to identify capability gaps that need focus.
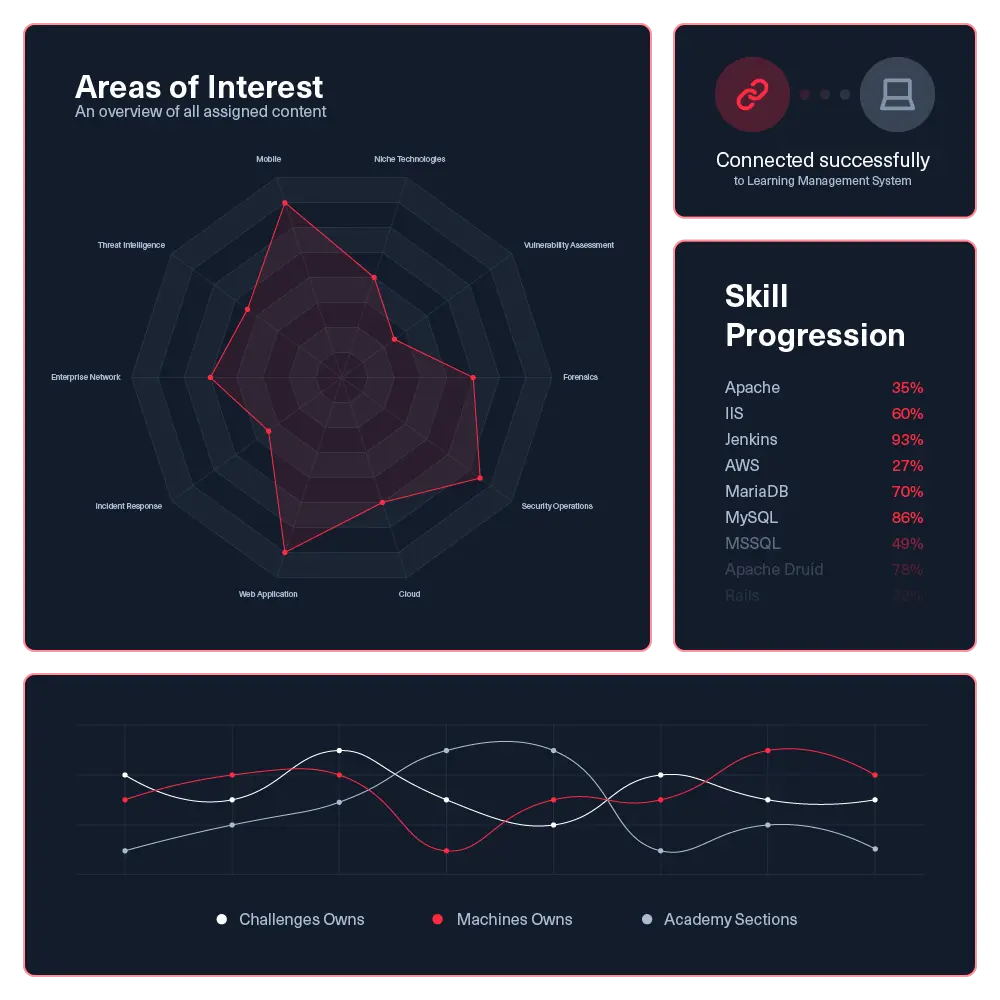
Customization and integration
Export or connect skill metrics and progression to your LMS system to track growth as part career advancement.
How major global organizations
stay ahead of threats
HTB gamified labs walk newcomers through the entire kill-chain (from recon to privilege escalation) so they internalize real adversarial techniques and gain a threat-ready mindset.
Seasoned red teamers can replay APT playbooks, develop custom C2 profiles, and measure skill progression, sharpening threat readiness while expanding their arsenal of tactics, techniques, and procedures.
Role-based analytics, ATT&CK heat-maps, and skill gap reports give leaders clear proof of red team maturity, enabling targeted programs that validates adversary coverage and reduces organizational risk exposure.

HTB has given us the ability to rapidly respond to changes in our required skillset. If leadership shifts priorities, for example if they say we need to focus on API security, we can immediately direct the team to relevant modules and upskill in a timely manner. It saves us the time of sourcing and negotiating, making us more agile and effective.

Ben Thal,
Get a full demo with our team
Fill the form to schedule a live product demo and Q&A about our cyber readiness solutions.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The #1 platform to build attack-ready teams and organizations
Maximum curriculum management flexibility, enhanced skills reporting, and engaging gamification features. Book a demo to see Hack The Box in action.
Your plan includes
- ✓ Unmatched content library
- ✓ Workforce development plans
- ✓ Centralized user management
- ✓ Advanced analytics & reporting
- ✓ Source, hire, and retain talent














