Offensive exercises to enable
predictive defensive operations
Break the silos between red & blue teams to ensure enhanced detection,
risk mitigation, and threat-ready incident response plans.



Trusted by 1,000+ cybersecurity teams
Turn threat intelligence into actions
Of ATT&CK and adversary techniques left unmonitored with siloed security teams.
The estimated dwell time (in days) for
attacks without proactive detection.
The possible regulatory fines for missing mandatory threat-led penetration testing.
Threat-informed learning model
Our platform focuses on practical skills development in real-world environments, not theoretical knowledge that doesn't transfer to actual cyber operations.
3x
Faster ramping time
for new hires
90%
MITRE and NIST
coverage in 6 months
50%
Decrease in time
patching CVEs

Threat emulation
Build intelligence-driven exercises and emulate TTPs executed by real adversaries: Scattered Spider, Salt Typhoon, Mustang Panda, or any other APT group.

Continuous skill measurement
Build intelligence-driven exercises and emulate TTPs executed by real adversaries: Scattered Spider, Salt Typhoon, Mustang Panda, or any other APT group.

Team collaboration
Red and blue teams can collaborate in real-time using gamified, live-fire labs, ranges or simulations. Execute, respond, and keep track with real-time telemetry.
How purple teams
use Hack The Box
Training Plans
Chain red team TTP courses with detection engineering labs, guiding analysts from threat intel mapping to automated rule testing while the platform tracks progress real-time.
Ranges
Dedicated purple ranges drop operators into enterprise scale networks where live attacker actions stream into real SIEM/XDR tools and collaborate from attack emulation to OpSec refinement.
Team Assessments
Test and benchmark teams against customized attack chains with automated scoring on both exploitation and detection efficacy, with a post-event report that maps to recommended upskilling programs.
Training Plans
Combine advanced OpSec, custom C2 development and threat intel labs, so practitioners learn to emulate realistic APT campaigns in a safe environment and ensure readiness.
Ranges
Jump into pre-built enterprise networks, actively generating live-fire logs as attacks occur. Simulate attacks with Atomic Red Team and implement predictive measures as real, iterative purple teams do.
Team Assessments
Simulate a realistic cyber attack (ransomware outbreak or insider threat) executed in a sandbox environment. All event data are recorded into the SIEM. The team's task is to detect and respond.
Training Plans
The detection engineering job role path guides analysts through advanced detection workflows and ATT&CK coverage, combined with more than 1,000+ hands-on labs.
Ranges
Enter a cyber range like a real corporate network under attack. Access attacker tools and upon exploiting the targets pivot to the centralized logging. All targets forward security telemetry to the SIEM
Team Assessments
Pre-execute a cyber attack and capture all alerts and logs in a SIEM. The team then enters the scenario with all incident data to experience the intensity of a real incident in a controlled setting.
Training Plans
Chain red team TTP courses with detection engineering labs, guiding analysts from threat intel mapping to automated rule testing while the platform tracks progress real-time.
Ranges
Dedicated purple ranges drop operators into enterprise scale networks where live attacker actions stream into real SIEM/XDR tools and collaborate from attack emulation to OpSec refinement.
Team Assessments
Test and benchmark teams against customized attack chains with automated scoring on both exploitation and detection efficacy, with a post-event report that maps to recommended upskilling programs.
Training Plans
Combine advanced OpSec, custom C2 development and threat intel labs, so practitioners learn to emulate realistic APT campaigns in a safe environment and ensure readiness.
Ranges
Jump into pre-built enterprise networks, actively generating live-fire logs as attacks occur. Simulate attacks with Atomic Red Team and implement predictive measures as real, iterative purple teams do.
Team Assessments
Simulate a realistic cyber attack (ransomware outbreak or insider threat) executed in a sandbox environment. All event data are recorded into the SIEM. The team's task is to detect and respond.
Training Plans
The detection engineering job role path guides analysts through advanced detection workflows and ATT&CK coverage, combined with more than 1,000+ hands-on labs.
Ranges
Enter a cyber range like a real corporate network under attack. Access attacker tools and upon exploiting the targets pivot to the centralized logging. All targets forward security telemetry to the SIEM
Team Assessments
Pre-execute a cyber attack and capture all alerts and logs in a SIEM. The team then enters the scenario with all incident data to experience the intensity of a real incident in a controlled setting.
Data-driven cyber resilience
Measure security team performance with reporting features that
demonstrate skill growth and operational readiness.
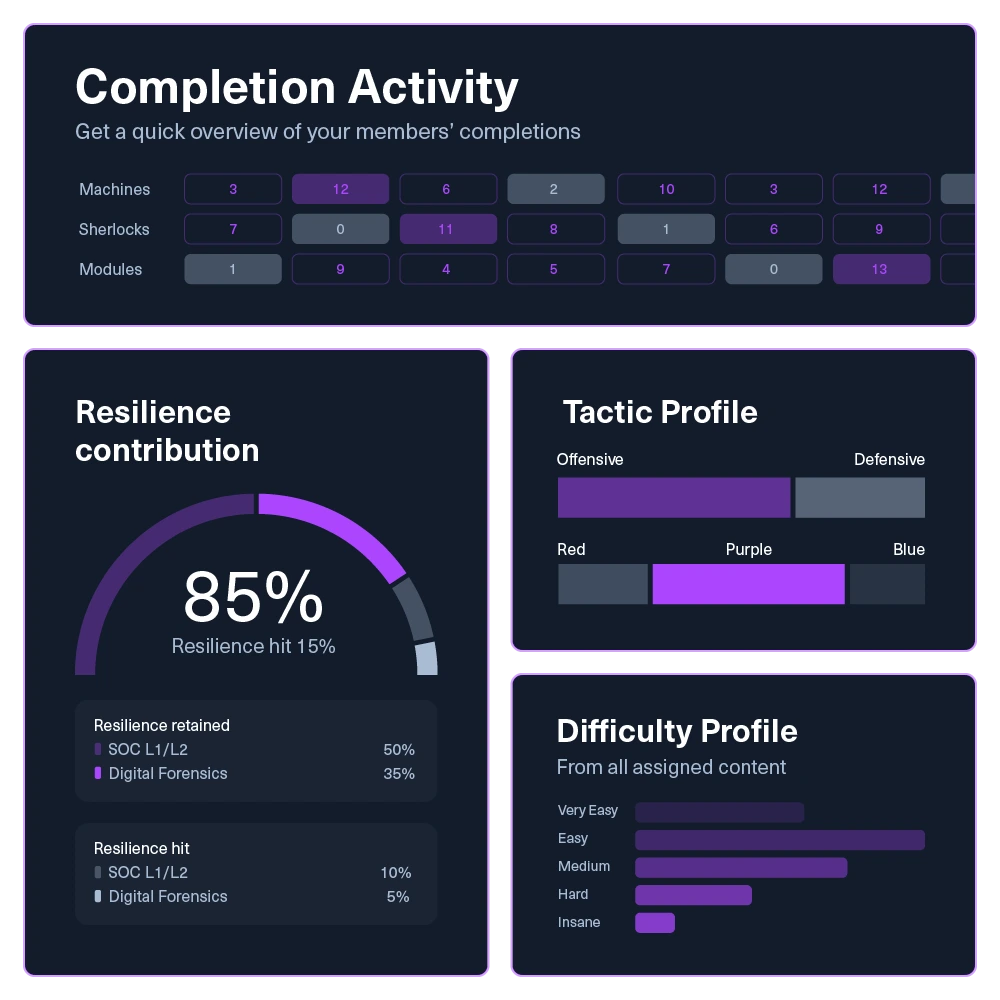
Individual & team analytics
Track key metrics like MTTD, alert precision, and investigation quality at both the individual and team level.
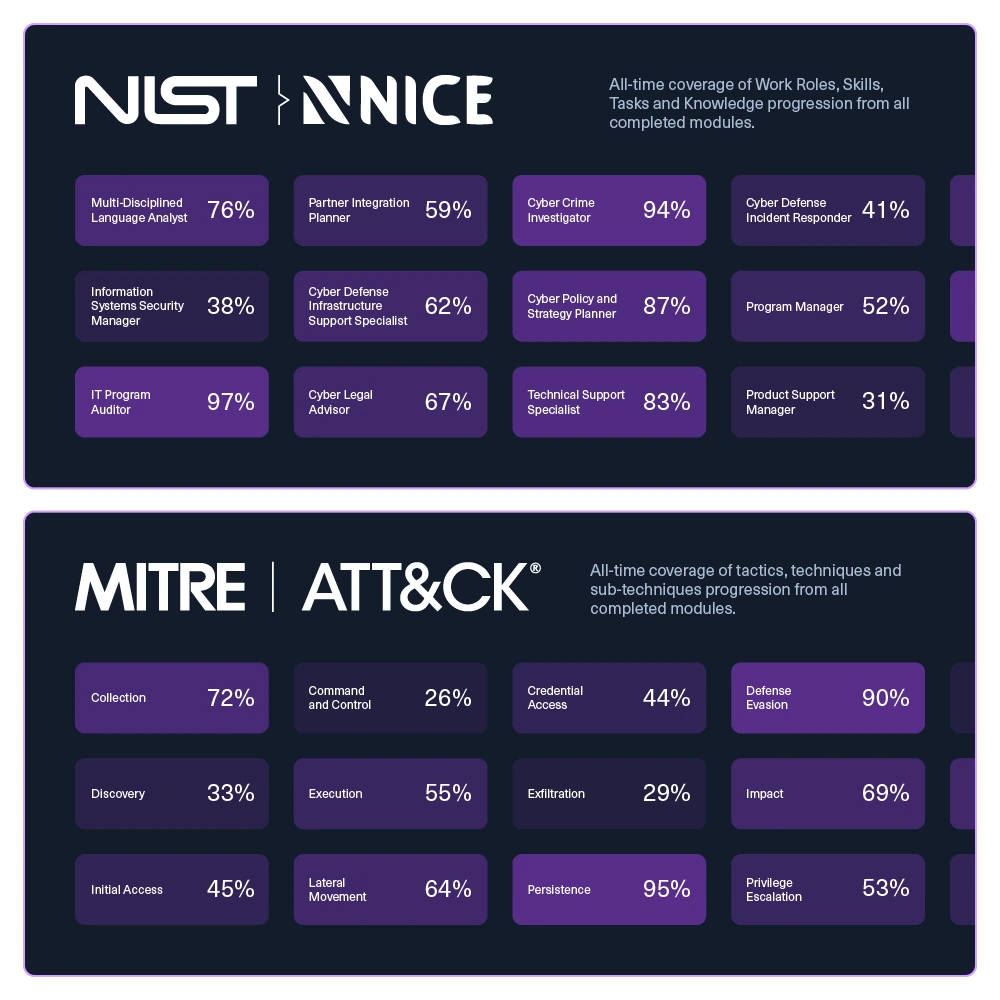
Skill coverage heatmaps
Visualize team proficiency against MITRE ATT&CK and NIST NICE framework to identify capability gaps that need focus.
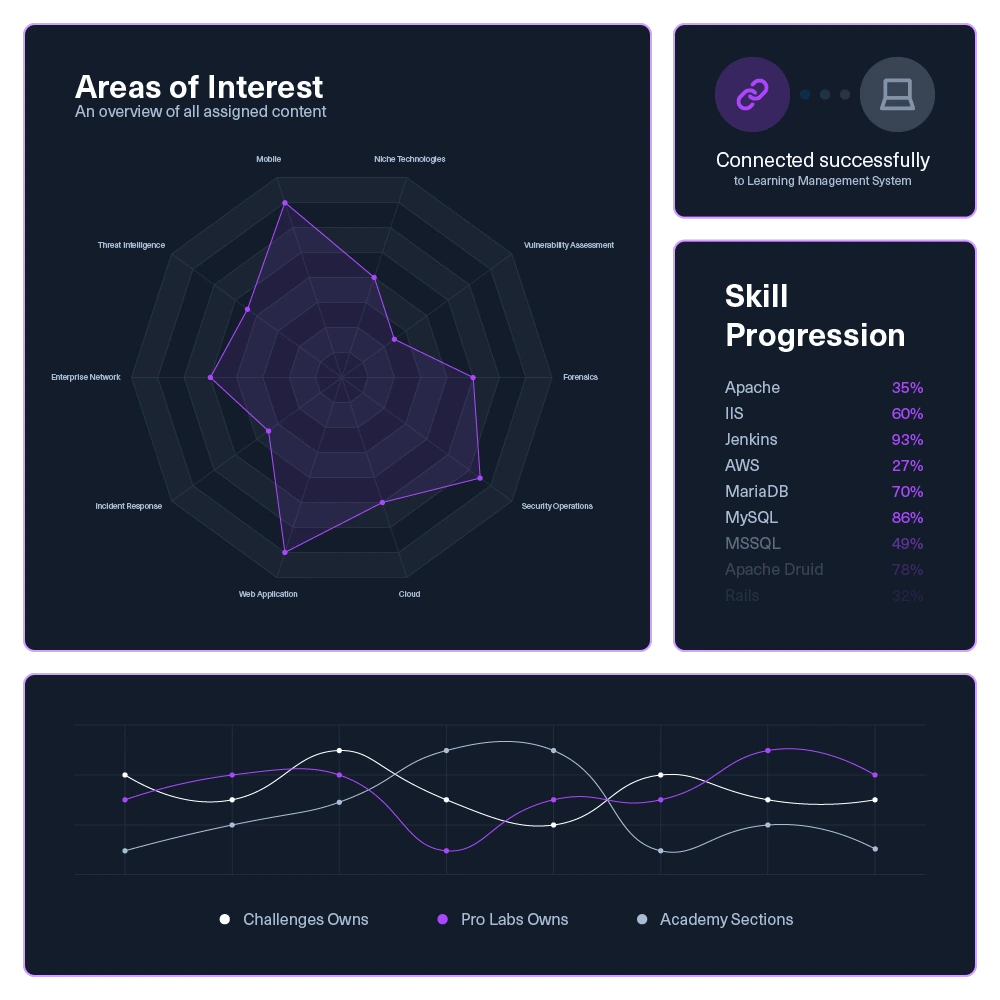
Customization and integration
Export or connect skill metrics and progression to your LMS system to track growth as part career advancement.
How major global organizations
reduce cyber risk
Hands-on purple team labs let newcomers play both attacker and defender in the same scenario, revealing how real-time collaboration slashes blind spots and turns theory into tangible risk reduction.
Enterprise-scale ranges stream live adversary actions into SIEM/EDR dashboards while analysts tune detection rules, creating predictive actions that shrink MTTD and prove collaboration that drives down breach risk.
New regulatory frameworks now require organizations to demonstrate enhanced detection capabilities. Without modern solutions, teams face increasing pressure and diminishing effectiveness. Fully control your team's cyber readiness.

The best defense is a good offensive mindset. Hack The box has enabled our security engineers a deeper understanding on how adversaries work in a real world environment. With HTB, we can learn at your own pace and track progress towards readiness. I've seen the knowledge of exploitation, privilege escalation, and system enumeration grow exponentially.

Richard Kaufmann,
Get a full demo with our team
Fill the form to schedule a live product demo and Q&A about our cyber readiness solutions.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The #1 platform to build attack-ready teams and organizations
Maximum curriculum management flexibility, enhanced skills reporting, and engaging gamification features. Book a demo to see Hack The Box in action.
Your plan includes
- ✓ Unmatched content library
- ✓ Workforce development plans
- ✓ Centralized user management
- ✓ Advanced analytics & reporting
- ✓ Source, hire, and retain talent














