Blue Teaming
How 11,000+ investigators cracked the case in Holmes, HTB’s defensive CTF
HTB’s first all-blue Holmes CTF brought 11,000+ defenders together to tackle DFIR, SOC, malware, and threat hunting challenges in a fully immersive investigation.

JXoaT,
Oct 24
2025
Table of Contents
Great job, detectives! We have wrapped up our first-ever all-blue CTF, and there’s a ton we’d like to share with you about the event. From ideation to bringing the content to your fingertips, this event has been a blast for us, so we hope it was for you, too.
Over the course of the event, players were dropped into Holmes’ home of Cogwork-1, a city hit with a string of cyber incidents begging to be unraveled. From suspicious binaries and compromised infrastructure to traces left by an elusive adversary, every challenge required the same skills blue teams apply in the real world: digging into logs, chasing down leads, and putting the puzzle together under pressure.
What stood out most wasn’t just the technical skill on display, but the creativity in how teams approached problems. Watching investigators bounce ideas off each other, test different angles, and find “aha!” moments was exactly why we wanted to build this.
And the best part: this is only the beginning. So, how did this event come to be?
The defensive engineers who brought you Holmes 2025
They say that the ultimate form of understanding a concept is teaching it. So, what does it say about the people who build entire defensive challenges from the ground up?
Working on Holmes CTF was a great experience for me because I had the opportunity to create content that truly throws our players into a fictional world. Our inclusion of Easter eggs, hidden messages, and the connection to one another did the task of creating an immersive world.
—CyberJunkie, Senior Content Engineer at Hack The Box
We want to take a moment to shine a light on the ones who made this CTF possible. If you learned a single thing from this event, then these are the people you can thank!

Before we dive into the event itself, please check out some insights from the mad lads who brought this investigation through Cogwork1 to life.
Balancing realism vs. playability is a tricky move, especially when we talk about OSINT, CTI, and self-contained platforms. Achille and I worked together to create the most realistic simulated environment possible, using different replicas of real platforms that CTI and OSINT analysts would use in real-life scenarios. The key is to add a little flavor—that’s why the storyline becomes so important in these types of challenges. Also: look Mom, I’m famous!
—Joey, Senior Content Engineer at Hack The Box
11k investigators joined Holmes to solve the case
This event took you—all of you—coming together and showing us you were ready to solve this case. This is just the start for blue-themed CTFs; you all showed us that you're ready to dive deeper into more cases around Cogwork1.

A few words from Idna, the mastermind behind Holmes 2025
Creating defensive content is hard. Very hard. You not only need to be an expert in the forensic side, but you also need your offensive chops to be up to scratch.
The process can look something like:
-
Think of a fun and unique content idea
-
Plan the learning outcomes that you want players to achieve
-
Plan the attack and the forensic fingerprints that you want to leave behind
-
Configure a lab that is vulnerable to the attack and has all of the necessary logging needed
-
Run the attack, leaving the fingerprints you intend to leave, BUT NOT YOUR OWN!
-
Capture the forensic artifacts
-
Write up the questions that you want players to answer
-
Test
-
Make amendments where necessary
-
Test
-
Test a bit more
For Holmes, this was made particularly exciting, as we wanted to ensure that each challenge flowed into the next, often with callbacks and easter eggs that related to the other challenges. We wanted to ensure that timestamps flowed well, and that hostnames, etc, maintained continuity throughout.
The level of detail the team pulled off made the whole event truly immersive, and they created something they should be very proud of.
A message to the participants of Holmes CTF
Thank you all so much for taking part in Hack The Box's first all-blue CTF. You showed up en masse, and the event would have been nothing without the players. I truly hoped you learned something new, and most of all, had fun.
If you're not aware, we release challenges like this called Sherlocks every Thursday, and if you enjoyed this CTF, over 100 Sherlocks are waiting on the platform ready for you to tackle. I'm also looking forward to seeing the write-ups as they get submitted to see how people solved the challenges.
I've already got some ideas brewing for next year, most of which I'd like to keep under my deerstalker for the time being. This case may have been put to bed, but Holmes is ready and waiting for his next case…
The game is (still) on
Holmes CTF may be over, but this doesn’t have to be the end of your investigation. If Holmes taught us anything, it’s that defending against threats isn’t a one-off—it’s an ongoing process of learning, adapting, and sharpening your instincts.
Where should I start if I’m new to defensive content?

If this was your first CTF and you’re looking to dig a bit deeper into defensive content, then look no further than the Junior Cybersecurity Analyst path. This is going to not only give you foundation techniques, but also start you off with an understanding of offensive.
Knowing both sides will give you a deeper understanding of what you’re trying to defend and what you’ll be defending it from.
Want to put your skills into action? Or find out if you have any blind spots? Then we have you covered with Tracks on HTB Labs! Use this as a freeform space to develop questions on subjects you’d like to learn, or a testing ground for what you already know:
If you’re more of a visual learner, be sure to keep up with Learn with Hack The Box, where we cover introductory topics on offensive and defensive security.
Ready to specialize in defensive security?
Now that you’ve been training for a while, it is time for specialization. And a solid place to start is in a SOC!
Getting hands-on inside a SOC (Security Operations Center) is where all the theory clicks into place. It’s the difference between knowing what an alert looks like and actually understanding why it matters in the middle of a live investigation.

The HTB SOC Analyst path was built as that natural next step once you’ve got your security fundamentals down. It drops you into the same workflows defenders use every day, triaging SIEM alerts, digging through Windows event logs, correlating threat intel, and piecing together the story of an attack from scattered traces.
If you’ve started your journey with general IT or blue team basics, this path bridges the gap and helps you develop the operational mindset companies look for in junior analysts. Think of it as your apprenticeship in the SOC, one that gives you the muscle memory and context to step confidently into a defensive role.
Are you and your coworkers looking for a way to tackle today’s threats?
If you and your work team joined Holmes CTF and had a blast tackling incident investigations, it’s time to take that experience even further. We just released HTB’s Threat Range!
A place where you can put those same skills to the test in a live-fire, team-based environment.
You’ll face realistic attack simulations, work together under pressure, and see how your team performs when every second counts. All without the pressure of an incident report or chat with legal about your security policy.
Each Threat Range scenario plays out like a real breach, whether it’s a ransomware outbreak, insider threat, or full-on APT campaign, and gives you measurable results you can actually learn from.
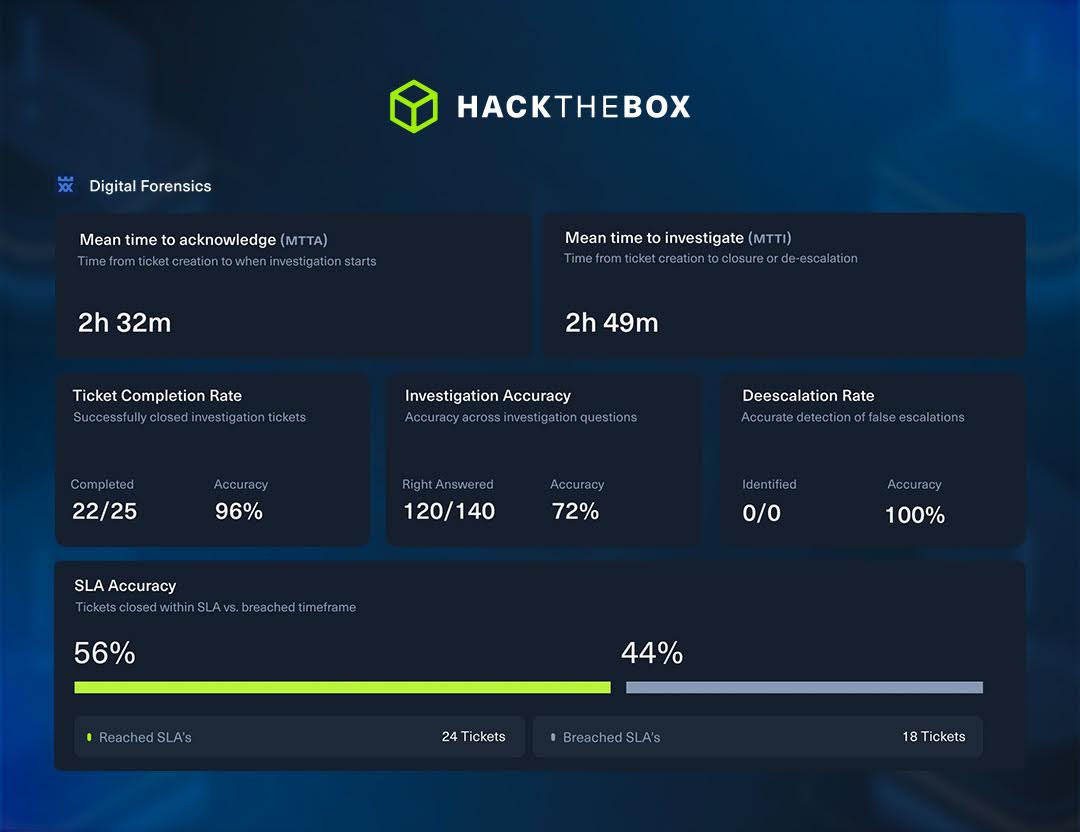
After every run, you’ll get detailed analytics on detection speed, response times, and communication flow, helping you strengthen your processes and sharpen your team’s readiness for whatever comes next.














