Threat Intelligence
Ghost in the PowerShell: APT33’s low-and-slow tactics explained
How the Elfin group made the move from quiet espionage to all-out disruption, and how to stay a few steps ahead of its tactics.

diskordia,
Jul 15
2025
The threat group APT33 (AKA Elfin, HOLMIUM, Peach Sandstorm) has been around since at least 2013, regularly targeting aviation, energy, and government networks across a range of different regions, including the US, Saudi Arabia, and South Korea.
Around mid-2025, several joint advisories and commercial threat bulletins began reporting a sharp uptick in activity from threat groups aligned with APT33, particularly ones against operational technology (OT) and critical infrastructure operators.
APT33’s renewed activity means—you guessed it—another instalment in the Attack Anatomy series. In this piece, we’ll get up close and personal with this well-documented threat group and learn how to prepare for the most likely tactics and techniques defenders can expect in its wake. Let’s jump in.
Who is APT33?

In a nutshell, APT33 combines low-cost access with custom-built malware. Microsoft’s 2024 research on the group’s Tickler backdoor also emphasizes their consistent investment in bespoke tooling, cloud C2, and living-of-theland (LOTL) binaries.
How APT33 breaks in
There are five main techniques defenders should focus on when gearing up against APT33. We’ve mapped them out below:
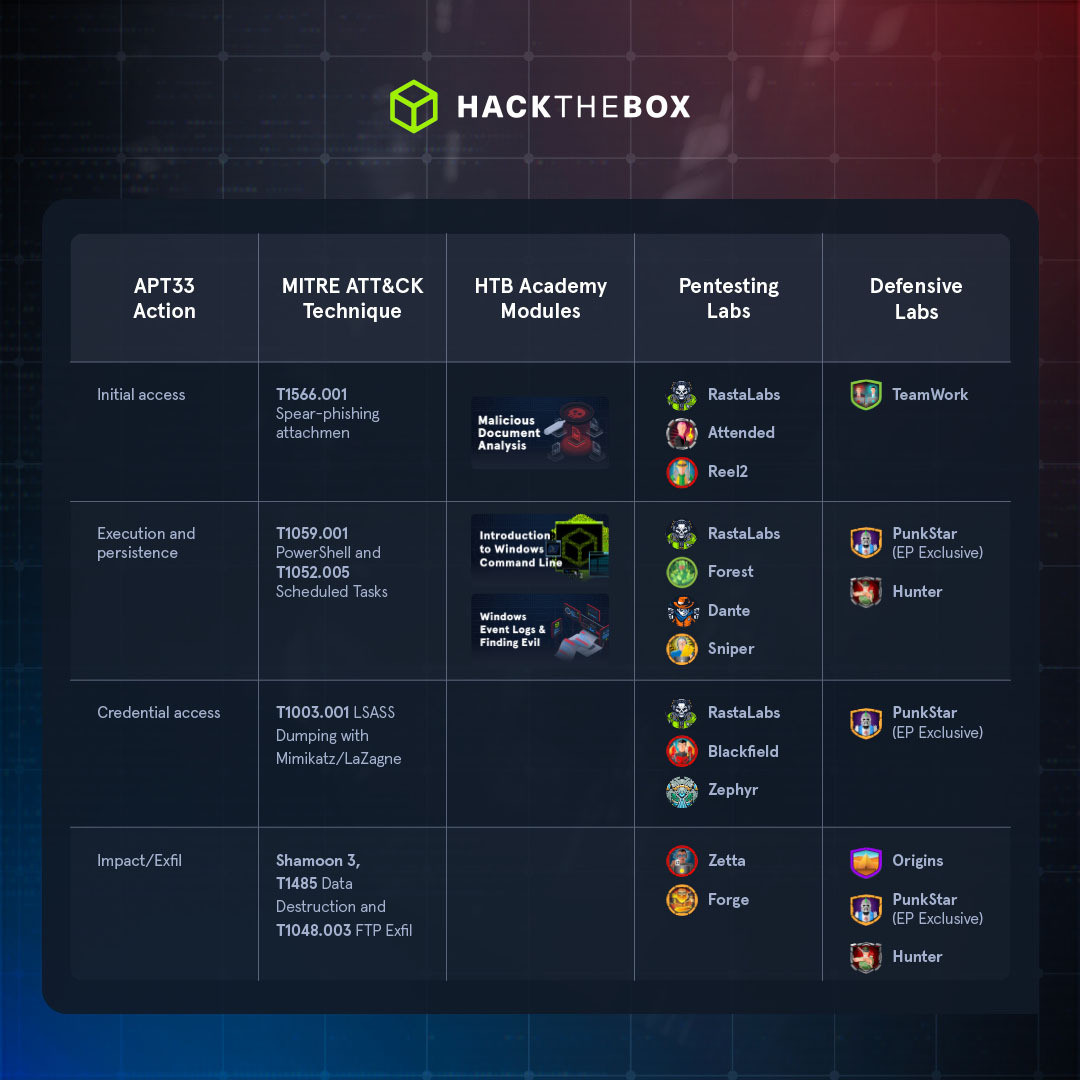
Detection tip: Keep an eye out for outbound HTTP on uncommon posts 808/880 plus base64-encoded payloads—APT33’s go-to C2 pattern.
What to do: Practical strategies to strengthen your defenses
Actions to take right now
-
Roll out and enforce phishing-resistant MFA across IT, OT, and cloud systems.
-
Patch internet-facing assets fast (especially WinRAR, Outlook, and VPN appliances).
-
Segment networks, especially ICS environments; deny outbound 90/808/880 unless explicitly required.
-
Test backups and offline recovery paths monthly.
-
Deploy DDoS protections.
-
Elevate anomaly detection in OT and user behavior.
Strategic tips for long-term resilience
-
Run tabletop exercises simulating wiper or ICS attacks.
-
Subscribe to ISAC threat intel feeds.
-
Update your threat model to reflect Iranian APT TTPs.
Simulation and response: What red and blue teams need to know
APT33’s approach reveals a hybrid adversary model. They have one foot in the world of persistent access, and another in the realm of high-impact, destructive capability; this presents challenges for both red and blue teamers.
For red teams
The lesson here is to mirror the attacker’s mix of techniques. APT33 doesn’t rely on novel zero-days; it hits where it hurts, exploiting weaknesses in authentication, social engineering, and endpoint hygiene.
Truly effective red teaming means simulating realistic entry paths like credential reuse and phish-to-payload delivery.
For blue teams
The message is simple yet urgent: visibility and segmentation have never been so important. Detection engineering should be laser-focused on scripting abuse, command-line logging, and service account monitoring.
And it’s equally crucial that IR teams drill recovery scenarios for the kind of malware employed by APT33, assuming that backups and business continuity will be tested to their limits.
The bottom line is this: APT33’s attack pattern embodies a core truth: today’s cyber threats aren’t just about individual techniques. They're about chaining low-cost actions into high-impact campaigns—low-and-slow. Defenders who stay sharp across the whole kill chain rather than just focusing on prevention will come out on top.
What’s next?
APT33’s tooling and tactics are increasingly modular and may appear in the hands of other actors. Watch for crossover TTPs in OT-targeting campaigns throughout Q3.
Final thoughts: Cyber vigilance, not cyber panic
This isn’t about fear-mongering. It’s about having the skills and discipline in-house to prepare and respond to these threats effectively. That’s what readiness—and resilience—look like.
The intent behind attacks is consistent, and its reach is global. Whether you're a SaaS platform or a utility operator, you might find yourself in the firing line. Your defense doesn’t need to be perfect—it needs to be proactive, resilient, and responsive.
Explore CTEM with Hack The Box
Staying sharp with Hack The Box
If your team hasn’t pressure-tested its response capabilities, there’s no better time.
Recommended HTB resources to get you moving:
-
HTB Enterprise Labs: ICS/OT Scenarios (Alchemy and Professional Labs)
Cyber war is real. It’s here. Don’t just watch the news—train like you’re already in the fight.















