Threat Intelligence
How Volt Typhoon targeted US ISPs with the zero-day Versa exploit
During the Summer of 2024, several internet service providers (ISPs) & managed service providers (MSPs) were the target of a zero-day vulnerability being used by Volt Typhoon.

Howard Poston,
Nov 26
2024
Table of Contents
Volt Typhoon is an advanced persistent threat (APT) group generally believed to be sponsored by the People’s Republic of China (PRC), though their government officially denies this.
Also known as BRONZE SILHOUETTE, Dev-0391, Storm-0391, VANGUARD PANDA, or VOLTZITE, the group was first discovered in the wild in 2021 and specializes in targeting critical infrastructure organizations in the United States.
Several major attacks have been attributed to Volt Typhoon, prompting a joint security advisory by the United States and international cybersecurity authorities in June 2023. Since this report was issued, Volt Typhoon has performed other attacks against US critical infrastructure organizations.
In this Attack Anatomy blog, we’ll dive into the details of an attack campaign targeting internet providers in Summer 2024.
Like our past deep dives into the Cuttlefish malware and Snowflake breach, we’ll be exploring this attack campaign through the lens of MITRE ATT&CK.
We will map each technique used by Volt Typhoon to the corresponding MITRE ATT&CK Technique, and we’ll highlight Hack the Box (HTB) resources that you can use to gain hands-on experience with how these threats work—and how to protect against them.
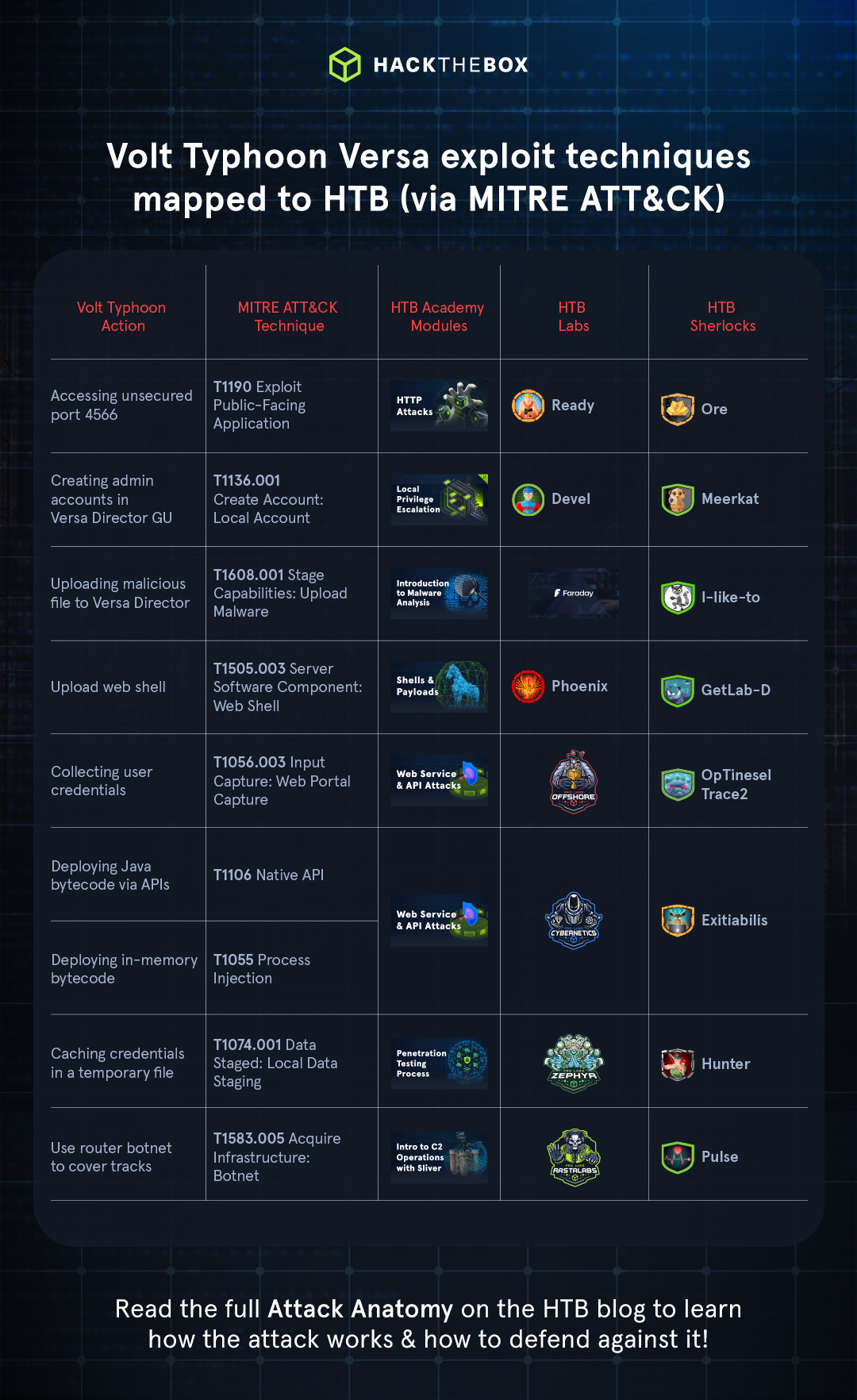
|
Volt Typhoon Action |
MITRE ATT&CK Technique |
HTB Academy Modules |
HTB Labs |
HTB Sherlocks |
|
Accessing unsecured port 4566 |
T1190 Exploit Public-Facing Application |
|||
|
Creating admin accounts in Versa Director GUI |
T1136.001 Create Account: Local Account |
|||
|
Uploading malicious file to Versa Director |
T1608.001 Stage Capabilities: Upload Malware |
|||
|
Upload web shell |
T1505.003 Server Software Component: Web Shell |
|
||
|
Collecting user credentials |
T1056.003 Input Capture: Web Portal Capture |
|||
|
Deploying Java bytecode via APIs |
T1106 Native API |
|||
|
Deploying in-memory bytecode |
T1055 Process Injection |
|||
|
Caching credentials in a temporary file |
T1074.001 Data Staged: Local Data Staging |
|||
|
Use router botnet to cover tracks |
T1583.005 Acquire Infrastructure: Botnet |
Volt Typhoon’s exploit of Versa Director’s platform
In this particular attack campaign, Volt Typhoon exploited a zero-day vulnerability in the Versa Director network management platform. Versa Director was likely targeted by Volt Typhoon because it offers wide-reaching access within a target environment.
The network management platform enables IT staff to centrally administer a distributed network. This same access makes the tool ideal for deploying malware within an organization’s environment.
By exploiting this vulnerability, the APT group was able to upload malware into software users’ environments to act as a stepping stone for future attacks. With this access, the attack group could collect legitimate users’ login credentials or use the compromised web server as a foothold to attack the rest of the organization’s network.
Translate threat intel into stronger security ops

Security teams spend a ton on Cyber Threat Intelligence (CTI) and SIEM tools. Despite the dollars thrown at defensive intel, there's a missing ingredient crucial for maximizing these investments:
Prioritizing and developing the capabilities needed to counter high-priority threats.
Our webinar covers how security leaders can bridge the gap between intelligence and action to elevate your existing security operations. Explore advanced strategies for operationalizing the MITRE ATT&CK framework and using threat intel strategically.
Gaining initial access
The Versa vulnerability exploited by the APT group required admin-level access to the tool’s management graphical user interface (GUI).
Attackers gained access by taking advantage of the fact that some organizations left port 4566—which is used for node pairing between Versa nodes in a high-availability cluster—open to the Internet. (An example of MITRE ATT&CK Exploit Public-Facing Application.)
The group was then able to connect to the exposed ports. They then created an account for themselves with either “Provider-Data-Center-Admin” or “Provider-Data-Center-System-Admin” access (MITRE ATT&CK Create Account: Local Account).
Exploiting the vulnerability
The vulnerability exploited by Volt Typhoon was documented as CVE-2024-39717 and assigned a CVSS v 3.0 score of 7.2 (High). It allows a user to customize the appearance of the Versa Director GUI.
After obtaining the “Provider-Data-Center-Admin” or “Provider-Data-Center-System-Admin” permissions in the previous step, the attacker could exploit an error with the Change Favicon option in the GUI that allowed users to upload malicious files with a .png extension (MITRE ATT&CK Stage Capabilities: Upload Malware).
Volt Typhoon exploited this vulnerability to upload a malicious JAR file that acted as a web shell (MITRE ATT&CK Server Software Component: Web Shell), providing remote access to web servers running vulnerable versions of Versa Director.
Collecting credentials and other threats
The primary goal of the Volt Typhoon attackers was to collect the login credentials of legitimate users.
When users logged into the compromised Versa instance, the uploaded malware would capture their passwords by exploiting Versa’s `setUserPassword` authentication mechanism (MITRE ATT&CK Web Portal Capture) and save them to a temporary file (MITRE ATT&CK Local Data Staging).
The malware also enabled the threat group to send Java bytecode, which could be loaded into memory and executed within a compromised Tomcat webserver (MITRE ATT&CK Process Injection).
They accomplished this using the Java Instrumentation API and Java bytecode manipulation toolkit (MITRE ATT&CK Native API).
The ability to upload and execute bytecode expands the potential malicious applications of the uploaded web shell. For example, using the compromised web server as a foothold, an attacker could scan the rest of the organization’s network for vulnerable machines they could infect to steal sensitive data.
Concealing their presence
Volt Typhoon conceals the source of their attacks using a network of compromised small office/home office (SOHO) devices (MITRE ATT&CK Acquire Infrastructure: Botnet).
Often, these routers and other systems lack the same level of protection and monitoring as enterprise options, making them easier to attack and use as part of malicious botnets.
After the attack, they can use the botnet to scan for vulnerable systems and perform automated attacks, such as the malicious account creation and exploitation of the Versa Director vulnerability.
Since these devices aren’t obviously linked to them, it is more difficult for an investigator to track the attack back to its source.
The attack group also developed a custom malware variant to be used in the Versa attack campaign (MITRE ATT&CK Develop Capabilities: Malware).
At the time of discovery, the malware had zero hits on VirusTotal, indicating that no major antivirus was able to detect its malicious functionality.
The group is also known for “living off the land” by using built-in system utilities to perform malicious actions in an attempt to avoid detection by endpoint detection and response (EDR) solutions.
Prepare for emerging threats with HTB
The MITRE ATT&CK framework is an invaluable resource for learning about various offensive techniques. It describes how an attack technique works, how it can be detected, and the potential means of preventing these attacks.
Volt Typhoon used a wide variety of different techniques in its attack campaigns against critical infrastructure. The specific techniques used in the attack against Versa customers are outlined in the following table, as well as the corresponding HTB resources with related content.
Hack The Box resources complement frameworks MITRE ATT&CK, MITRE D3FEND, and NIST NICE by providing hands-on experience with various techniques.
Instead of just reading about how a technique works, security teams can perform or defend against the attack in a realistic environment. This leads to a deeper understanding and an enhanced ability to manage this threat in their own environments.