Red Teaming
10 practical pentesting tips (from HTB's staff hackers!)
Ready to power up your pentesting skills? Try these pentesting tips gathered from Hack The Box's very own talented team of hackers!

r0adrunn3r,
Jan 25
2023
Table of Contents
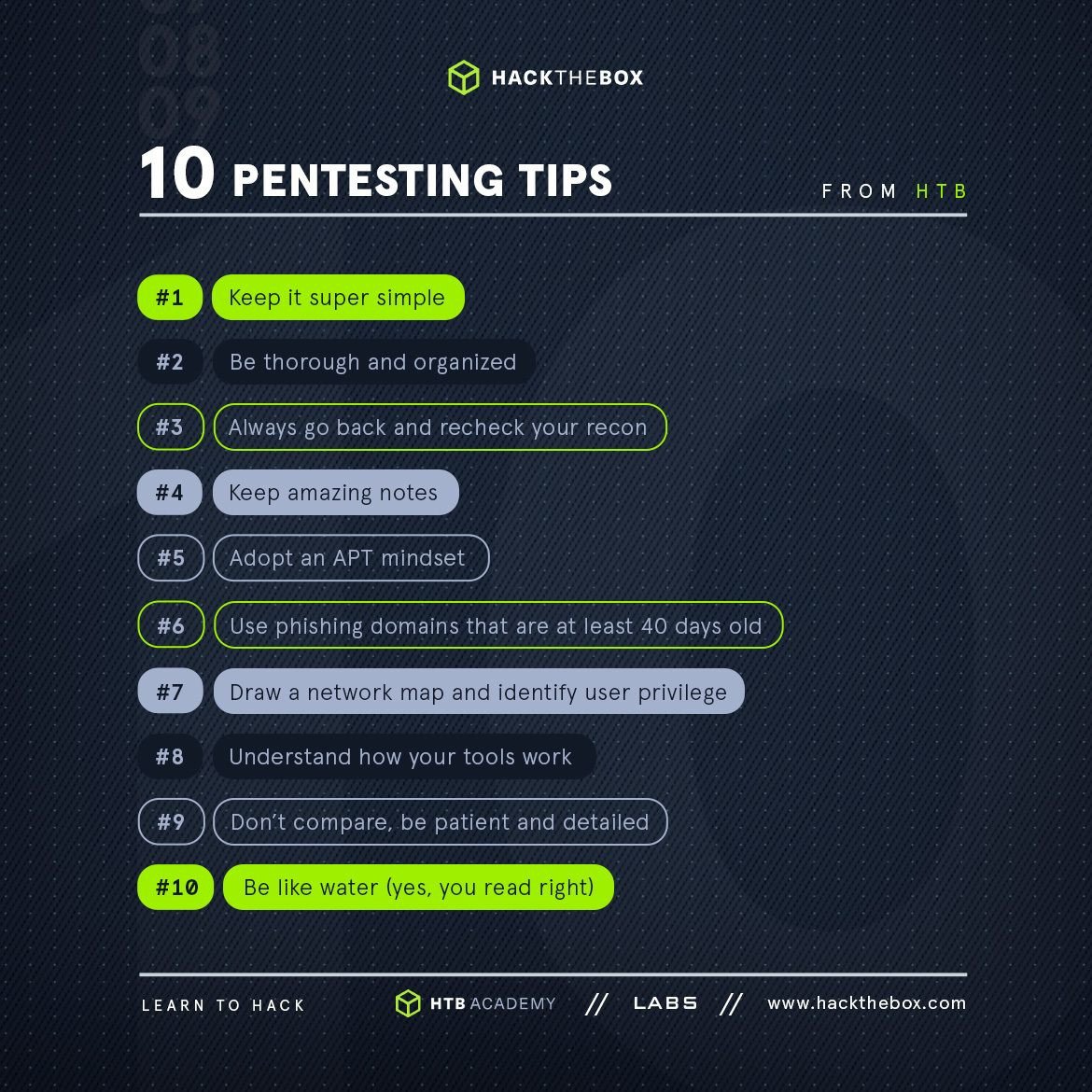
- 1. Keep it simple
- 2. Be thorough and organized
- 3. Always go back and check your reconnaissance
- 4. Keep amazing notes from day 1
- 5. Adopt an APT mindset
- 6. Use phishing domains that are at least 40 days old
- 7. Draw a network map and identify user privilege
- 8. Understand how your tools work
- 9. Don't compare, be patient and detailed
- 10. Be like water
I am a pentester and hacker at heart who has studied computer science, completed a master's in CyberSecurity, and been an active member of Hack The Box (HTB) from the first week it was created (I’ve achieved top place in many CTFs!)
Before joining HTB, I worked as a SysAdmin (one and a half years) and pentester (three years). So I know how challenging learning how to become a pentester can be for both noobs and even seasoned cybersecurity professionals.
But trust me, the journey, experience, and unique competencies you’ll possess are worth it!
While there is no single best path or shortcut to becoming a powerful pentester, you can accelerate your learning by drawing inspiration from experienced cybersecurity professionals.
That’s why I reached out to 10 different professionals from the talented HTB hacking team and asked them to share their favorite penetration testing tips with the community.
TLDR: Everyone has their own journey. Get inspired by all and do what fits best for you to keep your hacking journey fun. Hacking with no excitement is like eating deserts with zero sugar. It still does the job, but you will not enjoy it as much and will end up feeling something is missing.
Enjoy!
1. Keep it simple
@ippsec
Training Lab Architect, infinite years in the field
My tip is to keep it super simple. People often overcomplicate the payloads or exploits they are trying. Taking a step back and simplifying them will usually help identify where something is failing.
If you're trying to get a reverse shell, for example, there are so many places it can fail that are hard to troubleshoot with a reverse shell. Is it the network/firewall? Dirty word filter?
Does the payload have bad characters? An antivirus?
Keeping the payload simpler and trying things like echo, sleep, ping, and reading a file has a greater chance of working. When echo works but ping doesn’t, you'll know you can execute code, but a firewall is blocking outbound connections.
2. Be thorough and organized
@dinosn
Security Consultant, 20 years in the field
Be thorough, document your process, and aim to improve over time. Learn about new technologies and experiment as much as possible on websites like Hack The Box!
3. Always go back and check your reconnaissance
@arkanoid
Head of Content, 18 years in the field
Know that what failed yesterday can succeed tomorrow due to systems and processes changing. That’s why it’s important to recheck your reconnaissance and previous steps to discover a different status of the same infrastructure.
For example, during the reconnaissance phase in a recent penetration testing project, we scanned the target’s entire infrastructure many times, and no vulnerabilities were exposed.
However, as ‘out-of-office’ hours were in the scope of the project, the team later reattempted a full port scan during the weekend which revealed some interesting remote desktop connections exposed on the internet!
Discovering those exposed connections gave us the opportunity to exploit them and get a foothold on the target.
As we discovered later, administrators were enabling remote desktop connections over the weekend to certain servers while bypassing policies and procedures.
4. Keep amazing notes from day 1
@mrb3n
Head of Training Development, 15 years in the field
Pentesting is an iterative process. You will often come across data early on in the pentest that doesn’t seem useful, but note everything from your recon down anyway.
You never know when something that you found on day 1 (that seemed trivial) can actually be chained with another flaw to gain you a foothold or more.
Be organized from the start and note down everything for later. Save your tool output to files, log, and take screenshots. Leave no stone unturned.
5. Adopt an APT mindset
@pzyc0
Delivery Manager, 8 years in the field
Always adopt an APT mindset (Advanced Persistent Threat) when conducting black-box assessments while respecting the rules of engagement. What would you do to avoid detection? Try your best to create minimal noise. Stick to the crown jewels and the intended outcome.
In such engagements, the most crucial step is the initial one, the information-gathering phase.
Leverage open-source intelligence to fully map the external posture, and passive reconnaissance to obtain as many details as possible for the in-scope entities through metadata - i.e., IPs, open ports, versions of services, subdomains, and leaked usernames.
6. Use phishing domains that are at least 40 days old
@DBougioukas
Training Director, 8 years in the field
Use phishing domains that are at least 40 days old during social engineering or red teaming exercises. Older/more mature phishing domains have better chances of bypassing email filtering solutions.
In addition, ensure you appropriately configure SPF, DKIM, and DMARC to further increase your inbox penetration rate.
7. Draw a network map and identify user privilege
@plaintext
Training Developer, 15 years in the field
One of the things that made me fall in love with hacking was the community, the people. I was impressed by the selfless way many people helped me solve a CTF challenge, answer a question about a tool or tell me what method to use to attack a service. So a non-technical tip of mine is to help others, motivate people not to give up, and keep our amazing hacking community alive.
Now let's talk about technical tips. The first tip is about networks. If you identify a scenario where you think you'll need to pivot, it's good to draw a network map. This will provide a helpful visual representation of the components needed to make your pivot work.
The second technical tip is related to identity. Once you get a credential or token from a user, try to understand what that user has access to.
You can create a list of the things you have already identified where you would like to test that new access. The user may not have high privileges, but if it has access to a database, an application, or a local administrator on a computer, it can open the doors to what you need to achieve your goal.
8. Understand how your tools work
@panawesome
CTF Manager, 8 years in the field
It is easy to get lost in the complexity of certain attacks, but a good understanding of the basics can go a long way. Take the time to understand how your tools work.
Proxy the traffic of SqlMap to see what it is being tried. Run Wireshark to see the packets that your LLMNR poisoner is sending out. This will not only give you a better understanding of your attacks but may also reveal why your attempts fail in a given engagement.
9. Don't compare, be patient and detailed
@r0adrunn3r
Community Manager, 6 years in the field
If I would give a pentesting tip to the community or to my younger self it would be: Do not compare, be patient and detailed! Comparing yourself to the best and being a perfectionist can counterintuitively slow down your progress.
Start with small goals and work towards those targets. I am not gonna lie, it takes time. But use that time efficiently and try to have a balance between hacking and fun. Achieving anything needs dedication, but try to learn and enjoy the journey. Because the only way you can excel at something is to love what you’re actually doing, so my tips are to:
Play CTFs as part of your training: There is no such thing as something being too CTFy or not realistic. These days CTFs are not compared with CTFs 10 years ago and HTB and many other communities create these cyber war games with the intention to teach you something new! Whether you solve a challenge or not, the knowledge you gain while investigating it will last forever.
Play the Retired Boxes of HTB strategically and watch Ippsec’s videos: Create a flow of what you want to learn and target to hack the boxes related to your goal. Try to do it blackbox at first. When you cannot go any further review the writeup and understand why there’s a vulnerability, do not just copy-paste the exploit!
In the end, after your victory dance, watch what Ippsec recommends in his videos. He often shows the intended way alongside so many more things that can be life-changing for your career.
Carefully read the exploits you use: Yes, sometimes we are lucky and we can find an exploit or tool working for the target, but if you are not careful or are unsure of what it’s doing you might end up harming the infrastructure and maybe fall out of scope. Plus, understanding what the exploit/tool is doing is part of the studying process!
TAKE NOTES (might seem boring, but it’s a must): Noting how you got a result in Burp or your thought process to succeed in an exploit and the POC is crucial for both the quality of your reports and future guidance and replication. It might take more time and hours from your test, but the people getting the report afterward and your future self will thank you a million times.
10. Be like water
@Bob Theisen
Training Developer, 8 years combined experience in the field & as a college professor
"Be like water" is a philosophy that the legendary Bruce Lee used to teach before he passed on. The idea is centered around water being able to take many different shapes and forms as conditions change and obstacles stand in its way. Practicing this philosophy and mindset in every facet of life can help you improve all-around, especially as a pentester, CTF player, information security professional, and creative problem solver.
The software and IT infrastructure that we test for vulnerabilities are perpetually changing. So be prepared to re-invent your skillset and enter a continuous state of learning. Try to get a feel for where the industry is going so you can be ready to meet the demand before it is here and fully realized by the people and organizations in need of our skills.
For example, if we look at the future of pentesting, what are some technologies you think are going to be used primarily by businesses in the next 5-10 years? One worthy consideration is the migration from on-prem IT infrastructure to hybrid-cloud and even cloud-native (completely in the cloud). What specific technologies should we learn as a result of this migration?
AWS, Azure & how on-prem AD connects to it, GCP, Docker, Kubernete clusters, VMware ESXi just to name a few. Yes, it is true that many organizations are slower moving than others in their migration to new technologies, so you can benefit from knowing the old & new, in other words, having “one foot in the past and one foot in the future.”
Use social media as an educational tool to aid your constant evolution and awareness of new vulnerabilities, tools, defensive tactics, educational materials, and more. When you encounter new topics of study, try to quickly practice them in a home lab and use various challenges on HTB (Academy, Hacking Labs, Pro Labs, and beyond.).
Be like water and keep learning.
We hope you enjoyed the tips from our team of hackers!
It is very important to make sure you are documenting and enjoying every step of your journey. Plus, you are not alone. Join our Discord server (where the heart of the hacking community is beating) to connect with more infosec-curious people like you ❤. Visit the relative channels and ask people their opinion, get advise, and meet professionals from all around the world.
We are the most interactive community for a reason!
If you’re looking to level up your skills, try our practical Penetration Testing Labs or HTB Academy to implement what you’ve learned. OK, now that you know our tips, we want to know yours next. Do you have a personal favorite pentesting tip that is a must and was not included in this compilation? Submit it here and you will get featured in a follow-up blog post: “Favorite Pentesting Tips - Community Edition”.
Keep on rocking!













