Red Teaming
10 OSINT Tools Hackers Need to Know About
Open source intelligence is a vital task for the red team and blue team alike. Here are some of the most useful OSINT tools.

KimCrawley,
Dec 15
2021
OSINT stands for “open source intelligence.” It’s all about finding information you can legally access, through legal means. OSINT is mainly done online, but it can be done offline as well. Pentesters use OSINT to research their targets, and threat intelligence specialists use OSINT to learn about cyber threats. OSINT is an important tool for both the red team and the blue team.
Here are some of the most popular tools for OSINT. You’ll be amazed by all the information that you can find!
Shodan
Shodan is a search engine of discoverable network devices on the internet, such as servers and IoT devices. By discoverable, I mean publicly accessible. It is possible to put a server, IoT peripheral, or networking appliance on the internet and configure it to be relatively private and difficult to fingerprint. But if a device is connected to the internet without careful security configuration, you’ll probably be able to find it through Shodan with the right search query!
Using Shodan without a paid account will return a very limited number of search results. Paid accounts are a lot more useful if the sort of OSINT cyber research that you do requires discovering servers, networking appliances, and IoT peripherals (such as cameras). There are different monthly service fees depending on whether you’re a freelancer, small business, or corporation.
Maltego
Maltego runs as a dedicated application for Windows, Mac, and Linux desktops, which gives users access to a wide array of data sources for the purposes of OSINT, journalism research, and forensics purposes. There are over 58 data sources in Maltego as of this writing, which include Google Maps geocoding, AlienVault OTX, ATII Hades Darkweb Intelligence, Blockchain.info, Crowdstrike, VirusTotal, among many others. I expect the number of data sources integrated into Maltego’s Transform Hub to only grow over time.
The value Maltego provides researchers with is not only in its vast collection of data sources, but also in how its platform can show users patterns and trends in data through highly customizable visualization. Up to a million entities can be plotted in the graphs that Maltego can generate.
Of course, being able to take advantage of all of Maltego’s features isn’t free, although they will let you have a demo before you decide to sign up for a subscription. But if you don’t want to pay for a subscription, the free Maltego Community Edition can still be very useful.
Google Dorks
Google Dorks isn’t its own application. Rather, it’s a technique for using the same Google search engine everyone else on the internet uses everyday. Don’t go looking for an official Google Dorks app, it doesn’t exist! But there are developers who have developed open source software tools for Google Dorking that you can try, such as Pagodo and GoogleDorker.
A typical Google Dorking strategy starts with using simpler search queries and then moves onto more complex queries. Most laypeople only enter strings of words into Google search such as “Toronto weather,” or “Kim Kardashian wedding.” But there are a number of search operators that can be used in Google search that can return more targeted results. For example, you could try “site:hackthebox.com” to search our website specifically, or use quotes around a search term to only return results that use that exact search term. Google provides a list of tips to refine your Google searches here.
A lot of websites are configured very poorly when it comes to cybersecurity. Google’s web crawler bots travel as much of the web as they have access to explore. So Google Dorking can be a technique to find data like email addresses, logins, and financial identifiers which haven’t been properly secured.
Here’s a great video I found from Hak5 to get you started on your Google Dorking journey.
Recon-ng
Recon-ng is an open source web reconnaissance tool. Its power is amplified by the modules you can install with it. If you use Recon-ng effectively, you can save a lot of time in your online OSINT research.
Recon-ng can run from the command line. If you want to make Recon-ng useful for your purposes, choose the Marketplace option from the main menu and explore what’s available. There are a huge number of modules you can try, with more being improved and added all the time.
If you feel comfortable at the command line and you want to make your OSINT work a lot more efficient, Recon-ng may become one of your favorite tools.
Ahmia.fi
Ahmia.fi is a search engine specifically for finding sites on the Tor Network, although the search engine itself is accessible on the “clearnet.” But you will need the Tor Browser in order to open your Tor search results.
A lot of dark web markets and forums are on the Tor Network, so effective use of the Ahmia.fi search engine can be a great tool for your OSINT forensics work.
Wayback Machine
Where do old webpages go to die? The Wayback Machine is a search engine of over 632 billion webpages and growing, many going way back into the 1990s.
Archive.org is using Wayback Machine to archive as much of the web as they possibly can. You can also use their site to manually archive currently online webpages yourself. If and when webpages, websites, and web servers are removed or otherwise go offline, an archived copy may be found through Wayback Machine.
I have personally found archived webpages from 1994 to 2021 through this tool. And what’s really cool is that you can usually use links in the archived webpages to go to archives of those other webpages.
Webpages might be gone, but they’re not forgotten!
theHarvester
theHarvester is another useful open source reconnaissance tool that you can install from GitHub. It can be used to acquire email addresses, hosts, subdomains, employee names, and open internet ports from various public sources such as search engines, PGP key servers, and Shodan. It’s amazing how much useful information people leave online without properly securing it!
When theHarvester is installed, you can easily run the application from your command line. There’s an especially rich set of options to explore data in DNS servers. DNS servers have all kinds of very useful information because they link domain names to specific IP addresses.
Some of my favorite data sources that you can explore with theHarvester include LinkedIn, Bing, Google, and VirusTotal.
TinEye
TinEye is a powerful tool for researching images online. If you have an image on your local device, you can upload it into TinEye and see if and how that image is being used on the web.
An obvious use case would be if you had a photo of someone you don’t know the identity of and you want to find out who they are. But there are many other use cases, such as “where was this photo taken?” or “which application is this a screenshot of?”
Conversely, if you have the URL of an image that’s on the web, you can also conduct research that way.
TinEye is also useful for maintaining your privacy. For example, it’s probably a good idea to protect your children’s privacy. TinEye can alert you to if and when photos of your children are being shared online. There are way more use cases for TinEye than I have room to cover here. As an OSINT researcher, feel free to use your imagination.
OSINT Framework
OSINT Framework is the perfect web application if you aren’t sure which OSINT data sources you’ll need to use to find the information you want. So OSINT Framework presents you with a huge tree of potential data sources that you can explore.
Do you want malicious file analysis, usernames, geolocations, IP addresses, domain names, IRC, the Dark Web, metadata, threat intel, phone numbers, or possibly something else? Keep clicking through the tree until you find the source that you need.
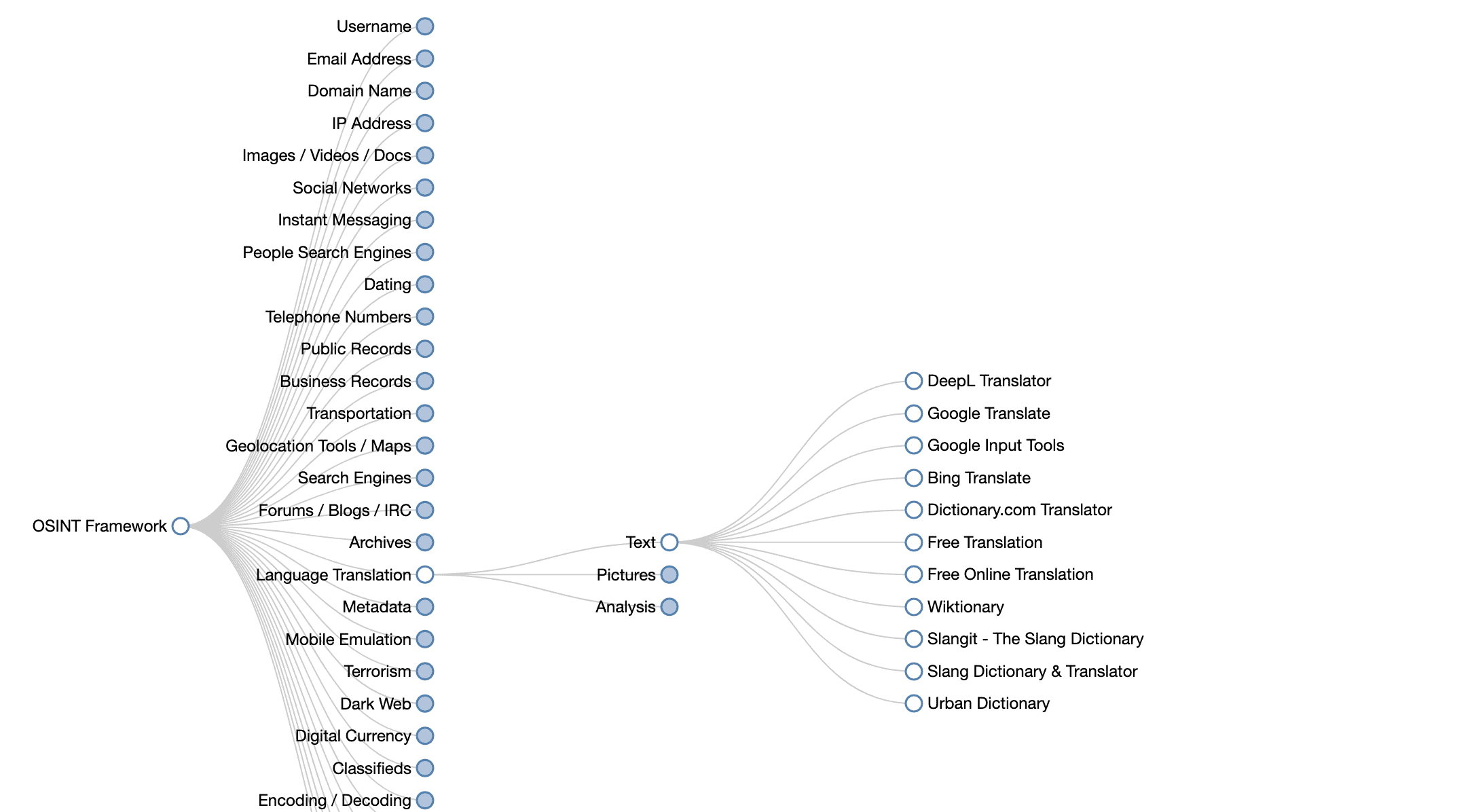
OSINT Framework may be your first step in all of your OSINT work!
Your local library
Not all OSINT is online. The absolute best source of offline data is your local library. You might have to physically go there, or your library’s website may be able to help you find the information you’re looking for directly.
Think of the millions upon millions of books which have never been digitized. The same goes for magazines, newspapers, and old-fashioned data such as Yellow Pages and White Pages phone number directories.
At some libraries, I’ve even found really old maps of places, the way they were in 1900 or earlier.
Your librarian is an offline research expert, and they will gladly help you with your offline OSINT.
OSINT and Hack The Box
Read more about OSINT on our blog. Check out What is OSINT? and Get into OSINT cyber research with HTB Academy.














