Threat Intelligence
Sandworm unleashed: Inside APT44’s Dune-inspired cyber destruction
Explore Sandworm (APT44), the Dune-inspired APT group behind NotPetya, Olympic Destroyer, and power grid attacks — and learn how to defend against their tactics.
Sandworm is an advanced persistent threat (APT) group that specializes in destructive attacks, and is widely believed to be associated with Russia’s General Staff Main Intelligence Directorate (GRU) Main Centre for Special Technologies (GTsST) Unit 74455.
The Sandworm name originated from references in the code to Frank Herbert’s Dune. Also known as FROZENBARENTS, APT44, Voodoo Bear, Telebots, IRIDIUM, Iron Viking, and Seashell Blizzard, the group has been active since at least 2009.
Several major cyberattack campaigns have been attributed to Sandworm, including multiple attacks on the Ukrainian power grid in 2015, 2016, and 2023, as well as the 2017 NotPetya epidemic, and the 2018 Olympic Destroyer attack. A common theme in these and other attacks was a focus on destructive techniques rather than on data theft or financial gain.
Stay one step ahead of threats like Sandworm
The focus in this Attack Anatomy blog is on highlighting some of the main tactics and techniques used by Sandworm in their attacks. To do so, we’ll identify relevant MITRE ATT&CK techniques and map them to related Hack The Box resources.
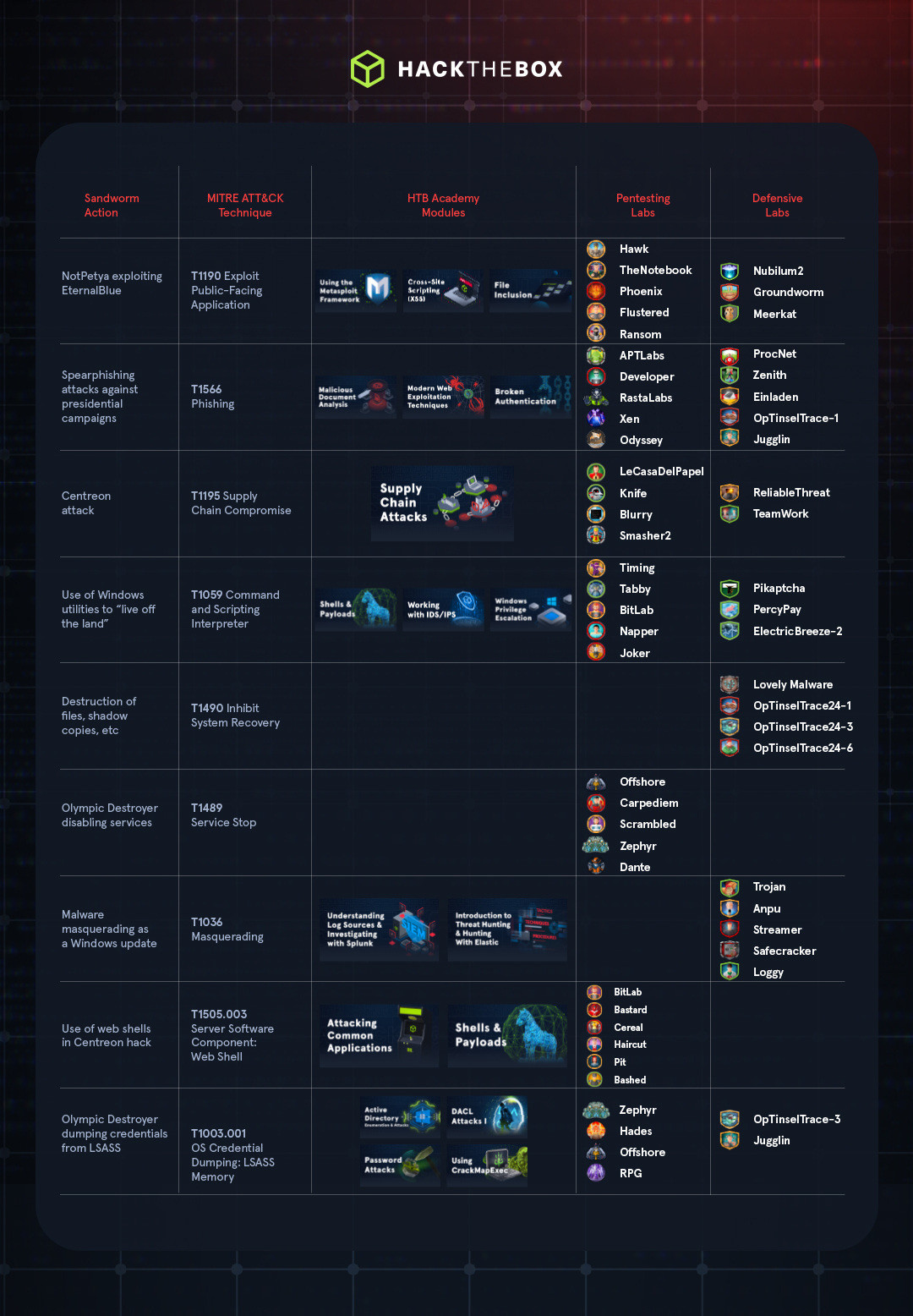
Sandworm’s attack techniques across the kill chain
Sandworm has been active for over a decade and uses a wide variety of tools and techniques, including exploiting documented vulnerabilities, “Living off the Land” techniques, and Masquerading.
Time to explore some of the techniques that the group uses, and identify attack campaigns where they employed them.
Note: While we have a pretty good idea of the techniques and tools that Sandworm has used during their attacks, we are not certain, and not everything has been confirmed by affected parties. So, in this anatomy, we will base our analysis of these techniques on public reporting.
Initial access
The first step in any cyberattack campaign is gaining an initial foothold within a target environment. To accomplish this, Sandworm has performed a mix of both highly targeted and scattershot attacks, and their initial access techniques match this trend. Some of the methods that they’ve allegedly employed include:
-
Vulnerability Exploitation (MITRE ATT&CK Exploit Public-Facing Application): Sandworm was behind the 2017 NotPetya attack in which a wiper malware masqueraded as a ransomware worm. This attack employed the same EternalBlue exploit as WannaCry, which exploited vulnerabilities in the Windows SMB protocol. Another example of this technique is the 2019-2020 attacks exploiting CVE-2019-10149 in EXIM mail servers that attempted to achieve remote code execution (RCE) by embedding malicious commands in the MAIL FROM header of SMTP messages.
-
Spearphishing (ATT&CK Phishing): Spearphishing is a common technique for more targeted attacks, such as ones that leaked emails from the 2016 Clinton (US) and 2017 Macron (France) presidential campaigns and the 2015 attack on the Ukrainian power grid. The use of spearphishing links and attachments was crucial to attributing various attacks to the group. For example, the leaked Macron emails included the original phishing email and a link to infrastructure later associated with the NotPetya attack.
-
Supply Chain Attacks (ATT&CK Supply Chain Compromise): In 2020, reports came out about a Sandworm campaign in which the group had compromised Centreon, a French IT monitoring platform, and had retained access since 2017. The APT group used this as a foothold to access various IT and web hosting providers to collect intelligence
Persistence and defense evasion
Sandworm often performs long-lived attack campaigns, like the multi-year Centreon hack. Accomplishing this requires evading an organization’s cyber defenses and finding ways to restore access after a system restart or file deletion. Some defense evasion and persistence mechanisms allegedly used by the group include:
-
Living off the Land: Sandworm often uses native Windows programs to achieve their goals. By doing so, they reduce the probability that their presence will be detected on the system. For example, the Olympic Destroyer malware used cmd.exe, vssadmin, wbadmin, and bcdedit (ATT&CK Command and Scripting Interpreter) to delete critical files and complicate recovery efforts (ATT&CK: Inhibit System Recovery). Additionally, the malware used the ChangeServiceConfigW API to disable services on the affected system (ATT&CK: Service Stop).
Note: Living off the Land is a strategy that maps to many MITRE Techniques, such as the use of Command and Scripting Interpreters and Native APIs to achieve execution. CISA.gov has more information on how to identify these threats. -
Masquerading (ATT&CK Masquerading): The Sandworm APT also uses malware that pretends to be legitimate software to avoid detection and increase the effectiveness of phishing attacks. For example, a Q1 2023 attack campaign against Ukraine included credential-stealing malware pretending to be Windows updates.
-
Web shells (ATT&CK Server Software Component: Web Shell): A web shell is malware installed on a web server that allows the attacker to connect over the Internet and execute commands on the host system. Sandworm has been known to use webshells for remote access and persistence, including in the Centreon hack.
Privilege escalation and lateral movement
Once inside an organization’s network, Sandworm often needs to move laterally from its initial access point to high-value targets where it can deploy wiper capabilities for maximum impact. Some techniques they have allegedly used to accomplish this include:
-
Credential Theft: Sandworm frequently uses and steals user credentials as part of their attacks. In the 2018 attack on the Winter Olympics in South Korea, the APT group deployed the Olympic Destroyer malware, which dumped credentials from LSASS (ATT&CK OS Credential Dumping: LSASS Memory) and victims’ browsers (ATT&CK Credentials from Password Stores: Credentials from Web Browsers). These credentials could then be used to expand the attacker’s access or elevate privileges.
-
Vulnerability Exploitation: Some Sandworm malware exploits vulnerabilities to gain initial access to a target environment, and uses the same methods to spread through the network. For example, NotPetya used the EternalBlue and EternalRomance exploits for SMBv1 to infect new systems within a network (ATT&CK Exploitation of Remote Services).
-
Use of Legitimate Tools: Sandworm also used legitimate Windows tools to expand their access to a target environment. For example, in addition to exploiting SMB vulnerabilities, NotPetya also used WMI (ATT&CK Windows Management Instrumentation) and PsExec (ATT&CK System Services: Service Execution) to help it access and infect other systems within an organization’s network.
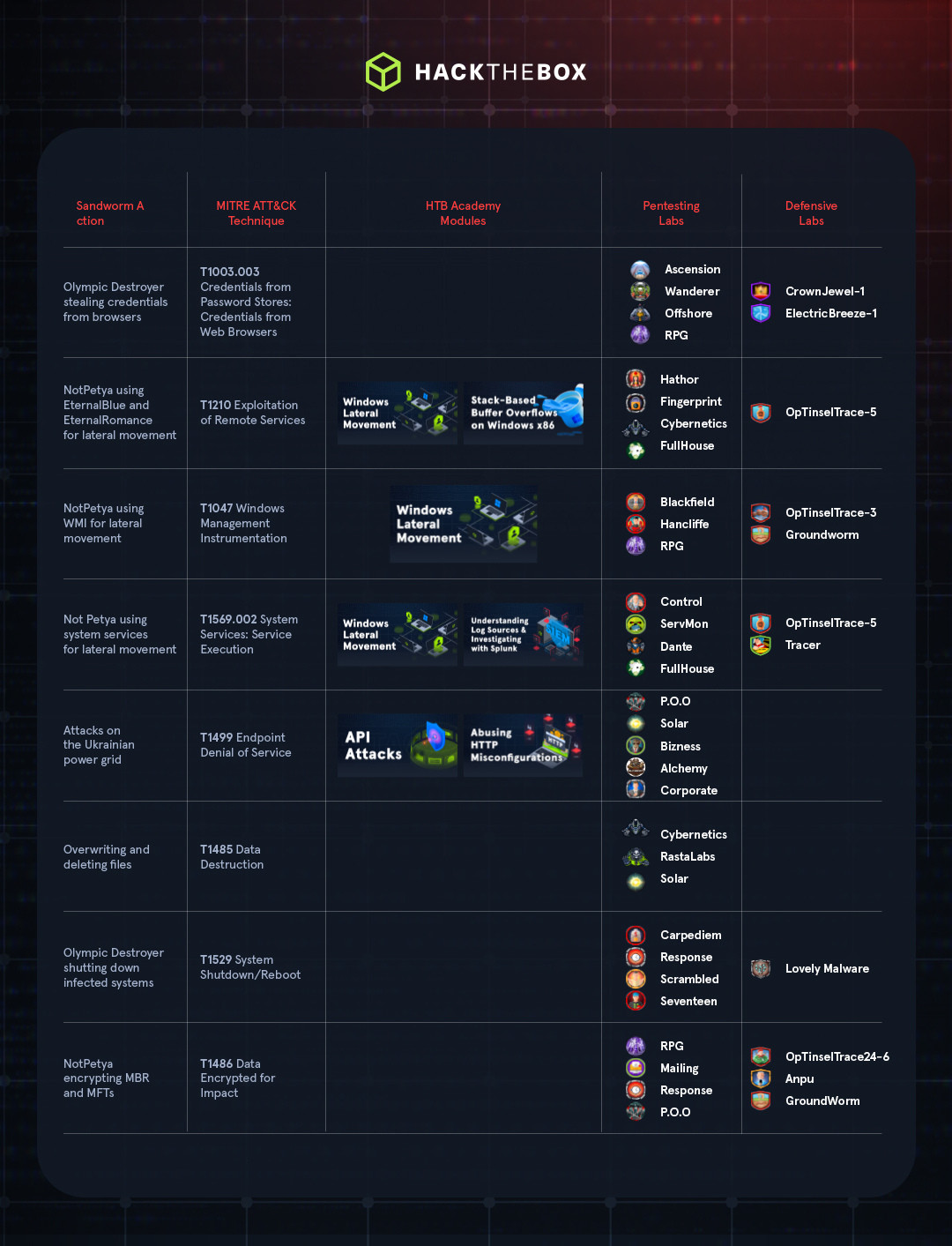
Impact
The majority of major Sandworm attacks have involved destructive malware designed to cause disruption in their targets. On multiple occasions, the group has targeted the Ukrainian power grid with BlackEnergy3 and other wiper malware (ATT&CK Endpoint Denial of Service). In the 2015 attack, the incident caused 30 substations to shut down and caused power outages for an estimated 230,000 people lasting up to six hours.
The Olympic Destroyer malware also deleted critical files, disabled services, overwrote files (ATT&CK Data Destruction), and shut down affected systems (ATT&CK System Shutdown/Reboot). This caused disruption during the opening ceremonies to the event’s Wi-Fi network, news coverage, and the official smartphone app.
NotPetya was another destructive cyberattack pretending to be something else. The NotPetya malware was a wiper that destroyed the Master File Table (MFT) and Master Boot Record (MBR) on a computer (ATT&CK Data Encrypted for Impact). While the malware presented a fake ransom note — pretending to be the Petya ransomware — this rendered the files completely unrecoverable. This attack has been called “the worst cyberattack in history” and caused an estimated $10 billion in damage.
However, while destruction is often Sandworm’s primary MO, it’s not always the only goal of their attacks. Some other objectives have included:
-
Intelligence collection: The supply chain attack targeting Centreon didn’t include a destructive component. For this reason, some analysts believe that the multi-year campaign was an intelligence-gathering mission.
-
Propaganda: Several accounts on social media sites, such as Telegram, are associated with Sandworm. These are designed to spread pro-Russia narratives and misinformation about Ukraine and the United States.
Manage destructive cyber threats with HTB
Sandworm is a well-established state-sponsored hacking group that has had ample time to develop and refine its tactics. While the techniques described here are some of the more common and significant ones used by Sandworm, this post is far from a comprehensive list.
When working to defend your organization’s systems against an APT group, there’s no substitute for hands-on experience with their tools and techniques. Hack The Box also has a bunch of resources like Threat Range where you can stay on top of the techniques used by groups like Sandworm.
By exploring these, security teams can gain a fuller understanding of how various threats work, and enhance their ability to detect and defend against them.















