Career Stories
5 cybersecurity career paths: A roadmap to your first role
Discover the cybersecurity career paths for entry-level candidates and complete beginners. Your cybersecurity career journey starts here!

g4rg4m3l,
May 10
2024

Table of Contents
You don't need to read typical AI-generated text to tell us the importance of cybersecurity “in today's ever-evolving digital landscape” (see what we did there?).
As a result, there is a high demand for professionals to fill specialized roles in cybersecurity, each requiring a particular set of skills (read with Liam Neeson's voice).
While penetration testing may be the first thing that comes to mind when you think of cybersecurity, it’s not all about hacking—there are strategic cybersecurity positions, defensive roles, and so much more.
To help you make an informed decision, let's explore five of the most popular cybersecurity career paths.
1. Cyber defense & analysis

Working within a security operations center (SOC), a cybersecurity analyst is responsible for defending an organization’s network. This means identifying threats and protecting systems against cyber attacks that involve unauthorized access, data theft, and disruptions to normal business operations.
An analyst's career path can take many directions and provide ample opportunities for success in the field. Often considered to be a good path for those new to the field even without any prior experience.
💡Recommended read: how to start a career in cybersecurity with no experience.
Jobs along this career path
|
Job title |
Description |
|
Cybersecurity consultants |
Consultants make recommendations to improve the overall security posture of an organization, generally guiding and supervising the implementation process. |
|
SOC analyst |
SOC analysts (or information security analysts) specialize in monitoring systems 24/7. They scan for suspicious activity, potential threats, or security breaches, taking action if something out of the ordinary occurs. |
|
Threat intelligence analyst |
Threat intelligence analysts identify vulnerabilities and potential threats. They track adversarial activities to keep up to date with the latest techniques and procedures cybercriminals develop to target a particular industry. |
This path is for you if:
-
You think the devil's in the details (and you'll find it.)
-
You have a strong logic and analytic sense.
-
You have a natural talent for correlating information.
-
You’re a problem solver.
Skills to develop:
-
Cybersecurity fundamentals.
-
Knowledge of security protocols.
-
Log analysis.
-
Malware analysis.
-
Communication skills.
-
Threat hunting.
Entry requirements & common certifications
The analyst path is usually recommended as the first step into a cybersecurity career. Typically cybersecurity analysts will begin by carrying out routine tasks while working alongside experienced professionals dealing with cyber threats. This provides real-world experience and growth opportunities.
If you're coming from an IT or non-IT background this might be a good place to start, as Sabastian Hague (sebh24) Defensive Content Lead, Hack The Box, shares in his blog post on how to become a cybersecurity analyst:
It is important to have a solid foundation of IT concepts. This can be done by taking online courses or attending workshops on topics like networking, system administration, or even some cybersecurity fundamentals (I would recommend saving this until you’ve covered the IT basics, though!).
Recommended training and certifications:
-
CompTIA's Security+: A great foundational certification can teach basic skillsets for an analyst career.
-
CompTIA’s Cybersecurity Analyst (CySA): Amore advanced certification focusing on specific analyst skills.
-
Certified Defensive Security Analyst (HTB CDSA): A comprehensive, industry-relevant, practical certification approach.
-
HTB’s SOC Analyst Job-Role Path: Will equip you with the skills and experience to perform security analysis and SOC operations, helping you stand out in the job market.
Get certified as HTB Certified Defensive Security Analyst

-
For those who want to enter the defensive security world with little to no prior experience.
-
Cover entry to intermediate-level SOC operations, detection, and incident handling concepts.
-
Learn how to spot security incidents and identify avenues of detection that may not be immediately apparent from simply looking at the available data/evidence.
💡Related read: How to become a cybersecurity analyst.
2. Ethical hacking & testing systems
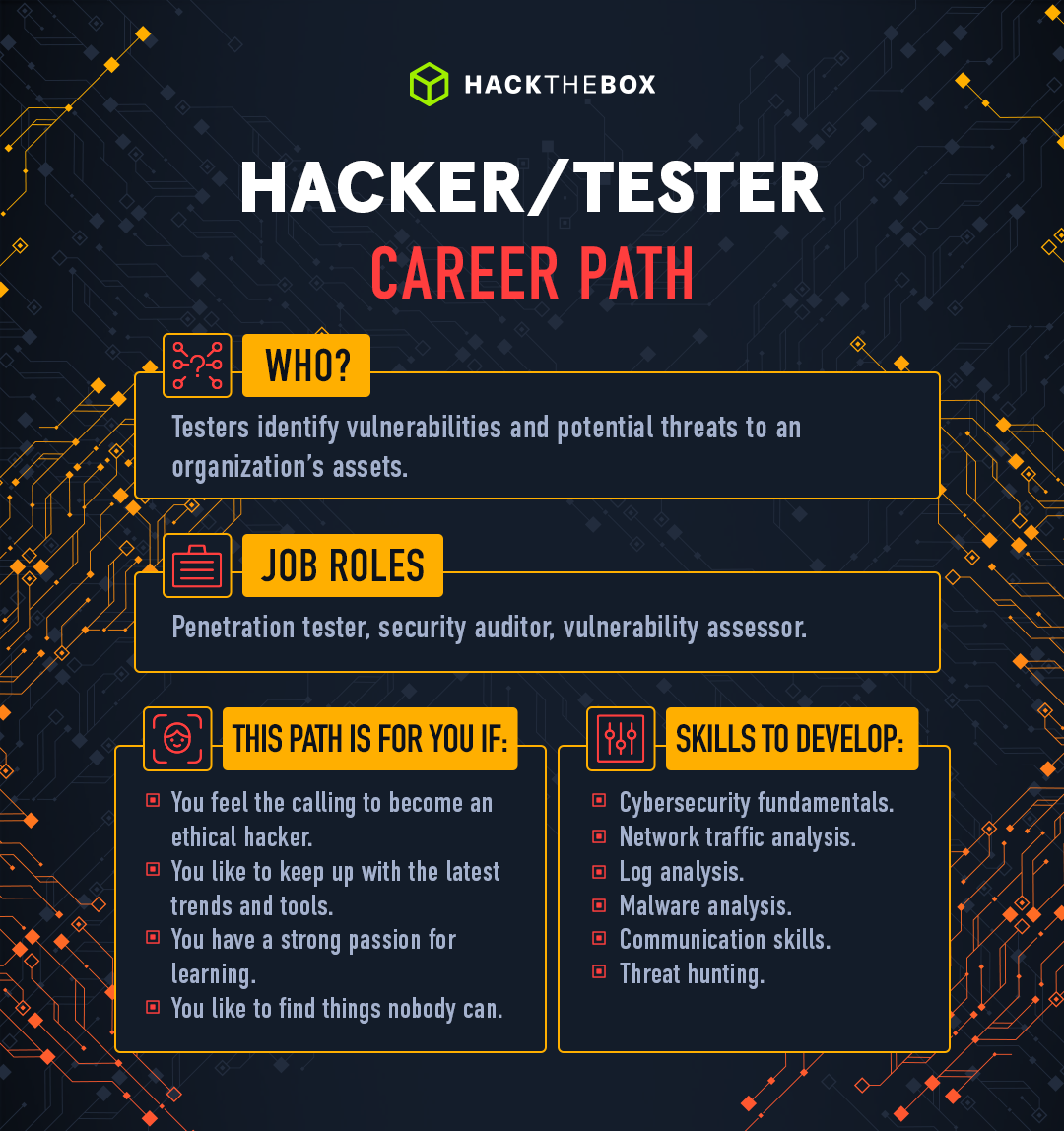
When talking about testing as a cybersecurity career, we refer to tasks that evaluate the security of computer systems, digital assets, and networks. Testers are responsible for identifying security gaps and weaknesses before the criminals do.
They identify vulnerabilities and potential threats to an organization’s assets. This could involve testing network security, system access management, and application functionality, among other things.
This path is related to the popular term "ethical hacker" or "red teamer." Where cybersecurity professionals simulate real-world attacks on digital assets to identify vulnerabilities from the attacker's perspective.
Jobs along this career path
|
Job title |
Description |
|
Penetration tester |
Penetration testers use the same techniques and procedures as cybercriminals to identify vulnerabilities before they do. This is where "ethical hackers" shine. |
|
Security auditor |
Security auditors are responsible for reviewing an organization's security systems to determine if they align with industry standards and regulations while identifying potential weaknesses. |
|
Vulnerability assessor |
Vulnerability assessors conduct tests to identify and categorize weaknesses in an organization based on their severity. This information helps organizations prioritize which vulnerabilities to mitigate first. |
This path is for you if you:
-
You live by Sun Tzu's motto "Know the enemy and know yourself in a hundred battles you will never be in peril".
-
You feel the calling to become an ethical hacker.
-
You like to keep up with the latest trends and tools.
-
You have a strong passion for learning.
-
You like to find things nobody can.
Skills to develop:
-
Proficiency with penetration testing methodologies, tools, and techniques.
-
Strong operating systems and computer network knowledge.
-
Scripting and programming concepts.
-
Familiarity with the latest vulnerabilities, techniques, and trends.
-
Outside-the-box thinking and problem-solving.
Entry requirements & common certifications
Becoming a tester requires dedication and structured learning. You must put your knowledge into proven practice, theory alone isn’t enough.
Learning platforms such as Hack The Box (HTB) provide hands-on training that is highly regarded in the industry.
💡Recommended read: An (aspiring hacker’s) web application penetration testing guide for 2024.
Recommended training and certifications:
-
HTB’s Penetration Tester job role path: Provides a structured approach to transition to the field, with or without prior experience.
-
Hack The Box Certified Penetration Testing Specialist (CPTS): A theoretical and practical certification that equips you with the knowledge and experience to perform penetration testing activities in the real world.
-
CompTIA PenTest+: An industry-recognized certification with practical experience for beginner pentesters.
💡Top tip: You should always prioritize certifications that focus on practical skills.
Get certified as HTB Certified Penetration Testing Specialist

-
For those who want to enter the penetration testing world with little to no prior experience.
-
Cover entry to intermediate-level security assessment and penetration testing concepts.
-
Learn to spot security issues and identify avenues of exploitation.
3. Governance and risk management

Cybersecurity specialists in governance, risk, and compliance (GRC) ensure that organizations follow the best security practices and comply with international laws and regulations by planning and overseeing regular risk and vulnerability audits.
A career in cybersecurity governance and risk management involves taking care of an organization's overall security strategy. This includes planning cybersecurity policies, ensuring implementation, and evaluating effectiveness.
Jobs along this career path
|
Job title |
Description |
|
Cyber risk analyst |
Cyber risk analysts evaluate and classify potential risks that target an organization. They provide security recommendations based on these assessments. |
|
Cybersecurity compliance consultant |
Compliance consultants are responsible for ensuring organizations align with industry-specific security standards and practices. |
|
Chief information security officer (CISO) |
A CISO is a senior-level executive job role. The CISO oversees the entire organization's security posture and overall strategy. |
This path is for you if:
-
You're a natural leader.
-
You have a strong sense of responsibility.
-
You love to plan and strategize.
-
Your favorite board game is Risk.
-
Your favorite TV show is Law and Order.
Skills to develop:
-
Organizational business processes and operations.
-
Knowledge of cybersecurity laws, standards, and regulations like GDPR, PCI DSS, and ISO 27001.
-
Risk management.
-
Project management.
-
Communication skills.
Entry requirements & common certifications
Cybersecurity core concepts and frameworks are fundamental to governance and risk management roles. You must be able to relate them to a structured cybersecurity strategy that aligns with industry regulations.
GRC is more than just check-the-box compliance. It's about identifying ways that the business can achieve its goals while meeting privacy and security goals.
Howard Poston, CISO, Qorra.
A typical entry-level job is a junior cybersecurity compliance consultant. It's common to see professionals from auditing job roles related to different areas, such as IT auditing, transition to cybersecurity GRC.
While it's not mandatory to have a formal degree to follow a governance and risk management path, it can be beneficial to speed up your career. Having a degree in IT and getting industry-credible certifications can make for a solid foundation.
Common GRC certifications include:
-
Certified in Governance.
-
Risk and Compliance (CGRC).
-
Certified Information Systems Auditor (CISA).
-
Certified in Risk and Information Systems Control (CRISC).
-
Certified in Risk and Information Systems Control (CISSP).
4. Incident response & digital forensics

In the field of cybersecurity, it is not a question of if an incident will happen, but rather when it occurs.
Jobs related to incident response involve preparing for cybersecurity incidents and jumping to action as soon as they happen.
Security professionals in this area develop detailed security protocols that outline procedures and assign responsibilities for handling unexpected situations.
They may even conduct forensic investigations to identify the source and nature of incidents. If it comes to that, they work closely with law enforcement to gather evidence, making sure it's admissible in court. Elementary, my dear Watson.
💡Recommended read: A step-by-step guide to writing incident response reports (free template inside).
Jobs along this career path
|
Job title |
Description |
|
Incident responder |
Incident responders are responsible for identifying, responding to, and mitigating security incidents to limit damage and reduce recovery time. |
|
Forensic analyst |
Forensic analysts focus on investigating cyber attacks to determine and gather evidence of when they happened, how they happened, and who was responsible. |
This path is for you if:
-
You work well under pressure.
-
You love to plan and keep yourself organized.
-
You're a problem solver.
-
You love teamwork.
-
You like to cosplay Sherlock Holmes (meaning you love to solve mysteries.)
Skills to develop:
-
Soft skills like communication, collaboration, and working well under pressure.
-
Fundamental computer and computer network concepts.
-
Solid understanding of cybersecurity concepts, frameworks, and methodologies.
-
Proficiency in incident responder and forensic tools like Endpoint detection and response (EDR), Intrusion Prevention Systems (IPS), Intrusion detection systems (IDR), and Security Orchestration and response tools (SOAR.)
Entry requirements & common certifications
To start a career in incident response, you must possess strong technical foundations and keep up with the latest attack techniques.
If you come from a technical or IT background, we recommend learning cybersecurity basics and becoming proficient in field-specific tools and methodologies like the NIST Incident Response Framework.
With no IT background, consider getting hands-on experience while learning foundational concepts. Working in an entry-level IT job such as a help desk or IT technician might be a speedy way to make a career change to an incident responder.
While some employers may prefer formal educational training, like a computer engineering or cybersecurity degree, this is not mandatory.
Recommended training and certifications:
-
CompTIA's Security+.
-
GIAC Certified Incident Handler (GCIH) or Certified Computer Forensics Examiner (CCFE).
💡Take a comprehensive approach to incident handling by checking out the Incident Handling Process module on Hack the Box (HTB) Academy.
5. Cybersecurity engineering & operations
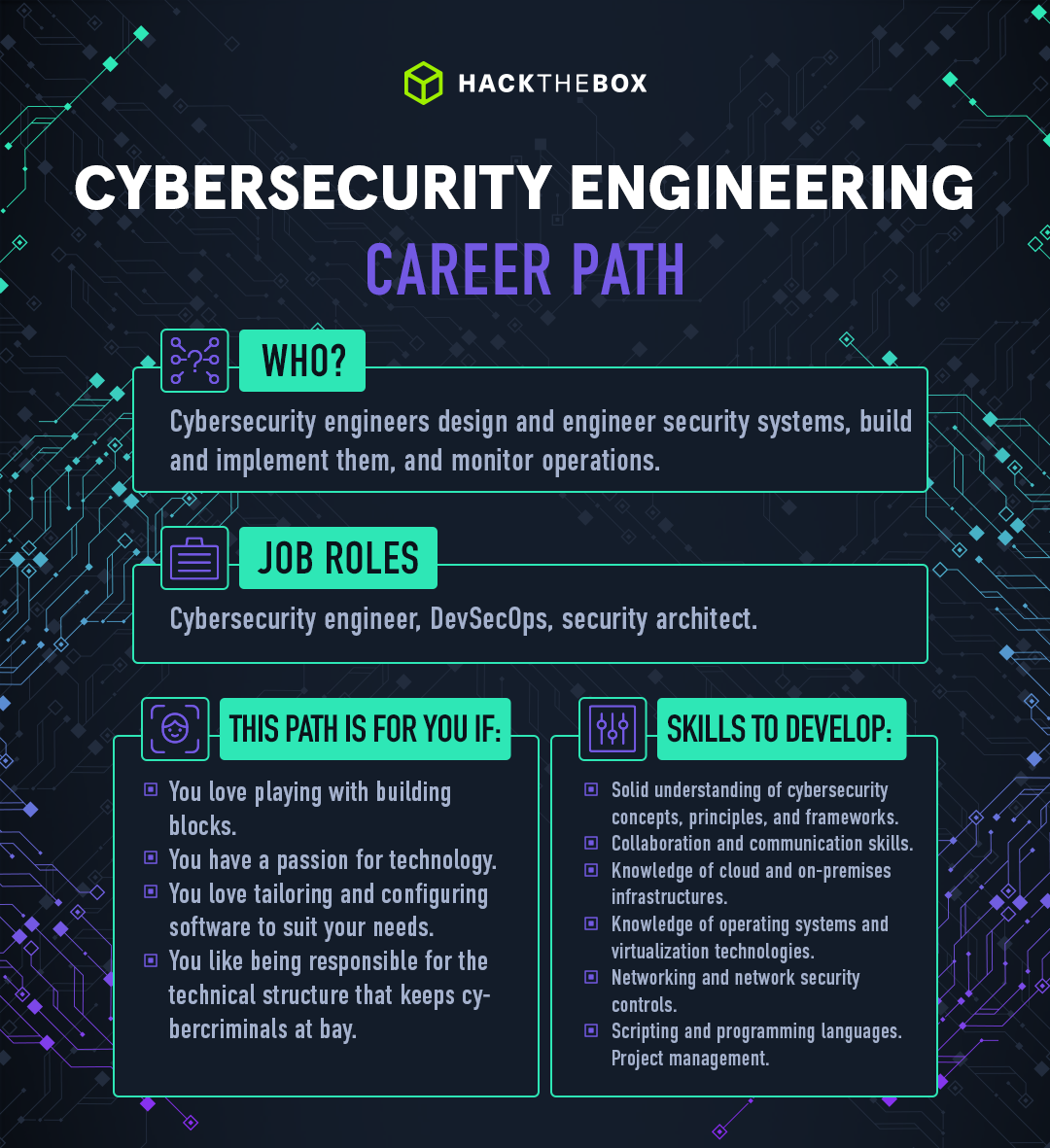
Cybersecurity engineers make sure the cybersecurity machine is up and running.
They design and engineer security systems, build and implement them, and monitor operations to ensure they align with the strategic security posture of the organization.
Jobs along this career path
|
Job title |
Description |
|
Cybersecurity engineer |
Engineers are responsible for designing and implementing security solutions—the infrastructure to defend from cyber attacks. |
|
DevSecOps |
DevSecOps ensures secure software development. Using several methods and automated tools they verify that code follows security best practices during the creation and deployment of software. |
|
Security Architect |
Architects are in a more senior position than cybersecurity engineers because a security architect sets the blueprint for engineers to work on. |
This path is for you if:
-
You love playing with building blocks.
-
You have a passion for technology.
-
You love tailoring and configuring software to suit your needs.
-
You like being responsible for the technical structure that keeps cybercriminals at bay.
Skills to develop:
-
Solid understanding of cybersecurity concepts, principles, and frameworks.
-
Collaboration and communication skills.
-
Knowledge of cloud and on-premises infrastructures.
-
Knowledge of operating systems and virtualization technologies.
-
Networking and network security controls.
-
Scripting and programming languages.
-
Project management.
Entry requirements & common certifications
This career path requires experience and technical proficiency. Although many cybersecurity engineers come from a formal education such as degrees related to computer sciences, this is not mandatory.
To pursue this path, you must have a strong foundation in computing and IT infrastructures, complemented by a thorough understanding of cybersecurity concepts, and the ability to seamlessly connect this knowledge.
Recommended training and certifications:
-
Security+ Systems Security Certified Practitioner (SSCP) and Advanced Security Practitioner (CASP+): These are highly regarded certifications that teach essential engineering skills.
-
AWS Certified Security - Specialty or Microsoft Azure Security Engineer Associate (AZ-500): These certs can make your resume more attractive to companies seeking cloud security solutions.
Choose your cyber career path
That’s a glimpse into the exciting range of career paths available in cybersecurity!
The field of cybersecurity needs motivated professionals who are passionate about making a difference. As we’ve seen, cybersecurity is not only about hacking. It is a diverse, deep industry that offers plenty of opportunities for those interested in building a career.
So whether you have a background in computer science or not, there is a cybersecurity career that suits your skills and interests.
Follow your passion, learn, obtain industry-relevant certifications, and start with an entry-level job to gain experience.
If you’re a beginner, consider these five free Hack The Box Academy Modules as a starting point.
|
Author bio: Pedro Correia (g4rg4m3l), Cybersecurity Lead, Red Teamer, and Instructor at Code For All_ Pedro Correia is a cybersecurity professional with a strong commitment to both learning and teaching. He currently serves as a Cybersecurity Lead, Red Teamer, and Instructor at Code For All_. He oversees a specialized team focused on penetration testing and cybersecurity assessments, with years of experience in educating students from diverse backgrounds worldwide in the domains of cybersecurity and programming. He also creates content specializing in various cybersecurity domains under the alias of “Cybersecurity Paladin.” As a Hack The Box Ambassador, Pedro hosts meetups, showcases, and live hacking demonstrations, making cybersecurity concepts more accessible to a wider audience. You can find him on HTB as “g4rg4m3l.” Pedro has embarked on a self-imposed delusional mission to infiltrate every Active Directory environment. Join him on this crusade. Feel free to connect with him on LinkedIn. |














