Threat Intelligence
Eek, a GodRAT: A step-by-step breakdown of a financial sector attack
A deep dive into GodRAT’s financial sector intrusion, mapping its attack chain, steganographic loaders, and RAT techniques to MITRE ATT&CK and real-world defenses.

diskordia,
Dec 18
2025
There’s something almost-romantic about cybercriminals dragging old malware into the present. Just as Hollywood keeps rebooting 90s movies (for better or worse), threat actors are rebooting RATs like it’s the Black Death out there.
GodRAT (associated with the Winnti APT group) was uncovered by Kaspersky’s GReAT team in 2024/2025 and is the latest installment in a franchise nobody really wanted to bring back. It’s a scrubbed-up, plugin-powered, steganography-smuggling, AsyncRAT-packing descendent of Gh0st RAT, one of the most popular backdoors of the last two decades.
In this piece, we’ll take a closer look at how it all went down, with a handy table mapping GodRAT’s attack actions to MITRE ATT&CK and HTB resources. Let’s jump in.
Table of Contents
- The document is a lie
- The loaders: Now things get interesting
- GETGOD and ye shall receive
- GodRAT: old RATs, new tricks
- Stealth, but make it practical: persistence and masquerading
- Credential theft: Chrome and Edge take the bait
- AsyncRAT has entered the chat
- Attribution: a familiar signature in a new coat
- Why it matters
- What security teams can do
- Final thoughts on GodRAT
The document is a lie
The campaign kicks off with a straightforward premise: financial employees exchanging documents over Skype. Not email, but Skype. That fact alone suggests the threat actor understood the target environment on a granular level.
Between September 2024 and August 2025, Kaspersky tracked multiple malicious files passed off as financial records: “2024-08-01_2024-12-31Data.scr,” “Corporate customer transaction &volume.pif,” and others. These were sent to brokerage and trading firms across Hong Kong, the UAE, Jordan, Lebanon, and Malaysia.
If the filename didn’t give it away, the extension will have: .scr and .pif executables dressed up as spreadsheets. A couple of clicks, and the user has just ignited the first stage.
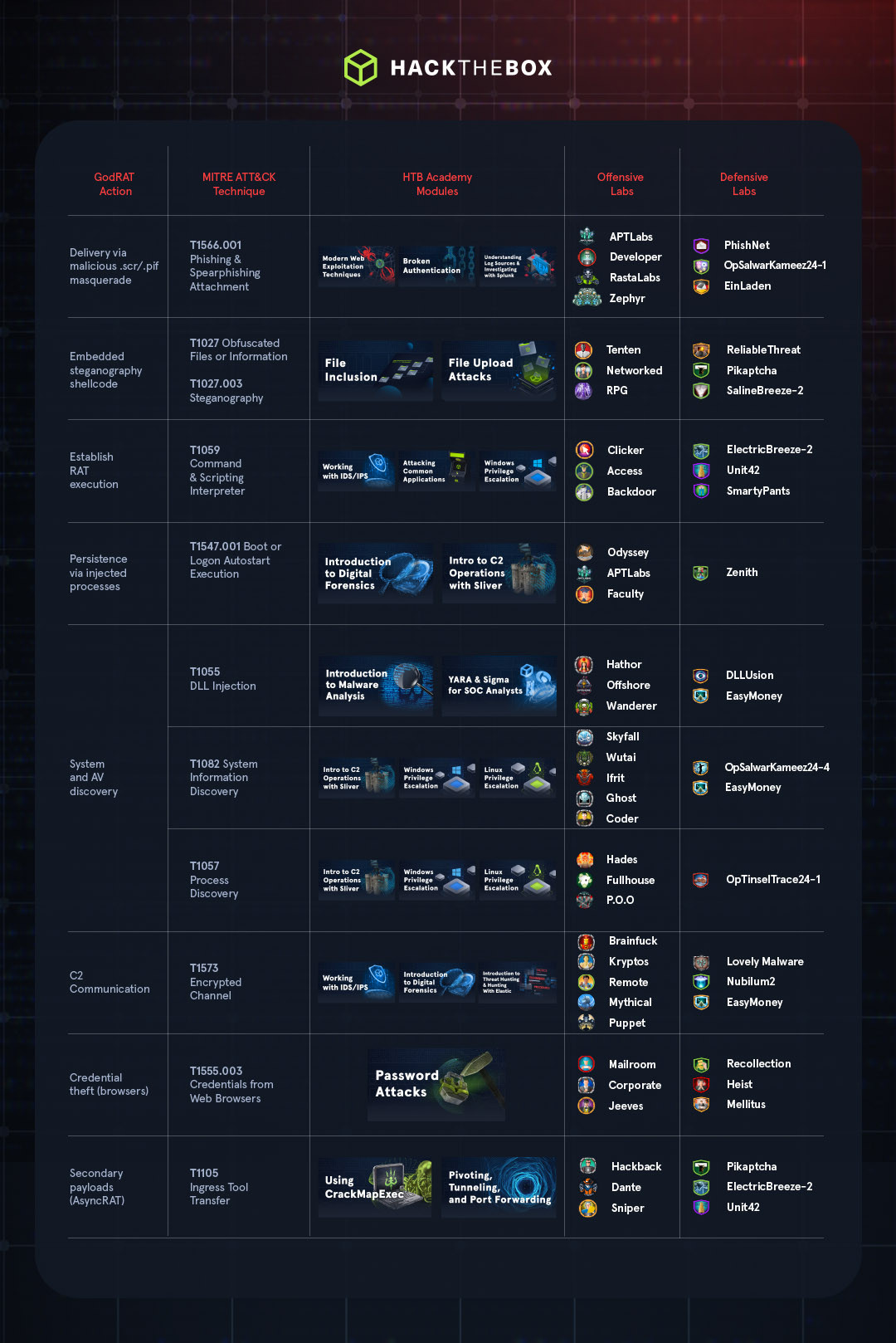
The loaders: Now things get interesting
The key differentiator in this campaign is its pair of loader families. The first is straightforward: a self-contained executable with XOR-encoded shellcode inside. The loader decodes it using a hardcoded key ("OSEDBIU#IUSBDGKJS@SIHUDVNSO*SKJBKSDS#SFDBNXFCB" if we're being specific) and injects it into its own memory before running it. A classic case of process injection.
The second loader is very cute. Inside a self-extracting archive delivered to victims, analysts found:
-
A legitimate
Valve.exebinary signed with an expired DigiCert certificate -
A malicious
SDL2.dll -
A JPEG image containing hidden shellcode
The image looks like financial details. In reality, it’s carrying encrypted shellcode. When Valve.exe loads SDL2.dll, the DLL quietly extracts the shellcode from the JPG, maps new memory, and runs it. The actor doesn’t just hide behind a borrowed signature; they disguise their payload inside an image of exactly the kind of content the victim expects to open.
Steganography in attack loaders isn’t new, but it’s not exactly commonplace. That makes it a little easier to slip past controls.
GETGOD and ye shall receive
Once running, the first stage searches for the marker string godinfo, uses XOR 0x63 to decode its configuration, and phones home to the attacker’s command-and-control server.
The opening line of the conversation? GETGOD. The server responds with:
-
A second-stage shellcode blob
-
A UPX-packed GodRAT DLL
-
Additional configuration
The first stage then overwrites the new configuration with its own values—an unusual but deliberate design choice—and launches a new thread to execute the freshly unpacked RAT.
It’s modular, consistent, and engineered to keep configuration handling under the attackers’ control.
GodRAT: Old RATs, new tricks
GodRAT’s main payload, ONLINE.dll, exposes just one export: run. Behind that unassuming entry point sits a full-featured RAT with:
-
System fingerprinting (OS, hostname, process details, user, AV presence)
-
Custom packet format using a 15-byte header + zlib compression + triple XOR
-
A plugin architecture built for extendable post-compromise activity
The most significant plugin observed was the FileManager module. And this thing is not subtle. It can enumerate drives, browse user directories, read/write/delete files, launch programs (hidden or visible), unzip payloads with dropped 7z.exe/7z.dll, and execute commands via both Internet Explorer and cmd.exe. It even checks whether the compromised user is operating as SYSTEM.
Stealth, but make it practical: persistence and masquerading
The campaign maintains persistence via:
-
A Run key at
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\MyStartupApp -
Running the RAT inside legitimate processes like
curl.exeorcmd.exeusing a-Puppetflag
The -Puppet parameter is a smoking gun linking GodRAT to AwesomePuppet, another RAT built on Gh0st RAT. Kaspersky found the GodRAT builder and source code uploaded publicly in July 2024—complete with options to inject into legitimate binaries or output .exe, .scr, and .pif payloads.
This is not sloppy tooling, but rather a fully configurable builder environment tailored for distributing modern Gh0st-family implants.
Credential theft: Chrome and Edge take the bait
Once GodRAT is in place, victims aren’t just monitored—their credentials get harvested. Kaspersky identified two standalone credential stealers:
-
A Chrome stealer dropped at
%ALLUSERSPROFILE%\google\chrome.exe -
An Edge stealer dropped at
%ALLUSERSPROFILE%\google\msedge.exe
Both modules extract login credentials from browser SQLite databases (Login Data) and decrypt stored passwords using the Local State key. They save the results as google.txt and edge.txt.
In an industry like finance, where compromised credentials can lead to fraudulent transactions, unauthorized trades, or deep exposure of market-sensitive data, this is the real danger zone.
AsyncRAT has entered the chat
If GodRAT wasn’t enough, the attackers deploy AsyncRAT as a secondary backdoor, delivered via DLL (LoggerCollector.dll) that performs reflective injection and executes a C# payload.
It also patches:
-
AmsiScanBuffer -
AmsiScanString -
EtwEventWrite
confirming that the threat actor is intentionally degrading endpoint defenses.
Attribution: a familiar signature in a new coat
Kaspersky is cautious and doesn’t jump to conclusions, but they highlight:
-
Overlapping code with AwesomePuppet
-
Shared command-line flags (
-Puppet) -
Gh0st RAT fingerprint headers
-
Infrastructure and workflow similarities seen in clusters historically linked to Winnti groups
This doesn’t mean GodRAT is Winnti. But it definitely means whoever built it knows their history and knows their tooling.
Why it matters
Financial firms operate in environments with:
-
High-value movement of assets
-
Credential-dependent workflows
-
A culture of rapid document sharing
-
Reliance on messaging apps for time-sensitive coordination
GodRAT slots into this world with ease. Credential theft + remote access = potential fraudulent transactions. Persistent RAT control equals long-term espionage. AsyncRAT in the back pocket equals fallback access if defenders get lucky.
There’s no ransomware or flashy extortion. Instead, we have a stealthy, Oceans 12-laser-scene-style structured intrusion. And that makes it worse.
What security teams can do
First things first: neutralize the root cause: block .scr and .pif attachments in messaging platforms. Finance employees shouldn’t be opening executable “spreadsheets,” point blank, period, no ifs or buts.
Next, address the loader. Steganography-based payloads stand out with entropy analysis and by monitoring DLL load patterns. SDL2.dll loading a JPG should never be a normal event. Sandboxing can reveal that behavior before an analyst ever sees it.
When it comes to endpoints, detection should pivot to memory. Both GodRAT and AsyncRAT rely heavily on injection, reflective loading, and AMSI/ETW tampering. Modern EDRs can flag inline patching of EtwEventWrite or calls to unbacked memory regions. That’s your canary down the mine.
Finally, assume browser-stored credentials are always at risk in finance. Enforce enterprise credential managers, disable local password storage, and watch for non-browser processes accessing Chrome and Edge directories. Those file paths—Login Data, Local State—are some of the cleanest signals you will ever get.
And if GodRAT does show up? Quarantine, memory capture, credential resets, full audit of Skype communications, and a network-wide hunt for the AsyncRAT loader paths documented by Kaspersky.
Final thoughts on GodRAT
GodRAT isn’t re-inventing the wheel. It’s not cutting-edge malware with novel exploit chains or bespoke zero-days. But it works because it’s disciplined, well-maintained, and strategic. It uses just enough new tricks (steganographic loaders, plugin architecture, dual implants) to sneak into environments where old-school RATs could never.
Download our CTEM report and stay ahead of threats like GodRAT
If anything, GodRAT highlights two uncomfortable truths: you don’t need futuristic malware to compromise modern financial systems. You just need one reliable thing, and a trusting user who double-clicks a fake file in Skype.














