Security 101
What is Active Directory? (Active Directory hacking intro)
Active Directory (AD) is a directory service for Windows network environments used by an estimated 95% of all Fortune 500 companies.

mrb3n,
May 17
2022
Table of Contents
What is Active Directory?
Active Directory (AD) is a directory service for Windows network environments used by an estimated 95% of all Fortune 500 companies. Its structure facilitates centralized management of an organization's resources which may include users, computers, groups, network devices, file shares, group policies, devices, and trusts.
At the highest level, AD provides authentication and authorization functions within a Windows domain environment. While it has been a target of hackers since its inception, attacks and research continue to evolve.
Recommended read: Active directory pentesting and cheatsheet
Why is Active Directory important for cybersecurity?
AD remains a key area of interest for offensive and defensive security practitioners because when an Active Directory environment is compromised, this typically results in almost complete control over the network. An initial installation of AD is arguably "not secure by default," and it can be easily misconfigured.
Weaknesses in AD, including common and obscure misconfigurations, recent vulnerabilities, and built-in functionality that attackers can abuse, can be leveraged to move laterally and vertically within a network environment and gain unauthorized access and persistence. AD is essentially a large database where many components can be queried by any authenticated user in the domain, regardless of their privilege level.
💡Note: If you're interested in learning how to defend active directory, check out our guide on Active Directory hardening, in which a SOC analyst defends AD from our Head of Security's attempts to perform a Golden Ticket attack.
Short History of Active Directory
Active Directory has been around for a couple of decades, and Microsoft's commitment to backward compatibility is commendable, but, as a result, some configurations are insecure by default. A basic AD user account with no added privileges can enumerate most information within the domain (including misconfigurations and flaws that could lead to unintended access) and even perform many different attacks. Due to this, organizations must focus on defense-in-depth and strategic planning, emphasizing security, AD hardening, hygiene, network segmentation, and limiting rights and privileges wherever possible.
While certain insecure practices have been eliminated as AD has evolved over the years (like allowing anonymous access to query any information in the domain without an authenticated user account and allowing admins to store passwords in Group Policy Preferences files), some "legacy" misconfigurations can still be seen in modern AD environments due to how AD upgrades can be performed. Domain Users being able to read this information isn't a vulnerability in itself, but since all users do have read access, if the domain is not properly hardened, any user, regardless of privilege level, can relatively easily sniff out misconfigurations with tools like BloodHound
Active Directory, by design, makes information easy to find and use for administrators and users alike. AD is highly scalable, supports millions of objects per domain, and allows the creation of additional domains as an organization grows, making it often the go-to choice for everything from small to mid-sized and large enterprises.
Source: Tools4ever
How Active Directory works
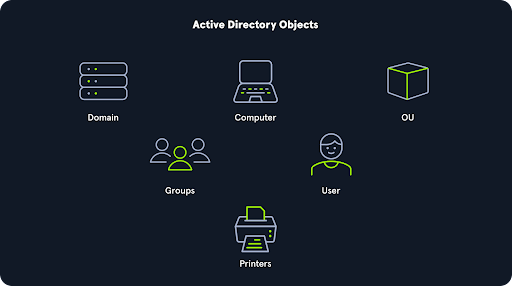
As mentioned, AD is a directory service used in Windows network environments (AD also provides authentication and authorization functions). It is a distributed, hierarchical structure that provides centralized management of an organization's resources, such as:
-
Users
-
Groups
-
Computers
-
File shares
-
Group policies
-
Trusts
At its core, a directory service provides an organization with ways to store directory data and make it available to users and administrators alike on the same network. AD stores sensitive information such as usernames and passwords and manages rights and access to information within the network, such as servers, databases, and file shares.
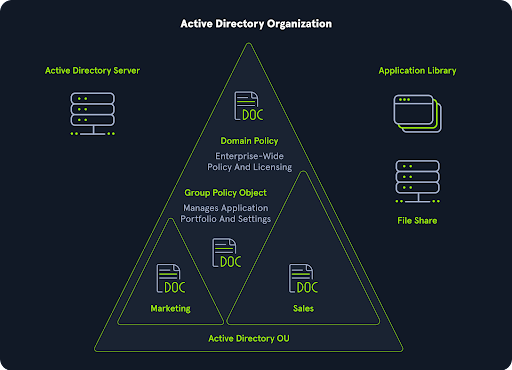
Active Directory is set up in a hierarchical tree structure. A forest is at the top, containing one or more domains that can have their own nested subdomains. In other words, a forest can contain multiple domains, and each of these domains can include its own subdomains. A domain contains objects (users, computers, groups, password policies, Group Policy Objects (GPOs), Access Control Lists (ACLs), etc.) and helps to manage access to these resources.
AD domains differ from DNS domains. The former is used to organize records on an internal network. The latter is used for locating services (matching IP addresses to hostnames when browsing the internet and vice-versa). That being said, DNS is also used within AD networks but to match internal IP addresses to host records.
There are various ways for handling authentication in Active Directory, and users and groups can be assigned permissions in many different ways. Access can be controlled at a highly granular level and is used to determine which users can access which servers, workstations, file shares, applications, and more, and at which permission level.
As stated earlier, a standard domain user with no added privileges can query most objects in AD, and due to its sheer size and how quickly an AD network can expand, it can be tough to administer and secure properly.
Why Does AD Get so Much Attention?
Active Directory can be considered "used by many, but secured (properly) by few.” In many companies, it presents a massive attack surface, especially for companies in industries that frequently acquire other organizations and "plug" their AD environment in through the use of a domain trust. This makes AD a key focus for attackers, especially as minor changes can open up significant flaws, and new attacks are constantly being made public.
Furthermore, many flaws can only be discovered through manual enumeration and are often missed by organizations that rely on vulnerability scans or only surface-level penetration tests. Though tools such as BloodHound PingCastle can be used to audit AD environments for misconfigurations, it takes a skilled (human) pentester to assess the results properly and secure an AD environment. Even the best tools can miss issues, so the human element cannot be replaced when looking to maintain a high level of security in an AD network.
In many environments (due to a lack of network segmentation), a successful phishing attack could land an attacker in a position inside the environment that would give them enough access to map out the domain with open-source or built-in tools, looking for ways to further their access. As security professionals, no matter if we're on the red or blue side, we will come across AD environments of all sizes throughout our careers.
For this reason, it is essential for us to gain a firm grasp of the structure and function of AD and how to enumerate, attack, and remediate all types of flaws and misconfigurations. Being better informed as both an attacker and defender will help us provide better value to our customers or the organizations we support internally. Microsoft has a near-complete monopoly in the directory services space. Even though many companies are transitioning to cloud and hybrid environments, on-prem AD is not going away for many companies.
Ransomware groups continue to target Active Directory to gain a foothold and spread their access through the environment. Evidence has shown that the Conti Ransomware, which has been used in more than 400 attacks worldwide to date, leverages recent critical flaws that affect Windows machines in AD environments such as PrintNightmare (CVE-2021-34527) and Zerologon (CVE-2020-1472) to expand access within an AD network.
Understanding the structure and function of Active Directory is a key step towards a career involved in finding and preventing these types of flaws before attackers do. Researchers are constantly discovering new, high-impact attacks that affect Active Directory environments. Many of these attacks require no more than a standard domain user to obtain complete administrative control over an entire AD domain.
History of Active Directory
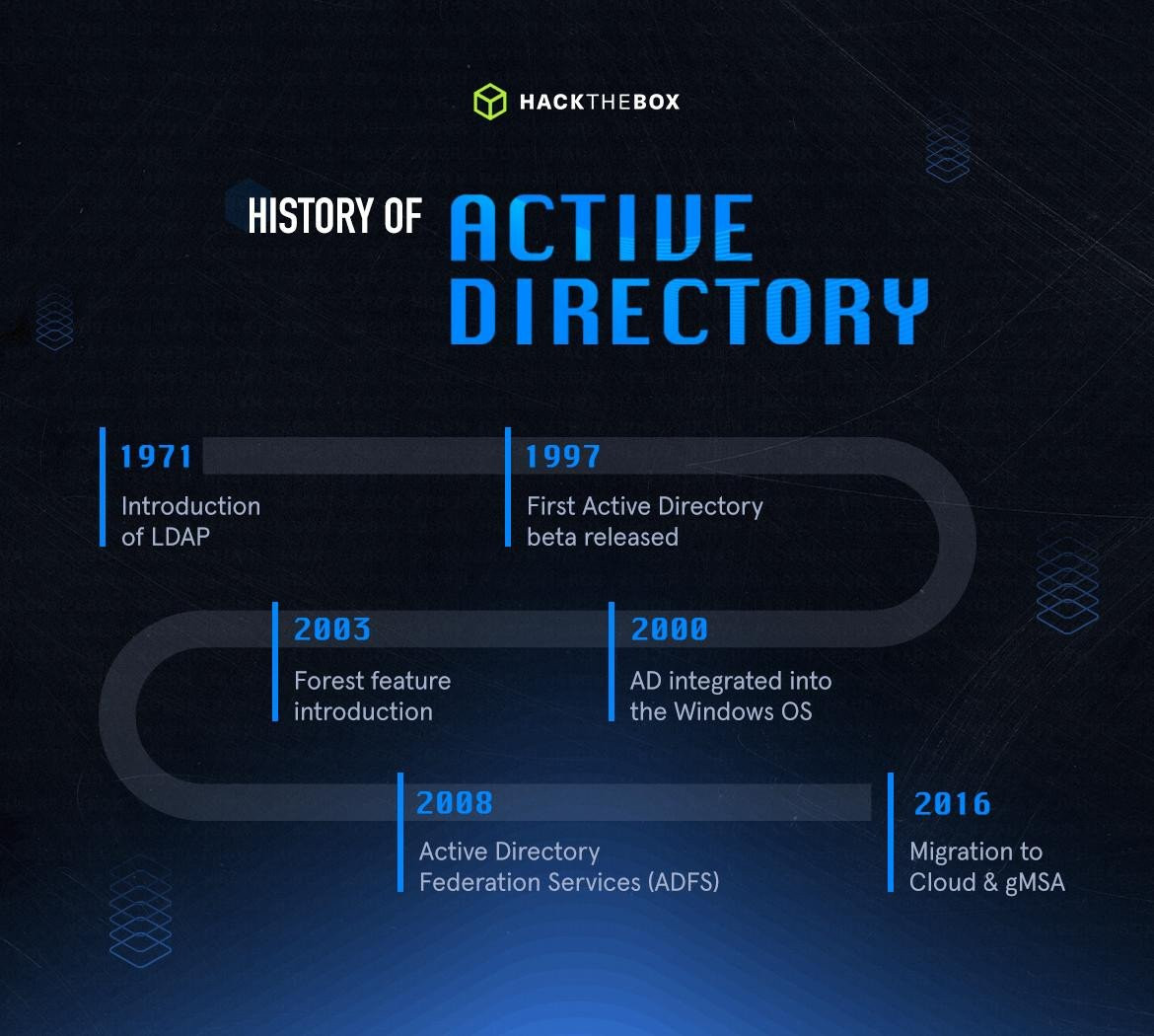
LDAP, the foundation of AD, was first introduced in 1971. The X.500 organizational unit concept is a precursor to AD. This was created by Novell and Lotus and released in 1993 as Novell Directory Services and can be considered the earliest version of all directory systems.
The first beta release of Active Directory was in 1997, but it was not integrated into the Windows operating system until Windows Server 2000 was released. Each subsequent release of Windows Server saw added functionality and improvements in administration. Windows Server 2003 introduced the Forest feature, which gave sysadmins the ability to create "containers," or groupings, of separate domains, users, computers, groups, and other objects.
Server 2008 saw the debut of Active Directory Federation Services (ADFS), which provides Single Sign-On (SSO) to systems and applications for users using Windows Server operating systems. ADFS streamlined the process of signing into applications and systems on a different LAN, allowing them to access organizations across organizational boundaries with a single set of credentials.
Server 2016 brought even more changes to AD, including functionality for migrating AD environments to the cloud and further security enhancements such as user access monitoring and Group Managed Service Accounts (gMSA). Group Managed Service Accounts offer a more secure way to run automated tasks, applications, and services. By design, they use very complex passwords, automatically rotate on a set interval (like machine accounts), and are a key mitigation against the infamous Kerberoasting attack. This release also brought a more significant push toward the cloud with the inclusion of Azure AD Connect as an SSO method for users being migrated to Microsoft Office 365.
Since its inception in 2000, AD has suffered from various severe vulnerabilities and is not "secure" out of the box, leading to many possible misconfigurations that can lead to domain compromise from just a standard domain user account or, in some instances, from an unauthenticated standpoint on the internal network.
New vulnerabilities and attack techniques are constantly being discovered, with manual techniques and automated exploit PoCs being made publicly available quickly after discovery. It is imperative that organizations that run AD remain on top of patching and implementing fixes. Understanding legacy and modern AD security issues can put us one step ahead of attackers.
Over the past decade or so, AD has been a significant focus area for security researchers, with tools for leveraging new vulnerabilities being publicly released in multiple languages (Python, PowerShell, and C# mainly) relatively quickly after an initial PoC is released.
Loads of research has gone into finding ways to abuse built-in Active Directory functionality, which has led to organizations having to harden their environments in new ways and implement new detection mechanisms. Starting in 2013 with the release of the tool Responder, we have seen many modern AD enumeration and attack tools and techniques emerge that have changed the game of AD security.
Some major tools and techniques that have only been in use for less than a decade include Responder, PowerView, and the PowerSploit framework, Kerberoasting, DCSync, CrackMapExec, the Impacket toolkit, BloodHound, ASREPRoasting, the Rubeus toolkit, PingCastle, and more.
New techniques continue to be discovered, with the latest major attack technique (accompanied by easy-to-use tools), noPac (also known as sAMAccountName Spoofing, exploiting CVE-2021-42278 and CVE-2021-42287), being released in December of 2021 when much of the industry was abuzz about the Log4j vulnerability. noPac allows any standard domain user to escalate to Domain Admin rights in an unpatched environment within seconds.
We will continue to see new attack techniques focusing on AD (and now Azure AD) over the coming years, and organizations need to remain on top of things to best protect their networks.

Where to Start Learning about AD?
Learning about AD can be a daunting task. It is hard to know where to begin, but with anything, we should start with the basics. A great place to start is standing up your own Active Directory lab environment.
Having an AD network to practice configuring (and securing) gives us invaluable skills which will lead to a deep understanding of the structure and function of AD. Experience with setting up, administering, and securing Active Directory will give us a leg up and help us be the penetration tester that finds flaws that others miss and provide great value to our clients or internal teams when recommending remediation and hardening measures in our penetration testing reports.
Even misconfiguring AD to practice legacy and modern attacks, tools, and techniques can be an incredibly valuable learning experience.
HTB Academy
Aside from self-study and creating your own AD environment to practice in, there are many ways to gain the necessary experience in and knowledge of AD. HTB Academy has a great deal of material on Active Directory for those looking to get started in AD or learn more.
If you are an absolute beginner, I recommend the Introduction to Active Directory module. If you are comfortable with the fundamentals and want either start with or hone your enumeration and attacking skills, the Active Directory Enumeration & Attacks module is an immense and immersive introduction to foundational AD enumeration and attack concepts that you will use time and time again when assessing AD environments.
It helps lay the groundwork for future, more advanced AD modules. Once you've mastered these two modules, I recommend working through the Active Directory LDAP module to hone your skills in enumerating Active Directory with built-in tools, and then the Active Directory PowerView, and Active Directory BloodHound modules to further refine your AD enumeration skills. We are constantly adding new courses to HTB Academy, so stay tuned for loads more AD content.
Old-but-gold HTB Machines
Hack The Box has many AD-focused boxes that are great for learning and practicing enumerating and attacking AD. The boxes below are excellent for honing your AD skills, and the Ippsec videos provide in-depth explanations to further your understanding.
HTB Tracks
The AD Track is an excellent resource for practice. Tracks are curated lists of machines and challenges that users can work on to master a particular topic. This track contains boxes of varying difficulties with various attack vectors. If you cannot yet solve these boxes on your own, you will still learn a lot by following a walkthrough or video. The more you are exposed to AD (and any topic), the more comfortable you will become, and eventually, things that right now may seem completely foreign will become second nature.
HTB Pro Labs
When you're up for a realistic challenge that emulates a real-life network, check out Pro Labs. These are larger, simulated corporate networks that teach real-world skills in enumerating and attacking AD.
-
The Offshore Pro Lab is an intermediate-level lab packed full of modern AD attacks and is an excellent test of your enumeration skills.
Once you have mastered Offshore, we have other, more advanced Pro Labs focusing on AD exploitation.
Aside from practicing on HTB Academy and the HTB main platform, I recommend several blogs for reading up on AD security, everything from legacy attack methods to the latest and greatest research.
-
The SpecterOps blog presents excellent research on various AD security-related topics.
-
Harmj0y has been an instrumental figure in the industry and has developed and contributed to many of the most widely used and well-regarded AD security tools such as the PowerSploit framework (including PowerView), the PowerShell Empire Project, the Rubeus toolkit for attacking Kerberos, BloodHound/SharpHound, and more. He also presents extensive and well-thought-out research on many AD security topics.
-
AD Security Blog by Sean Metcalf is a must-read for anyone new to or looking to expand their knowledge of AD security.
-
Dirk-jan Mollema has an excellent blog that discusses many modern AD attack techniques.
-
0xdf's blog is an excellent supplemental resource to Ippsec's videos. His writing style is extremely clear, and he dives in deep on many topics and doesn't merely show the steps to solve an HTB box. You will learn loads by reading his box walkthroughs, even if you could already solve a box on your own.
As you can see, there is no shortage of excellent content out there for learning about AD and AD security. While this list may seem overwhelming, make a plan and chip away at it bit by bit. It's not a race, and you will not master AD overnight, but persistence and constant hunger to learn, improve, and push the boundaries of your knowledge will pay dividends. Can’t wait to see your progress!














