Cyber Teams
Train red, blue, and purple with HTB’s Detection & OpSec Cyber Range
Train red, blue, and purple teams in a realistic lab with adversary emulation, detection tooling, and full SOC workflows. No setup required.

diskordia,
Aug 11
2025
Table of Contents
A lot of cyber ranges stop short of operational realism. They provide either offensive or defensive training, rarely both. And they almost never replicate the full attack lifecycle, telemetry pipelines, or case management you’d encounter in a real-world SOC.
That’s why we crafted the HTB Detection & OpSec Cyber Range: a cloud-based, hands-on training environment where red teams mount adversary-grade attacks, blue teams detect and investigate them in real time, and purple teams work together on iterative improvements to detection and response.
It’s much more than training; it’s operational readiness, refined in a repeatable, controlled, and fully monitored setting.
What is the Detection & OpSec Cyber Range?
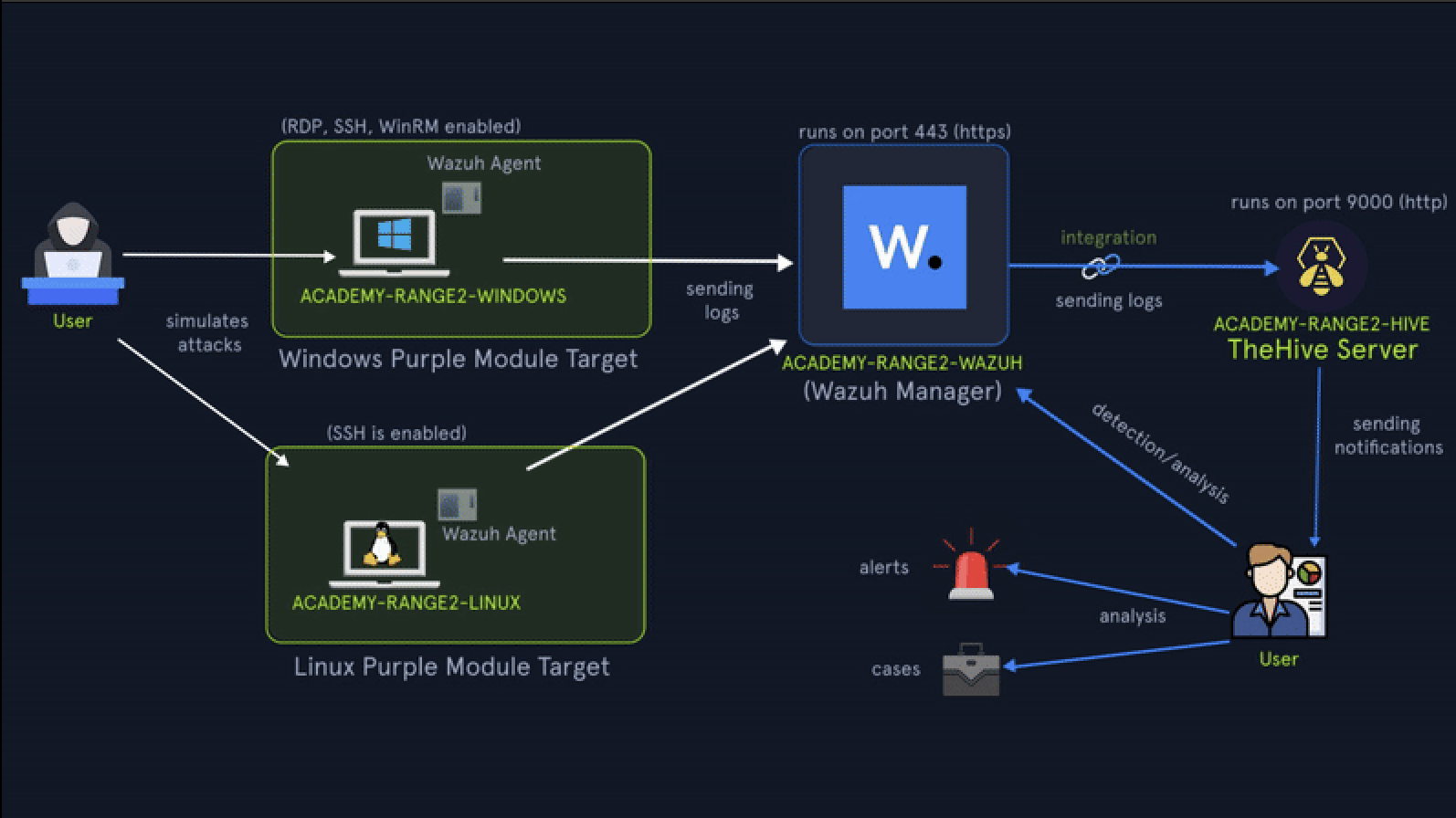
At its core, the Detection & OpSec Range is a live-fire simulation environment tailor-made for adversary emulation and active threat hunting. It includes:
-
Built-in SIEM (Splunk & Wazuh) streaming logs from endpoints and network activity
-
TheHive case management to triage, escalate, and track incidents
-
Red team simulation tools mapped to MITRE ATT&CK, including Atomic Red Team
-
Endpoint access via SSH/RDP, plus tools like Velociraptor for live forensics
-
Customizable OpSec levels, enabling red teams to vary stealth and test detection depth
Teams can launch TTPs, monitor telemetry, trigger alerts, perform triage, and conduct post-compromise analysis all in a single platform, with no setup necessary.
What makes a modern cyber range?
In the majority of training labs, defenders don’t get to see the kill chain in its entirety. Attackers work in a vacuum, and defenders operate on contrived logs or prefab scenarios.
There’s no shared telemetry, no adversary context, and no way to iterate on detection logic based on live signals. On the flipside to that, HTB’s Detection and OpSec Range offers:
-
Live telemetry and alert pipelines from real attack traffic
-
Active adversary simulation, not replayed payloads
-
Integrated blue tooling, including alert triage, log inspection, and response workflows
-
Feedback loops, enabling purple teams to close detection gaps quickly
It’s everything traditional ranges wish they had; tightly integrated, highly interactive, and tailored for real-world team roles.
Technical use cases: from emulation to detection
The majority of cyber ranges tend to cater to red and blue teams in equal measure. But the reality is that their respective levels of readiness aren’t always the same. For example, our 2024 report found that only 32% of blue teamers trained on a weekly basis in contrast to almost 50% of red teamers.
That kind of imbalance has a real-world impact. When defenders don’t get enough hands-on time (often due to things like burnout, intense workloads, ever-present backlogs and so on), they risk falling behind on attacker TTPs, leaving organizations vulnerable to newer or more stealthy threats.
That’s where the Detection and OpSec Range swoops in to close the gap by creating a space where defenders can respond to live attacks—not static logs—and refine their skills and detection logic in real time.
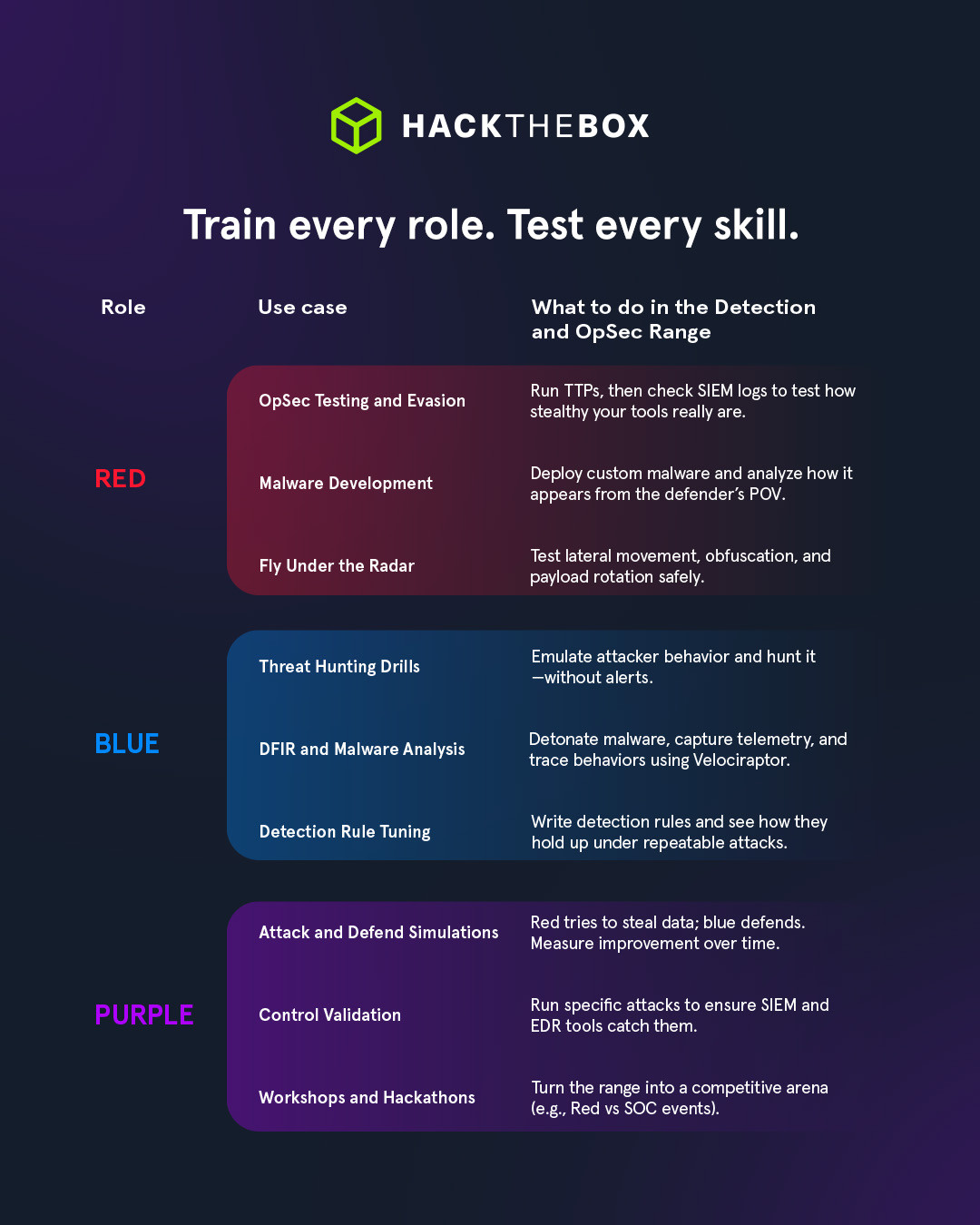
For red teams
Launch adversary TTPs, or tools like Atomic Red Team, with clear MITRE mappings. Then adjust OpSec (rotate payloads, obfuscate scripts, throttle execution, simulate lateral movement) and watch how defenders respond. This is the perfect space for you to test new tradecraft without risking real environments.
For blue teams
Stream telemetry from host and network activity to Splunk and Wazuh. Triage alerts in TheHive, pivot to endpoint telemetry using Velociraptor, and walk through the full IR workflow, from identification to investigation, containment planning, and post-incident review.
Need to fine-tune a detection rule? No problem. Just regenerate the attack and validate the update. Simple.
For purple teams
Collaborate in real time. Red executes a TTP, blue responds, and both review the outcome. Did detection fire? Was it actionable? How did triage go down?
Refine the detection logic, rerun the test, and document improved visibility. This is where collaboration meets iterative defense development.
Purpose-built for teams who need operational realism
Whether you're defending critical infrastructure or training the next generation of SOC analysts, the Detection & OpSec Range delivers:
-
For red teamers: Execute attacks, customize TTPs with tools like Atomic Red Team or C2 frameworks, install beacons, and simulate evasive tradecraft while leveraging real-time telemetry to validate stealth, persistence, and detection thresholds.
-
For SOC teams: Run tailored detection tuning workshops using live attack data.
-
For MSSPs: Demonstrate IR playbooks to clients, validate tool coverage, and upskill hybrid-skilled analysts.
-
For government and military: Emulate nation-state TTPs in a safe environment. Recent data shows that government teams are underperforming in AI and cryptography domains, despite policy-level pushes such as USCYBERCOM’s AI roadmap. This range helps bridge that gap.
-
For critical infrastructure: Stress-test your blue team’s ability to detect stealthy, multi-stage threats. Threat groups like Scattered Spider and DragonForce, for example, have kicked their campaigns up a notch here, exploiting VMware hypervisors, cloud misconfigurations, and weak lateral movement defenses. This range allows you to simulate these tactics safely so you can get a better sense of your detection coverage.
-
For academia: Give students access to an end-to-end simulation environment that bridges the gap between theory and field-ready skills.
-
For Retail and eCommerce: Train teams to respond to common breach vectors like credential stuffing and cloud misconfigurations. Groups like Scattered Spider are actively targeting retail brands, making realistic simulation a necessity.
Time to make the move from compliance to readiness
You don’t need another checkbox. You need a space where your teams can think like attackers, act like defenders, and collaborate like a mature security operation. The Detection & OpSec Cyber Range isn’t just another training module. It’s where modern purple teaming happens.
Hit the Detection and OpSec Cyber Range today!
Built-in tooling. ✅Gamified, repeatable exercises. ✅
No setup. Just launch and start learning. ✅













