Threat Intelligence
£300m gone: How Scattered Spider hit the UK’s biggest retailers
Scattered Spider expands its campaign from retail to the insurance sector, using social engineering to breach networks. Learn how the threat group operates and how to defend against it.

Howard Poston,
Jun 19
2025
Scattered Spider is a group of young, English-speaking cybercriminals that primarily communicates via platforms such as Discord and Telegram. The group is known for operating under a Ransomware as a Service (RaaS) model, using DragonForce, ALPHV/BlackCat, and other third-party ransomware within their attacks.
In April and May 2025, the group performed several attacks targeting UK retailers, including Marks & Spencer, Co-op, and Harrods. M&S, who thankfully have since recovered from the attack, suffered data loss and service outages that lasted days and impacted the company’s revenue and stock price. Co-op also suffered data loss and downtime, while Harrods experienced minimal operational impacts.
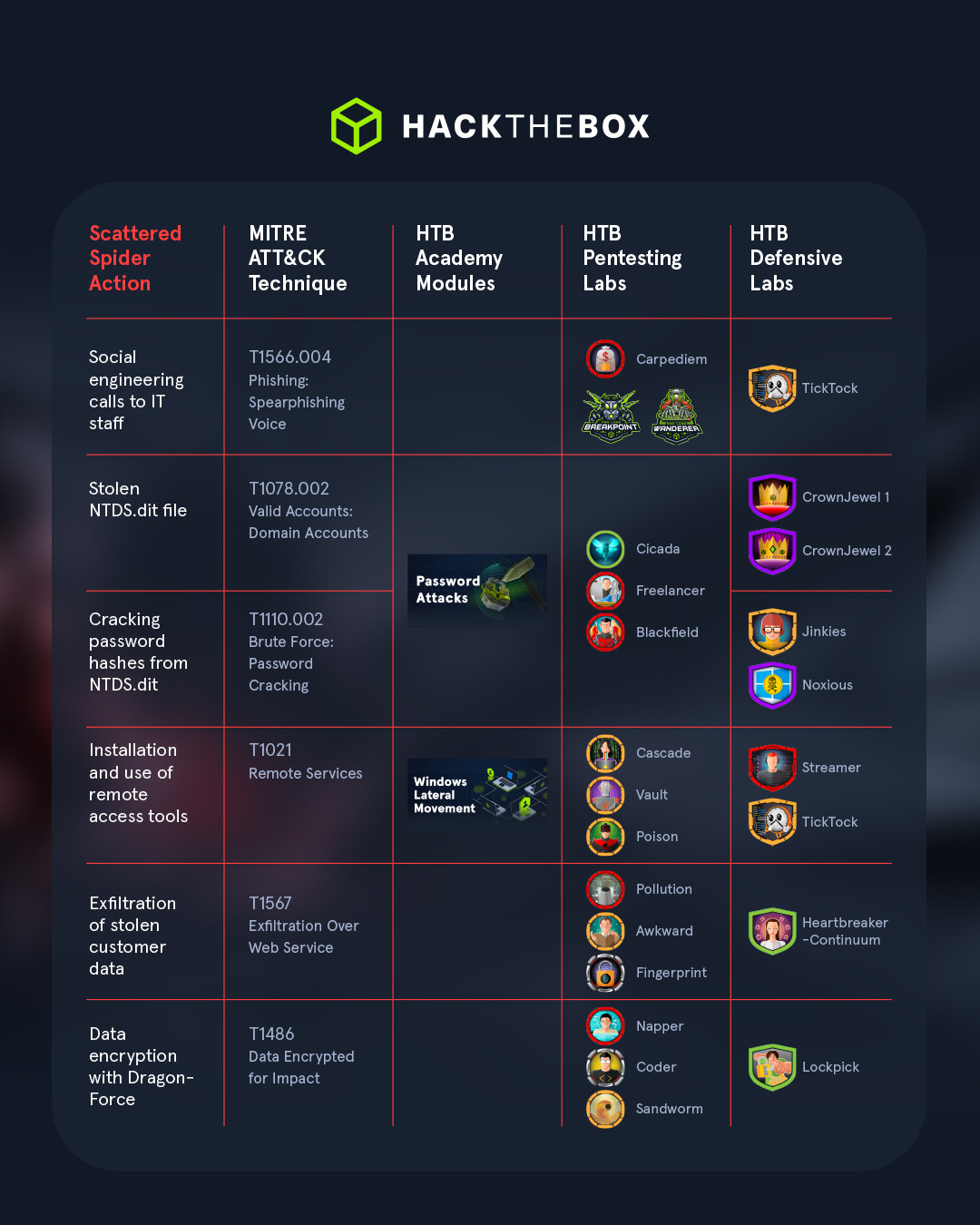
In this installment of the Hack The Box Attack Anatomy series, we detail the various techniques and tactics used by Scattered Spider in this attack campaign. These are mapped to the MITRE ATT&CK framework and Hack The Box resources that can be used for predictive security operations in terms of how these attacks can be performed and prevented.
Table of Contents
How Scattered Spider exploited UK retailers
The attacks on the three UK retailers were all attributed to Scattered Spider because the methods used closely matched the group’s standard techniques.
In general, these include the use of phishing attacks for initial access, off-the-shelf tools for lateral movement, and RaaS offerings to encrypt and exfiltrate sensitive data.
Initial access
Scattered Spider is known for using social engineering attacks to gain initial access to target environments. In this attack campaign, the group impersonated employees at target organizations to trick IT staff into resetting passwords to ones that the attacker controlled (MITRE ATT&CK Phishing: Spearphishing Voice).
When performing this type of scam, attackers work to develop a level of rapport and establish their identity with help desk staff before making requests. By doing so, their targets are more likely to send a password reset link to a new number or email address or reset multi-factor authentication (MFA) to support the user’s “new phone.”
In the case of Marks & Spencer, Scattered Spider allegedly gained access to the company’s environment in February 2025 and stole the NTDS.dit file for its Windows domain (ATT&CK Valid Accounts: Domain Accounts). This allowed them to crack password hashes to access various employee accounts (ATT&CK Brute Force: Password Cracking).
Lateral movement and persistence
With access to compromised accounts, Scattered Spider can move laterally through the network to compromise new accounts. This is especially true if the group had access to accounts with domain-level access.
Scattered Spider is also known for using legitimate remote access tools to expand their reach and maintain persistence (ATT&CK Remote Services). The group often installs multiple instances of TeamViewer, AnyDesk, and similar tools on a compromised system to maximize their chances of having backdoor access to a system.
Data encryption and exfiltration
Modern ransomware attacks, like those performed by Scattered Spider, often incorporate both data encryption and data exfiltration. Traditionally, ransomware groups used data encryption to pressure their targets into paying for restored access, but backups can undermine the effectiveness of this approach.
Exfiltrating data as well provides the attackers with an additional lever since they can threaten to expose the stolen data if the victim refuses to pay the ransom (ATT&CK Exfiltration Over Web Service).
Scattered Spider commonly works with RaaS operators, gaining access to specialized malware in exchange for a cut of the ransom. In the case of the attacks on UK retailers, Scattered Spider deployed the DragonForce ransomware (ATT&CK Data Encrypted for Impact) and attempted data encryption and exfiltration with mixed results:
-
M&S: The cybercrime group successfully stole customer data and encrypted several servers in the company’s VMware ESXi infrastructure. As a result, core services are disrupted, and the breach is estimated to cost the retailer approximately £300m or $400 million.
-
Co-Op: Scattered Spider successfully exfiltrated a significant amount of customer information from the company’s network. However, Co-Op detected the attackers’ presence before data encryption could be performed and shut down its own systems for remediation.
-
Harrods: The retailer identified an internal attack and restricted Internet access from its internal network. As a result, it didn’t suffer data encryption or exfiltration.
Scattered Spider targets insurers next
Scattered Spider is reportedly setting its sights on the insurance sector, according to Google’s Threat Intelligence Group. After this series of high-profile attacks on UK and US retailers, the group has pivoted, with multiple confirmed intrusions at US insurance companies in recent weeks.
Known for targeting one sector at a time, Scattered Spider continues to rely on social engineering tactics to bypass MFA and hijack accounts, this time focusing on help desks and call centers in the insurance industry.
Explore CTEM with Hack The Box
The warning comes as Erie Insurance investigates a suspected cyberattack discovered on June 7. While attribution is still pending, the incident aligns with Scattered Spider’s typical tactics and timing.
Security teams in insurance should be on high alert and take steps to harden access controls, train staff against social engineering, and detect lateral movement early.
Detect Scattered Spider techniques with HTB
Scattered Spider is a serious threat, targeting high-profile organizations using social engineering to hijack legitimate accounts—then exfiltrating and encrypting data for random. Their attacks on UK retailers led to data breaches, outages, and an estimated £300m in damages.
These types of attacks are an ongoing threat as Scattered Spider and other threat actors work to build on their successes. A recent attack targeting a major supplier of Whole Foods indicates that cyber threat actors have expanded their target base to include US retailers as well.
Because these techniques often bypass traditional defenses, the best countermeasure is preparation. That means hands-on training in social engineering detection, MFA implementation, least privilege access, and early threat identification.
Hit the HTB Labs to test your team! 🕷️
Hack The Box provides real-world labs and courses aligned with the exact tactics Scattered Spider uses. With these resources, your security team can better understand how these attacks are carried out and deploy controls that maximize their chances of detecting and remediating a Scattered Spider campaign before data encryption and exfiltration are complete.












