Blue Teaming
Your SOC vs. Reality: Why attackers are winning (and how Threat Range levels the battlefield)
Sharpen SOC and DFIR readiness with Threat Range. See how real attacker tradecraft, CTEM alignment, and measurable performance metrics prepare teams for today’s breaches.

diskordia,
Dec 19
2025
Spoiler: Your SOC isn’t ready for reality. But Threat Range is.
The average SOC feels one bad shift away from an episode of The Bear. And the numbers back it up, with a staggering 71% of SOC analysts experiencing burnout from overwhelming alert load, and breach response still drags from hours to days.
Breaches hit fast, threats morph even faster, and attackers collaborate like they’re running a motorsport pit crew. Meanwhile defenders are drowning in alert fatigue.
Most teams only ever rehearse isolated tasks: a bit of triage here, a forensic deep-dive there. But attackers don’t play in silos, and they definitely don’t follow your ticket escalation flow. Let’s get into the details.
Table of Contents
- Spoiler: Your SOC isn’t ready for reality. But Threat Range is.
- Cyber skills training v.s. Reality
- Threat Range: Where SOC training meets reality
- How Threat Range aligns with a CTEM-first program
- Inside Threat Range scenario: DomainLooter
- Threat Range methodology and the HTB ecosystem
- Why all of this matters for 2026 (and beyond)
- The takeaway for security leaders
Cyber skills training v.s. Reality
The 2025 Global Cyber Skills Benchmark report found, without a doubt, that teams are struggling in the exact domains attackers exploit most:
-
Secure Coding: 18.7% average solve rate
-
Cloud: 21.3% average solve rate
-
Web: 21.1% average solve rate
These aren’t just some innocent numbers. Those gaps line up with real-world failures like the MOVEit supply chain compromise, cloud misconfigurations, and recurring app-level issues that cost organisations millions.
And that’s before we touch emerging attack surfaces. Blockchain security remains weak in finance (10.1% solve rate). Government scored 5.6% on blockchain challenges and 8.9% on cryptography. AI and ML? Teams managed 37% and 30.1% respectively, at a time when AI systems are increasingly part of both enterprise workflows and attacker tooling.
None of this means defenders aren’t talented. It means their training doesn’t reflect reality. Threat Range fixes that.
Threat Range: Where SOC training meets reality
Threat Range is a team-based defensive simulation built for SOC and DFIR units who want training that actually resembles the mess and momentum of real incidents. No simplified labs or bite-sized theory exercises.
Your team steps straight into a fully instrumented environment using the exact tooling they use at work:
-
SIEM
-
EDR
-
Windows event logs
-
Memory dumps
-
Browser artifacts
-
Packet captures
And because this is Hack The Box, everything is engineered around real adversary behavior and CTEM-aligned workflows.
Teams are scored the way real incidents are measured
Threat Range automatically tracks:
-
MTTD
-
MTTI
-
MTTR
-
False positive/false negative accuracy
-
Quality of escalations
-
Noise reduction discipline
-
SLA adherence
Detection, analysis, containment, and reporting. End to end. No shortcuts. It transforms every scenario into a benchmarkable, repeatable CTEM exercise.
How Threat Range aligns with a CTEM-first program
The special CTEM Edition of the Global Cyber Skills Benchmark doesn’t mince its words: in an AI-driven landscape, human skills are still the make-or-break factor for exposure management:
-
Weak cloud fluency means scoping misses hidden assets.
-
Weak secure coding means exposures keep reappearing.
-
Weak reversing skills mean validation is shallow.
These gaps directly inflate breach cost, dwell time, and recovery. Threat Range sits at the juncture where CISOs need it most: between identifying gaps and proving whether teams can handle them under pressure.
Threat Range across CTEM phases
-
Scoping & Discovery: Teams uncover coverage gaps, audit blind spots, and missing logs.
-
Validation: Real attacker TTPs test whether teams can spot Kerberoasting, registry persistence, anomalous SMB, browser artifacts from phishing, LSASS access attempts, and more.
-
Prioritization: Performance data highlights which weaknesses carry operational and financial impact.
-
Mobilization: Teams practice coordinated containment across SOC tiers and DFIR roles.
-
Continuous Execution: Repeat quarterly to sustain readiness and quantify skill development over time. It is the bridge between benchmarking gaps (GCSB) and validating real-world risk (CTEM).
Inside Threat Range scenario: DomainLooter
Finally, the juicy bit, right? Meet DomainLooter, which simulates a full Active Directory compromise beginning with social engineering. It contains:
-
Domain Controllers
-
Admin Workstation
-
Web Proxy
-
Splunk SIEM
-
User Workstation
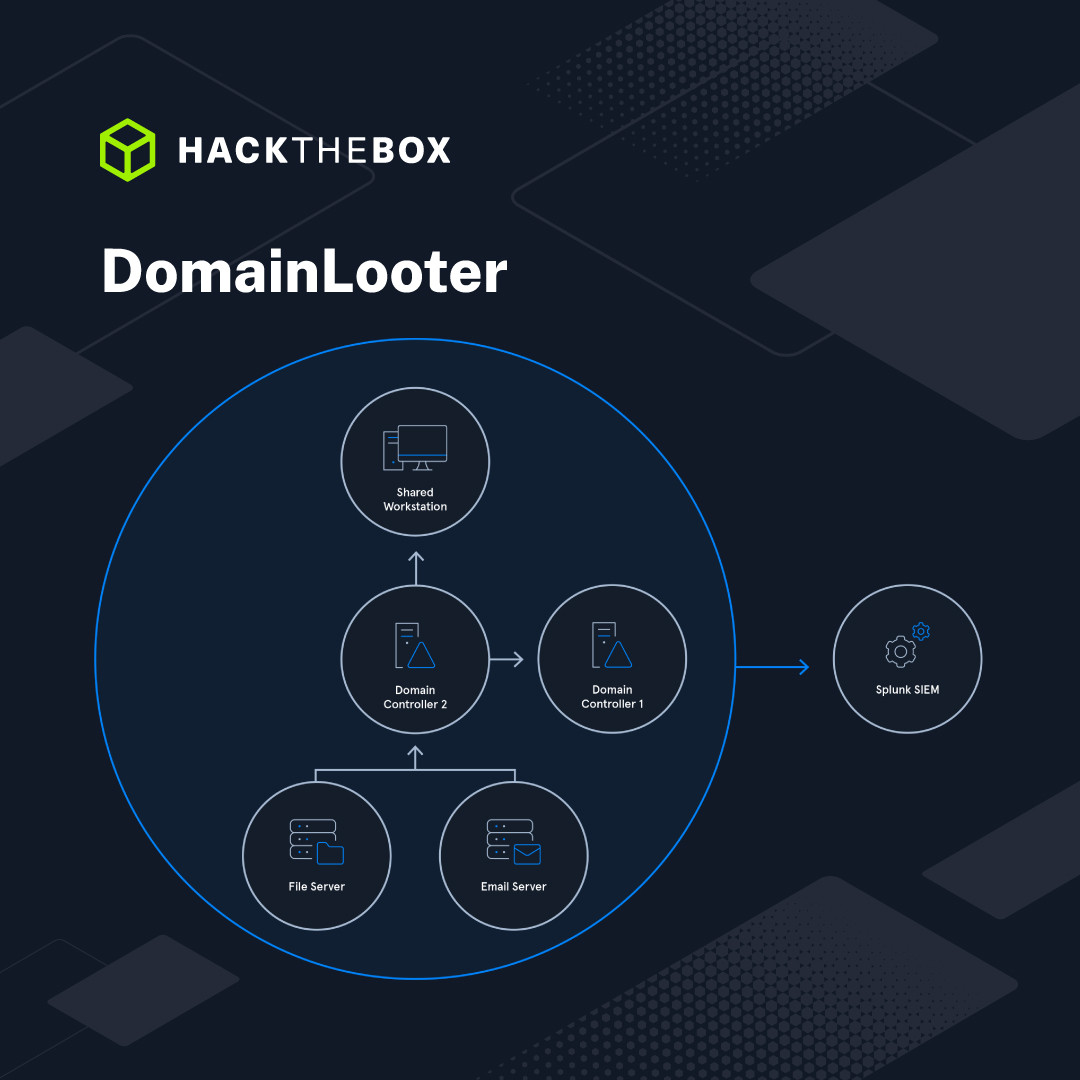
SOC and DFIR teams will need to work through:
-
Suspicious account creation
-
LSASS memory access artifacts
-
PowerShell anomalies
-
Browser artifacts tied to phishing
-
SMB traffic deviations
-
Memory dumps
-
PCAPs and host telemetry
-
A queue full of alerts… some noise, some catastrophic
They triage. They escalate. They reconstruct the kill chain. They assess blast radius.
It’s pressure-tested collaboration, not checkbox compliance.
Threat Range methodology and the HTB ecosystem
Threat Range scenarios are designed using the same methodology behind Academy modules, Sherlocks, and defensive labs. That gives teams a nice, clean progression loop:
Learn in HTB Academy:
-
Incident Response Levels 1 & 2
-
Memory Forensics & Volatility Basics
-
PowerShell Logging & Detection
Practice with Sherlocks and forensic CTFs:

Validate in Threat Range every 2–3 months:
-
Measurable, repeated, CTEM-aligned pressure testing.
-
This is training built around repetition, realism, and performance.
Why all of this matters for 2026 (and beyond)
The data is clear: industries are showing declining readiness in areas attackers gravitate toward. Secure Coding, Cloud, Web, Blockchain, and ML all display major gaps.
Threat Range continues to evolve with:
-
New APT-inspired simulations
-
Scenarios focused on cloud-centric breaches
-
AI-influenced attack patterns
-
OT/ICS-ready environments
-
Deeper CTEM metrics
Your workforce development strategy needs simulation at the center, not the edges.
The takeaway for security leaders
Repeat after me: Your SOC doesn’t need more dashboards. It needs reps. Your DFIR team doesn’t need more documentation. It needs pressure. Your organisation doesn’t need more theory. It needs measurable performance.
Threat Range delivers exactly that, aligned with CTEM maturity and supported by real-world data from nearly 800 teams across the 2025 Global Cyber Skills Benchmark.
Download the special CTEM edition of our report
If you want defenders who can handle what’s actually happening in the wild, not what’s in a certification syllabus, Threat Range is where they build that muscle.














