Red Teaming
Bring your attack surface to the air with the HTB Certified Wi-Fi Pentesting Expert (HTB CWPE)
Crack open the HTB CWPE's network exam and add Wi-Fi pentesting skills to your arsenal of corporate level attacks

JXoaT,
Jan 29
2026
We are extremely hyped to announce our challenge to professionals looking to crack into major networks! The HTB Certified Wi-Fi Pentesting Expert (HTB CWPE) is coming to anyone looking to advance their network hacking skills.
The community has been waiting for this one, so we are happy to give you a rundown of what you can expect. For those familiar with our certifications, you’ll see a similar pathway to success, but we know you’ll be interested in what we’ve included.
If you’re new to this area of security (and our certifications), welcome along for the ride. Let’s talk about why this pathway gives you what you need to grow.
Changing the way you learn Wi-Fi pentesting
This is a pathway many of our community members have been waiting for! So, we wanted to make sure to bring you something you’ll be able to interact with off the rip.
What does that mean? All cloud-based testing environments for capturing handshakes, cracking keys, and deploying evil twins. No equipment is needed.
You’re going to be learning from the perspective of a modern insider threat. That means learning to operate with techniques utilized by adversaries to bypass physical perimeter controls and work with newer Wi-Fi standards (WPA3).
And don’t worry, the coverage that this pathway and certification offer will bring you up to speed with a comprehensive overview of each skill that should be in your toolkit. All while focusing on industry-relevant scenarios that provide a strong backbone, your future teammates will appreciate.
But why would you choose to be a Wi-Fi pentester?
A world that runs on Wi-Fi
Wi-Fi and general accessibility to an access point in any metropolitan or suburban area are common. You can plop down in most places and find SSID (ex: FBIVAN) sitting there staring at you.
You’d have to be out in the woods, or really trying to distance yourself from society, to find yourself marooned from a way to connect to a network.
But have you ever been curious about what information is floating past the defenses of those tiny bastions? For your sake, and others?
Since it’s woven into our daily lives and businesses, there are always assurances we will need that those aspects of our lives are locked down. Here are some great examples!
The rules we follow and how they benefit the Wi-Fi hacker
The payment industry at large! Anyone who stores, processes, and/or transmits cardholder data.
No, your typical owner of a mom-and-pop coffee shop doesn’t need to run network pentests, but that little payment portal they have (Square, Toast, Clover, Stripe, etc) sitting at the register, they do.
Which brings me to Payment Card Industry Data Security Standard (PCI DSS). A global standard that requires wireless pentesting to be done to be compliant.
Specifically:
-
11.1/11.2.1: Test for the presence of wireless access points: You must test to find and detect any unauthorized wireless access points in your cardholder data environment at least quarterly.
-
11.1.1: Maintain an inventory of authorized wireless access points: You need to maintain a documented inventory of all authorized wireless access points and the business justification for each.
-
Incident Response Plan: Your incident response plan, specified in Requirement 12.9, must include what steps to take if a rogue wireless access point is detected.
The gallery of people responsible for following this standard includes processors that handle the payment transactions themselves, the institutions that issue payment cards, and banks that process that information.
Explore HTB for financial institutions
Those 3rd party providers are just a fraction of entities charged with the onus of financial security. Here are more incredibly dry (but important, shout out to Policy Village <3) standards!
Just kidding.
We were going to run down a couple more of the compliance standards that cover the backbone of medical and banking institutions, but what you're probably really looking for is coming up next…
What you will learn while training for the HTB CWPE
So, every certification starts with finishing the job role path. In this case, we have compiled a collection of modules that begin with the fundamentals of Wi-Fi pentesting, but explore the various ways attacks occur on robust networks.
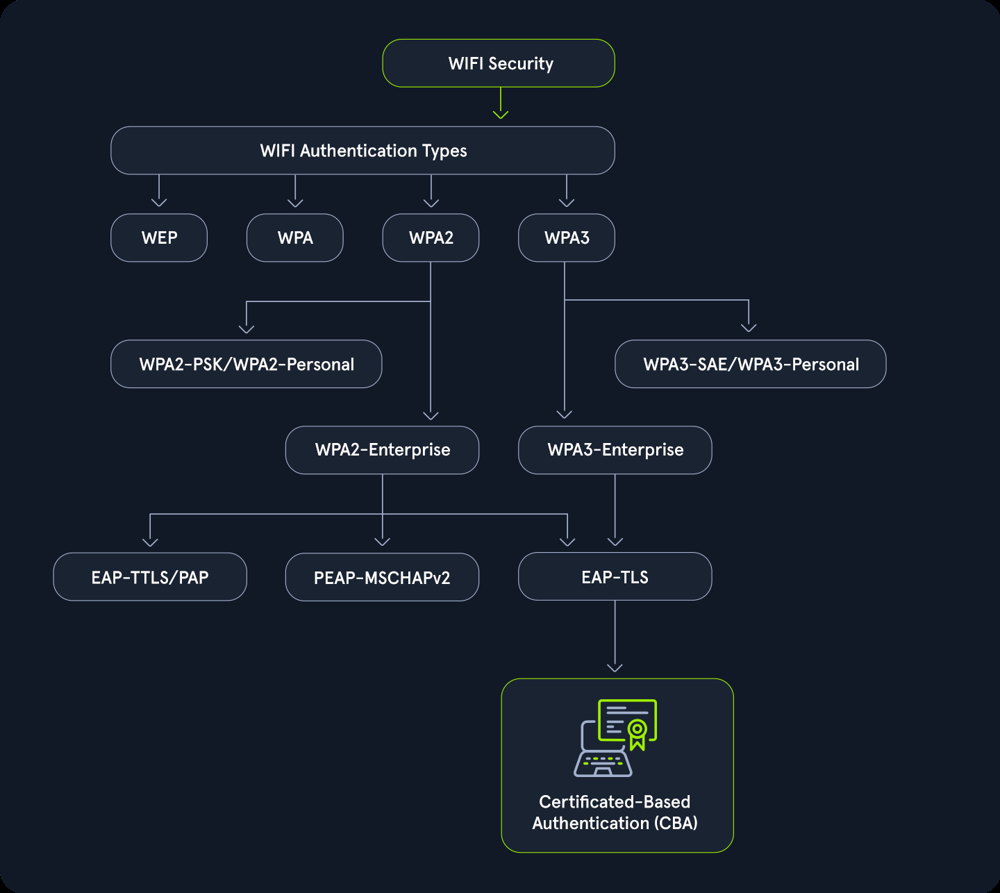
Modules contain hands-on content, so be prepared to become an active participant in learning:
-
Wi-Fi Penetration Testing Basics
-
Attacking Wi-Fi Protected Setup (WPS)
-
Wired Equivalent Privacy (WEP) Attacks
-
Attacking WPA/WPA2 Wi-Fi Networks
-
Wi-Fi Evil Twin Attacks
-
Attacking WPA3 Wi-Fi Networks
-
Bypassing Wi-Fi Captive Portals
-
Wi-Fi Password Cracking Techniques
-
Wi-Fi Penetration Testing Tools and Techniques
-
10. Attacking Corporate Wi-Fi Networks
In turn, here’s what you will stand to learn by following this path:
-
Understand the fundamentals of wireless networking.
-
Identify and differentiate between Wi-Fi security protocols.
-
Enumerate and exploit legacy Wi-Fi features (WPS)
-
Perform reconnaissance to detect Wi-Fi networks and hidden SSIDs.
-
Capture and analyze Wi-Fi traffic using Wireshark and other packet analysis tools.
-
Exploit common misconfigurations and weaknesses in wireless networks.
-
Execute advanced attacks on WPA2 and WPA3 networks.
-
Conduct Evil Twin and Rogue AP attacks.
-
Assess and bypass captive portal implementations.
-
Demonstrate downgrade and handshake-based attacks to extract or crack Wi-Fi credentials.
-
Perform and optimize Wi-Fi password cracking using multiple tools and methods.
-
Integrate multiple tools and techniques to automate the attack against Wi-Fi networks.
-
Learn how to pivot from a Wi-Fi foothold to internal network resources.
-
Complete a simulated corporate Wi-Fi attack chain.
-
Build confidence in executing a full Wi-Fi penetration test lifecycle.
By the end, we want to turn your fascination with access points and networking into a specialization that is globally recognized.
Prerequisites: A basic understanding of TCP/IP, Wi-Fi usage, and Linux command line is assumed. The path will refresh some essentials, but it moves quickly into practical exercises. No prior wireless hacking experience is required—this path will take learners from ground zero to an advanced level in Wi‑Fi pentesting.
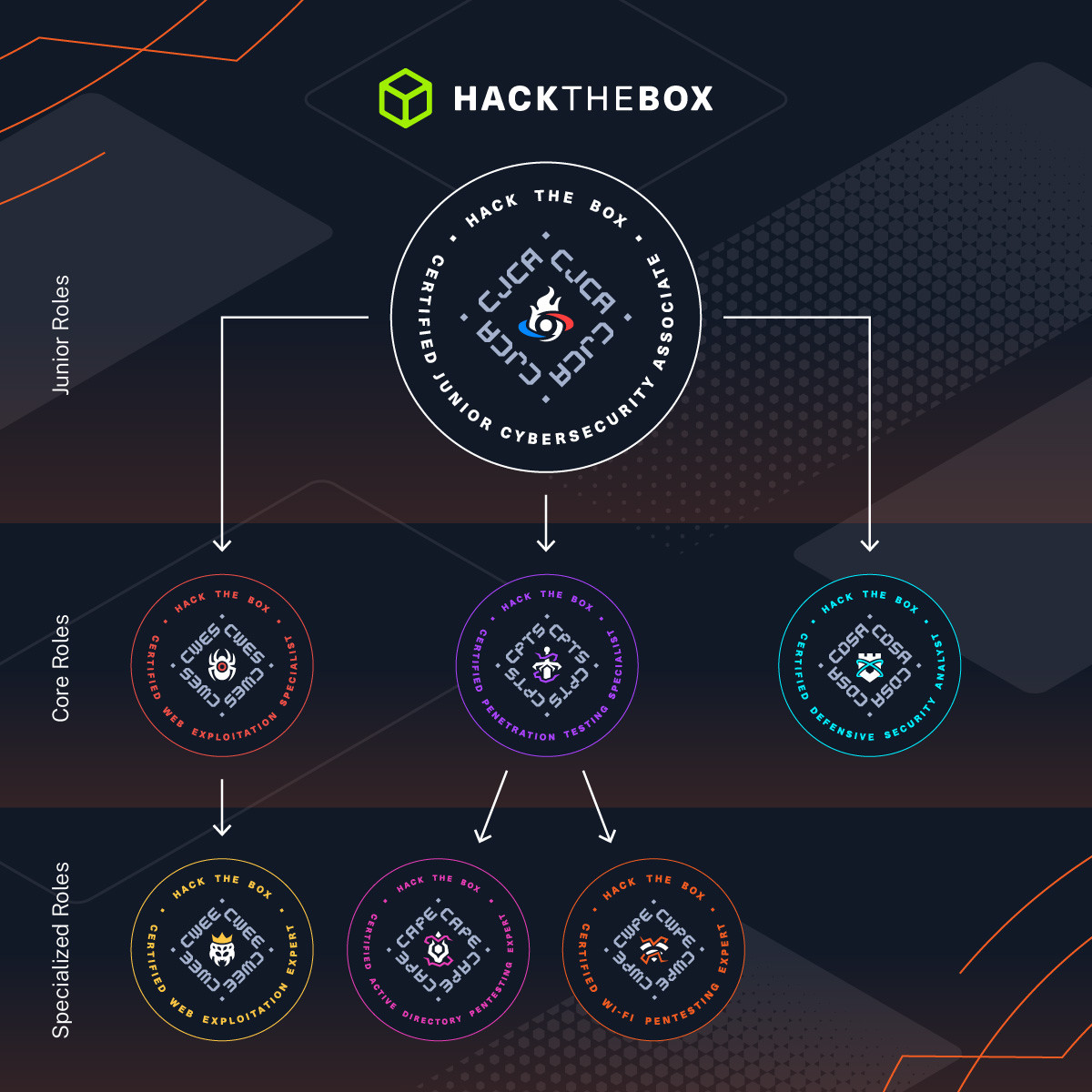
How do I start?

To take the HTB CWPE certification, you’ll first need to complete the full Wi-Fi Penetration Tester Job Role Path. This ensures you walk into the exam with the exact skills the assessment expects.
No surprises, no guesswork, and no wasted attempts.
Once the pathway is marked as 100% complete, the certification will unlock automatically in your account. From there, you can use a certification voucher to begin your examination.
The Wi-Fi Penetration Tester Job Role Path includes Tier III modules, which means you can access it through:
-
The Gold Annual subscription for users on HTB Academy (includes pathway + voucher)
See if the Gold Annual plan is for you
-
The Grow plan and above for businesses that already have an account with us
If you’re already on one of these plans, you’re good to go. Just finish the pathway, use that voucher, and dive into the exam!
If not, upgrading gives you immediate access to everything you need to train, prepare, and sit the certification from start to finish.
Get your team equipped for Wi-Fi engagements
How the exam works

1. Get your voucher
Once you’ve completed the full job role path, you’re officially eligible to sit for the certification. From there, you can pick up an exam voucher—each one comes with two attempts. If the first try doesn’t go your way, don’t stress. You’ll get detailed feedback and guidance to help you sharpen things before attempt number two.
2. Enter the exam and begin your pentest
After you’ve got your voucher, head to exams → exam Information → enter exam to start.
The moment you enter, you’ll see everything you need:
-
Your exam lab access
-
Deadlines for both the lab and your report
-
Reminder emails (so nothing slips past you)
You’ll receive a Letter of Engagement outlining the scope, requirements, and objectives, plus a report template to follow.
The lab is yours for 7 full days, with no restrictions. You’ll also submit flags through the exam page as proof that you’ve fully exploited each required vulnerability.
Every candidate gets a dedicated instance, meaning no interruptions, no cross-traffic, and the freedom to reset the environment whenever you want.
Tip: Start taking notes early. Draft your report as you go. Future-you will thank present-you.
3. Upload your report
Your job now is to professionally document every finding and the remediation advice using the provided template. You have 7 days from the moment you enter the exam to upload your final report.
If you’ve taken the Documentation & Reporting module, you’ll recognize the structure, note everything, map out your attack chain, and make it clean and clear.
4. Receive your results
An HTB Academy instructor will check your points first, then give your report a detailed review. If everything meets the quality bar, congratulations, you’ll earn the certification.
You’ll get your results within 20 business days. Once you pass, you can immediately claim your digital certificate. A physical certification package is also in the works (and yes, it’ll have that signature HTB flair).
Learning to see the world in a whole new way
Wi-Fi pentesting isn’t just a niche offensive trick or something only network admins care about. It’s one of those rare skills that cuts across most corners of security.
If you work in IT, you’ll touch wireless. If you’re a blue teamer, you’ll defend it. If you’re a red teamer, you’ll absolutely target it.
And if you’re a team looking to grow your skill pool, Wi-Fi upskilling will add a new dimension to your team's lethality.
Build your curiosity about the Wi-Fi Penetration Tester job role path and HTB CWPE into a valuable global skillset.
It teaches you how networks actually behave outside the comfort of a lab. It forces you to understand misconfigurations, weak auth flows, careless deployments, and how attackers think when they pivot through the airwaves instead of the wire.
Turn curiosity into skills today















