Security 101
Our top 5 DFIR labs for beginner analysts (to get good fast)
Sherlocks are powerful blue team labs for security analysts looking to quickly develop threat-landscape-relevant DFIR skills. In this post, we put together our top picks for beginners.
Table of Contents
When it comes to developing strong Digital Forensics and Incident Response (DFIR) skills, many blue teamers want more practical hands-on content.
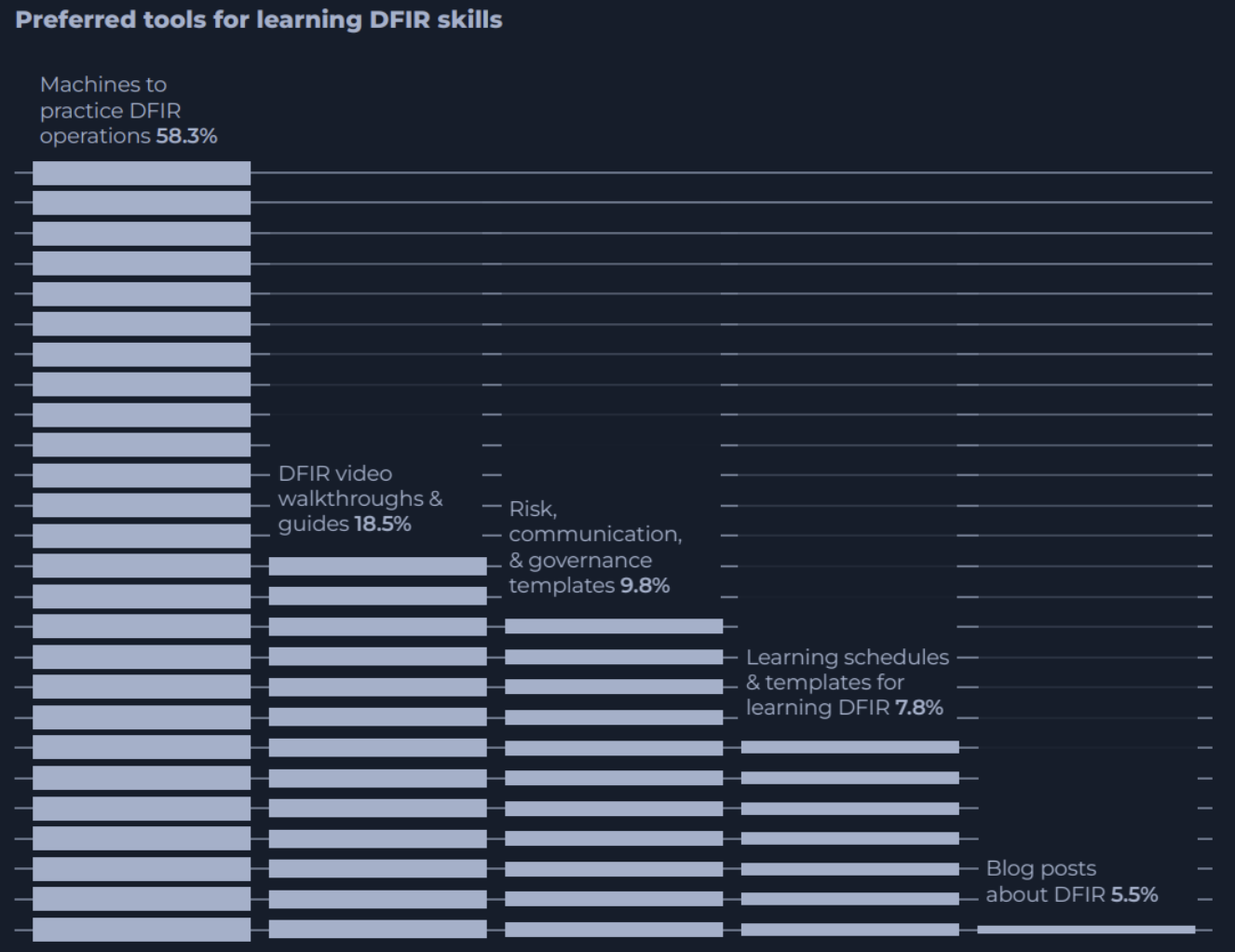
In our 2023 report on the critical skills for modern SOC analysts, over half (58.4%) of participants ranked practical Machines (instances of vulnerable virtual machines) as the best way to improve their DFIR skills.
This is one of the main reasons why it is so exciting to add our new investigation-based defensive security scenarios to HTB Labs: Sherlocks.
What are HTB Sherlocks?
Sherlocks are meticulously crafted environments that offer realistic, gamified investigation labs for defensive security professionals. Through these blue team labs, defenders can quickly improve their DFIR capabilities.
Sherlocks are part of the Dedicated Labs offering. This means challenges are based on a fully functioning simulated corporate environment. You’ll be presented with artifacts or supporting materials of some kind, and then tasked with answering a series of questions.
Completing these challenges builds a deeper understanding of defensive security tools and methodologies—enabling blue teamers to prioritize information during real investigations and level up their technical analysis.
More about our SOC analyst report
We interviewed 400 cybersecurity professionals to discover what skills are required to be a modern SOC analyst and the future trends in the industry.
Play these 5 DFIR labs to upskill faster

Meerkat: A realistic taste of DFIR

You’re the new security provider for Forela, a fast-growing startup. The startup has been using a business management platform but has insufficient documentation and potentially lax security practices.
You are provided with PCAP and log data and are tasked with determining if a compromise has occurred.
Meerkat is one of our most popular Sherlocks to date. And it’s easy to see why when you consider the critical topic skill the lab focuses on teaching: analysis.
As a guardian of the network, you’ll get a realistic taste of the pivotal role cybersecurity plays in the protection of any business as you sift through network data and logs to detect signs of intrusion.
Skills you’ll learn:
-
Network traffic analysis and interpretation: Use tools like Wireshark and log analysis applications (e.g., Timeline Explorer) to analyze PCAP files and Suricata/Zeek log files. This helps you identify malicious activity and develop an eye for “normal” versus “suspicious” network behavior.
-
Identification and analysis of cyber attacks: Learn to tell techniques like credential stuffing apart from other brute-force methods by analyzing the nature of login requests and credential pairs.
-
Vulnerability identification and CVE research: Identify vulnerabilities exploited in an attack such as authorization bypass, RCE, and then research relevant CVEs to understand the attack vector and affected versions.
Bumblebee: Database forensics & malware analysis

Step into the role of a DFIR specialist and trace the steps of an external contractor who breached Forela's internal forum.
This easy Sherlock tests your ability to work with forum logs and an SQLite3 database dump. You’ll unravel how the perpetrator exploited the Guest WiFi to steal administrative credentials.
Skills you’ll learn
-
Database forensics: Examine SQLite databases to identify unauthorized modifications, user activities, and extraction of sensitive information.
-
JavaScript malware analysis: Get familiar with the behavior of malicious JavaScript code embedded in web pages to steal credentials.
-
Lightweight Directory Access Protocol (LDAP) integration security: Boost your knowledge of securing LDAP integrations within applications to prevent credential compromise and unauthorized access.
Litter: Sniff out suspicious network protocols & tunneling

Khalid has just logged onto a host that he and his team use as a testing host for many different purposes. It’s off their corporate network but has access to many resources in the network.
The host is used as a dumping ground for a lot of people at the company, but it’s very useful, so no one has raised any issues.
Little does Khalid know that the machine has been compromised. And company information that should not have been on there, has now been stolen.
Your mission? Figure out what has happened and what data has been compromised.
Network protocol analysis is front and center in this exciting Sherlock. Prepare to identify suspicious protocols such as unauthorized data exfiltration or tunneling activities.
Skills you’ll learn:
-
Wireshark for cyber investigations: Use Wireshark to dissect network traffic, follow UDP streams, and analyze communication between hosts for signs of compromise.
-
Data decryption: Work with tools like Cyberchef to decrypt hexadecimal values and uncover attacker commands and tools used during an attack.
-
DNS tunneling tool identification: Ability to recognize specific versions of DNS tunneling tools used by attackers for data exfiltration.
Related read: How to learn cybersecurity for free.
Logjammer: Level up your Event Log analysis

You have been presented with the opportunity to work as a junior DFIR consultant for a big consultancy, Forela-Security. Before going any further, however, they’ve assigned you a technical assessment to complete.
The consultancy would like to gauge your knowledge of Windows Event Log analysis. Please analyze and report back on the questions they have asked.
Logjammer will help you get good at navigating and analyzing Windows Event Logs. Including System, Security, Windows Defender, Windows Firewall, and PowerShell operational logs to trace user activities and system changes.
Skills you’ll learn:
-
Firewall rule analysis: Analyze firewall event logs to identify modifications made to firewall settings, including creating new rules and their directions (inbound/outbound).
-
Audit policy changes: Detect changes in audit policies through security logs and identify specific policy subcategories that were altered.
-
Malware detection and response: Use antivirus event logs to identify malware threats, analyze antivirus actions (e.g., quarantine), and understand the implications of PowerShell commands executed by users.
Tracer: Practice advanced incident response techniques

A junior SOC analyst on duty has reported multiple alerts indicating the presence of PsExec on a workstation. They verified the alerts and escalated the alerts to tier II.
As an incident responder, you triaged the endpoint for artifacts of interest. Now please answer the questions regarding this security event so you can report it to your incident manager.
Related read: How to detect PsExec and lateral movements
Timestamps, key files, service binaries, and much more…Tracer is a treat for you sophisticated SOCs looking to push your skills to the limit.
Skills you’ll learn:
-
Service binary identification: Identify binaries dropped by tools like PsExec that allow attackers to execute remote commands.
-
Timestamp analysis: Determine the specific times at which certain activities occurred (this is crucial for timeline reconstruction in incident response).
-
Named pipe analysis: Read named pipes for inter-process communication, often used by malware for lateral movement, through event logs and Sysmon data.
Want to learn the theory first?
HTB's Certified Defensive Security Analyst (CDSA) certification will build your knowledge and practical skills to get you “job ready”.
The knowledge I've gained from CDSA has already helped me on the job.
Recently I was able to directly apply techniques I learned from the CDSA exam on a real incident. This led to the uncovering of artifacts that were an integral part of the investigation. This is a testament to how realistic the exam truly is.
Security Analyst and CDSA first blood winner, Jamie Dumas.
The certification deepens your expertise as you progress and aligns with skills currently sought in SOC analyst roles. You’ll hone your ability to analyze, respond to, and mitigate cybersecurity threats—preparing you for the dynamic challenges of a SOC environment.
The final exam, which is graded by a team of seasoned security professionals, verifies your real-world defensive security skills for critical roles and will support your journey to becoming a SOC analyst or cybersecurity engineer.
|
Author Bio: Sabastian Hague (sebh24), Defensive Content Lead, Hack The Box Sabastian Hague is a seasoned cybersecurity professional with over eight years of experience in the field. After serving in the Royal Air Force as a specialist in all things SOC, he went on to work for Vodafone's global CERT team before taking on a role as a senior security consultant with SpiderLabs and working on numerous high-profile incidents. He is now the Defensive Content Lead at Hack The Box. Seb has numerous industry certifications, including GIAC Certified Detection Analyst (GCDA), GIAC Continuous Monitoring Certification (GMON), GIAC Certified Incident Handler (GCIH), GIAC Certified Intrusion Analyst, Offensive Security Certified Professional (OSCP), Blue Team Level 1 (BTL1), Blue Team Level 2 (BTL2), Cybereason Threat Hunter (CCTH). |
|
Author bio: Kyser Clark (KyserClark), Cyber Defense Operations (1D771), United States Air Force (Active duty) Kyser is a Cyber Defense Operations leader with over five years of active duty U.S. Air Force experience specializing in offensive security, ethical hacking, penetration testing, and red teaming. His credentials include a Bachelor of Science (BS) in Cybersecurity Management & Policy from the University of Maryland Global Campus (UMGC), and 11 industry certifications: OffSec Certified Professional (OSCP), (ISC)² Certified Information Systems Security Professional (CISSP), eLearnSecurity Junior Penetration Tester (eJPT), EC-Council Certified Ethical Hacker (CEH), Cisco Certified Network Associate (CCNA), CompTIA PenTest+, Cybersecurity Analyst (CySA+), Cloud+, Linux+, Security+, and Network+. Kyser encourages you to connect with him in these places in cyberspace: |















