CISO Diaries
CISOs: Win your “board's blessing” with this reporting template
Learn how to correctly report cybersecurity performance to the board using our free board reporting toolkit!

Mags22,
Apr 29
2024
Table of Contents
As a CISO, your job is to help the board understand three things:
-
What are the risks to our business?
-
How well are we managing those risks?
-
Are those risks costing us money?
However, the link between cybersecurity risk and overall business risk isn’t always crystal clear to non-technical leaders.
You can bridge this gap and gain the support and investment you need, with effective board reporting.
Sample CISO board report template 👇
An example of an CISO board report created by the HTB team. Use it as a template for your next report!
CISOs face job loss & jail time for poor reporting
Suppose a CISO can’t provide evidence of the security posture they’ve built. Then, they are one breach away from being fired should something go wrong. (They could even face jail time in extreme cases.)
Connecting security strategies and measures to an org’s financial performance means CISOs avoid scrambling to prove their worth in the face of a breach.

What’s more, if CISOs want board investment and backing, they need to demonstrate the value of their cybersecurity team.
Reporting data to the board provides visibility and ensures alignment of security with the organization's business strategy.
Ken Underhill, CISO and multi-award winning and international best-selling author of Hack the Cybersecurity Interview.
Effective board reporting not only covers the CISO’s back, but also boosts investment in cybersecurity and overall security posture. This ensures alignment between all departments that work with the security function.
Timothy Martens, CISO at T.M. cyber consultancy, shares the following important benefits of board reporting:
-
Provides a deep understanding of cybersecurity risks and mitigation strategies.
-
Enhances diversity and fresh perspectives.
-
Facilitates cybersecurity-driven business advantage.
-
Translates complex cybersecurity issues for the board.
The role of the board vs. the CISO
Effective board updates boil down to knowing how your day-to-day responsibilities as a CISO differ from the board’s priorities.
A board provides general oversight of operations without involvement in day-to-day operations. Boards can be more future-focused, while the CEO and management concentrate on day-to-day challenges.
The board may provide direction on what assets to secure and initiatives to explore. But the CISO will implement and create a security strategy.
For example, the board could prioritize the protection of critical intellectual property, customer data, or operational infrastructure.
CISOs must then work with various stakeholders to create a plan to protect the organization’s most vital assets and a strategy to implement this plan.
This could involve hiring new talent, upskilling their team, gaining input from stakeholders, and implementing the overall cybersecurity strategy.
What should a CISO board report cover?
Every CISO’s approach to cybersecurity board reporting can differ slightly. But it’s hard to go wrong with a risk-based approach, as it:
-
Explains the rationale behind focusing less on lower-risk areas.
-
Directs the board’s attention to high-risk priorities.
-
Justifies your current strategy.
A CISO’s board report should include a high-level overview of the threat landscape, an overview of security incidents and mitigation strategy, how we're ensuring compliance, current security investments, and their effectiveness, etc.
Ken Underhill, CISO and multi-award winning and international best-selling author of Hack the Cybersecurity Interview.
But every organization is different, with boards having a variety of unique priorities. Timothy Martens, CISO at T.M. cyber consultancy, highlights key questions to ask yourself before deciding what to include in your board report:
-
What are our top business priorities, and how can information security support them?
-
What is our risk appetite for cybersecurity threats, and how does it align with our overall risk management strategy?
-
How can we ensure that our employees are aware of their cybersecurity responsibilities?
-
What is our cybersecurity budget, and is it sufficient to protect our critical assets?
-
How are we monitoring our security posture and measuring the effectiveness of our security controls?
-
What is our incident response plan, and have we tested it?
-
Are we compliant with all relevant regulatory and industry standards, and what steps are we taking to maintain compliance?
-
How are we addressing emerging cybersecurity threats, such as ransomware and phishing attacks?
-
How are we partnering with third-party vendors to ensure a high level of security when relying on their services?
-
What investments are we making in cybersecurity innovation, and how can we use emerging technologies to enhance our security posture?
By tailoring your board report to business priorities, you’ll only further highlight how aligned your cybersecurity strategy is with business goals.
What (even smart) CISOs get wrong with board reporting

The board has limited time to read reports, so CISOS must be proactive to improve receptivity. Common mistakes include being too technical and only discussing the problems, without offering solutions:
The biggest thing is being too technical in the reporting. Some board members might have a tech background, but all understand the language of business.
Focus on metrics and tailor your reporting based on what the board wants to know about. They don't need to know every single security thing going on.
Ken Underhill, CISO and multi-award winning and international best-selling author of Hack the Cybersecurity Interview.
Another common mistake Timothy discusses is reporting on the wrong thing. This ties back into understanding what’s most important to the board and business goals.
A lot of CISOs are focused on showing numbers to the board. But is that really how you measure your security program?
Showing them phishing statistics, or the number of incidents, will not add any real value, unless they are mapped to business outcomes.
If you want to succeed at the board level, you need to speak their language. Think strategically and in business terms.
Translate complex risks to human language where they can make a proper board decision strategy.
Timothy Martens, CISO at T.M. cyber consultancy
So, what cybersecurity metrics should your board report focus on?
-
Preparedness.
-
Security incidents.
-
Cost per incident.
-
Time to detection and mitigation.
Reporting on these domains describes your security posture and program in a concrete way. You’re able to map security measures to business outcomes. This is a must-have for winning the board’s “blessing” for new investments and initiatives.

CISO cybersecurity reporting best practices

1. Avoid the technicalities
Don’t waste time diving too deep into the technical details.
Instead, speak directly about what the board cares about: the organization’s security posture and avoiding costly risks.
This aligns with what your cybersecurity team offers as a function of the business.
Data security, Information security, and information risk is a business risk issue. Not a technology issue. Technology doesn’t have risk. Security doesn’t have risk. Businesses have risk.
Steve Katz.
2. Focus on the right metrics
Your board of directors aren’t necessarily interested in what the most common cyber attacks are. They care more about how long it takes you to respond and how much this costs the business.
These key business outcomes include revenue, reputation, and trust with customers. Focus on these metrics to help guide your KPIs.
3. Give enough context
Don't just list out a ransomware attack but talk about the potential business impact of such an attack.
Ken Underhill, CISO and multi-award winning and international best-selling author of Hack the Cybersecurity Interview.
To encourage support from the board, discuss not only the dangers of ransomware but what this means for the business financially. Example:
We could face prolonged system outages, disrupting our core operations and bringing revenue-generating activities to a grinding halt. Based on our current daily revenue figures, even a temporary shutdown of 48 hours could result in losses upwards of $200,000.
But you can go a layer deeper with the level of context you supply, also discussing reputational damage, which can have longer-lasting effects than a dip in revenue.
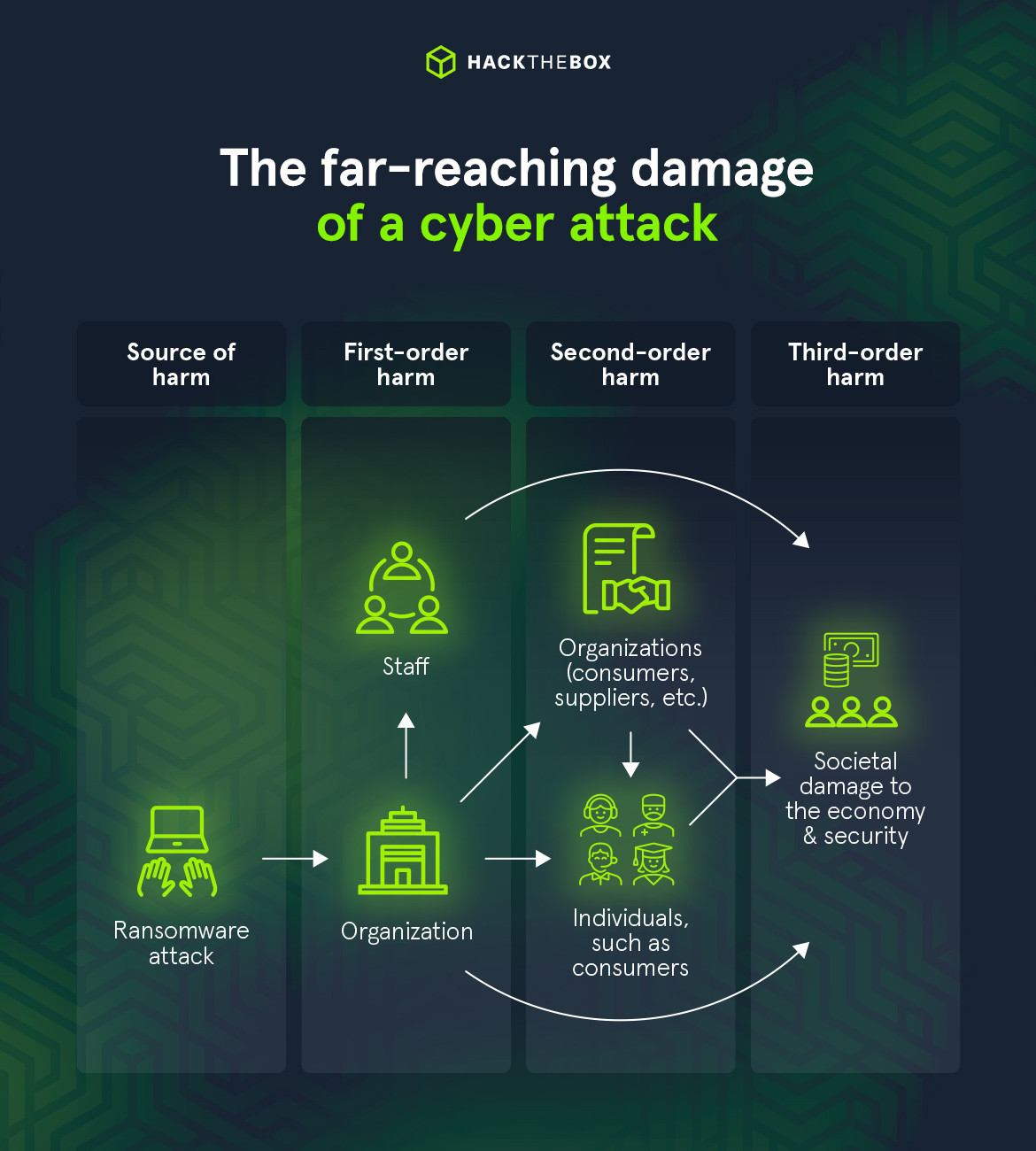
Help the board visualize the impact of a cyber attack, by discussing first, second, and third-order harms:
-
First-order harm: Damage to the organization and staff (financial, reputational, physical harm).
-
Second-order harm: Damage to organizations or individuals indirectly caused by the incident. This includes the erosion of customer trust, employee anxiety, and potential shifts in organizational culture.
-
Third-order harm: Damage to the wider society, including financial and security.
By showing how dangerous the cycle can become, the board will have enough context to appreciate the gravity of a seemingly “minor” incident.
4. Come prepared with solutions
It’s hard to be heard when you only discuss problems, not solutions. As a CISO, your role involves constant communication of problems. Including solutions to those problems in your board reports makes gaining buy-in from leadership easier.
Be ready to offer actionable recommendations to the board. For example, if your security team is constantly rectifying the impact of phishing attacks employees have fallen for, show them your proposal for setting up a cybersecurity awareness training program.
When presenting your solutions or proposals, crunch the numbers and have projections ready. Can you translate the reduction of successful phishing attacks into increased product security, better compliance, or a smaller attack surface?
5. Prove the ROI of cybersecurity by embracing the power of “I told you so”
Revenue and loss are the language of the board. Some key figures to report on include:
-
Financial loss due to security incidents.
-
Regulatory fines.
-
Compliance revenue (deals won or lost due to meeting regulatory requirements).
-
Cost per incident.
By reporting on these financial figures, you’ll quickly prove the ROI of cybersecurity. As the right strategy and budget will minimize these issues.
If the board is unable to support you in certain areas, you can always refer to past reports. Timothy Martens coined this using the power of “I told you so.”
The power of CISO board reports
Both CISOs and the board are responsible for cybersecurity. With public companies required to disclose any material cybersecurity incidents, and brand reputation relying on keeping data safe, no one can push cybersecurity aside.
But there’s a lingering disconnect between the technical world of a CISO and the board’s focus on profit. When a CISO bridges this gap, the payoff is huge. Everyone benefits from the increased support that comes from aligning cybersecurity strategy with business goals.
That’s why your board report should always aim to answer the three vital questions:
-
“How secure are we?”
-
“Are we losing money?”
-
“Do we meet regulatory and compliance requirements?”
Do this right, and you’ll have everything you need to build your team and implement a water-tight cybersecurity strategy.
Become an HTB Subject Matter Expert

Are you a cybersecurity professional who wants to contribute to articles like this one?
Join the HTB SME program and you’ll benefit from the following:
-
A huge audience: Our HTB community has over 2.7 million members, giving you a huge platform to share your knowledge with and feature in our editorial content.
-
Networking opportunities: Meet other HTB SMEs and expand your professional network, meeting people you may never have connected with if it wasn’t for your involvement with HTB.
-
Recognition: Any insights you provide will be credited to you, including your name, title, and LinkedIn profile. Some content will get additional love on social media too!
-
Share your experiences: We’re giving a voice to cybersecurity professionals, providing you with a platform to share your knowledge and experiences.
-
Help others: Your unique insights are incredibly valuable to other cybersecurity professionals, or even individuals just starting their careers.
💡Find out more on our blog: Become an HTB Subject Matter Expert
|
Dan Magnotta (Mags22), HTB Federal Business Development & Capture Manager, Hack The Box Dan Magnotta is an accomplished professional in cybersecurity and intelligence operations with more than a decade of experience in the military and private sectors. His career began with dedicated service to the U.S Department of Defense, where he played critical roles in the U.S. European Command and U.S. Special Operations Command Europe, contributing significantly to cutting-edge cyber strategies. In addition to his civilian role, he serves as an LCDR in the U.S. Navy Reserve, showcasing his leadership and dedication as an Executive Officer for a Navy Reserve Unit. His expertise in cybersecurity, operational analysis, and strategic planning is extensive. At Hack The Box, he tailors solutions to meet the unique requirements of government agencies and organizations worldwide, leveraging his deep understanding of both military and civilian cybersecurity needs. |















