Artificial Intelligence
Ni8mare fuel: Chaining n8n CVEs for full compromise in automated workflows
Dive into Ni8mare (CVE-2026-21858) and CVE-2025-68613—two critical n8n bugs that chain into unauthenticated RCE. See the exploit in action and practice on our new BloodFlow machine.
Any modern security team today loves a bit of automation—almost as much as attackers do. Tools like n8n promise to glue systems together, orchestrate workflows, and make everything faster, smoother, and more scalable. Unfortunately, as history keeps reminding us, complex automation platforms also come with complex attack surfaces.
That’s when the Ni8mare begins. Pause for dramatic effect.
In this post, we’re going to break down CVE‑2026‑21858 and CVE‑2025‑68613, why they matter, and how chaining them turns a helpful workflow engine into an attacker’s playground. We’ll also introduce BloodFlow, a shiny new Hack The Box Machine designed to help you relive (and vanquish) the nightmare in a safe setting instead of in production.
TL;DR
-
n8n versions before 1.65.1 contain critical flaws that can be chained for full system compromise.
-
CVE‑2026‑21858 (Ni8mare) allows unauthenticated arbitrary file reads via a Content‑Type confusion bug.
-
Attackers can extract encryption keys and databases, forge admin JWTs, and gain full control.
-
CVE‑2025‑68613 enables a JavaScript sandbox escape which leads to remote code execution.
-
Fear not—BloodFlow is here. This is a hands‑on HTB machine that simulates the full exploit chain end‑to‑end.
Table of Contents
- TL;DR
- What makes n8n a high‑value target?
- CVE‑2026‑21858 (Ni8mare): Content‑Type confusion
- From file read to admin: JWT forgery
- CVE‑2025‑68613: Escaping the JavaScript sandbox
- Full compromise, zero magic
- Meet BloodFlow: Step back into the Ni8mare (safely, in a lab)
- Why all this matters for your AI security
- Final thoughts on Ni8mare
What makes n8n a high‑value target?
n8n sits at that oh-so-awkward intersection of automation, credentials, and logic. Enterprises are relying on it more and more to orchestrate agentic workflows that touch multiple systems, from CRMs and databases to internal APIs and cloud services. And because workflows can span so many layers, a single compromise can cascade across entire business processes.
What multiplies the risk is just how accessible n8n is. Even non-technical users can deploy production-ready workflows quickly, often without deep oversight, meaning sensitive operations or secrets may be exposed inadvertently. Attackers know this: gaining access to n8n can provide a shortcut to APIs, credentials, internal tools, and even core business workflows—essentially flipping the master switch on critical enterprise infrastructure.
From a threat-modeling perspective, n8n is as attractive as a siren in the high seas: high-value assets, broad access, and low deployment friction. For defenders, the implication is clear: vulnerabilities here carry outsized risk, and misconfigurations can be just as dangerous as software flaws.
CVE‑2026‑21858 (Ni8mare): Content‑Type confusion
The opening gambit is CVE‑2026‑21858, nicknamed Ni8mare for…somewhat obvious reasons.
This vulnerability springs from a Content‑Type confusion issue in n8n’s Form Webhook nodes. By taking advantage of the way requests are parsed, an attacker can trigger arbitrary file reads without authentication.
That’s already bad enough, right? But what makes it critical is what is in those files. Using this bug, an attacker can:
-
Read the n8n encryption key.
-
Extract the SQLite database storing credentials and user data.
-
Reconstruct sensitive internal configuration without ever logging in.
Think of it like clipping through the map and looting the endgame chest at level one.
From file read to admin: JWT forgery
Once the encryption key is out in the open, the rest of the process is scarily straightforward. In short: n8n uses JWTs for authentication. With the signing key in hand, an attacker can:
-
Forge a valid admin JWT.
-
Bypass authentication entirely.
-
Gain full administrative access to the platform.
At this stage in the game, defenders have already lost control of the room. But the story doesn’t end there.
CVE‑2025‑68613: Escaping the JavaScript sandbox
The next wave of the attack, CVE‑2025‑68613, has n8n’s JavaScript sandbox in its sights.
n8n allows user‑supplied JavaScript in workflows, packed up in a sandbox that should prevent dangerous behavior. This CVE exposes that the sandbox can be bypassed, allowing attackers to:
-
Break out of restricted execution.
-
Access Node.js child_process.
-
Execute arbitrary system commands.
In other words, we’ve gone from a harmless webhook to remote code execution. Enter, the reverse shell.
Full compromise, zero magic
Chaining these vulnerabilities results in:
-
Unauthenticated file read.
-
Credential and key extraction.
-
Admin token forgery.
-
Sandbox escape.
-
OS‑level command execution.
No zero‑days. No exotic exploit chains. Just small assumptions stacking up like a Jenga tower.
Meet BloodFlow: Step back into the Ni8mare (safely, in a lab)
Because the HTB team has your back always, we’ve just released BloodFlow. This is a Very Easy Linux machine that recreates this entire attack path in a controlled environment.
You’ll:
-
Exploit CVE‑2026‑21858 (Ni8mare) to read sensitive files.
-
Extract encryption keys and databases.
-
Forge admin JWTs.
-
Abuse CVE‑2025‑68613 to escape the JavaScript sandbox.
-
Achieve remote code execution and capture the user flag.
Along the way, you’ll get hands‑on experience with:
-
Content‑Type confusion bugs.
-
Arbitrary file read exploitation.
-
JWT abuse in real systems.
-
JavaScript sandbox escape techniques.
-
Chaining CVEs for full compromise.
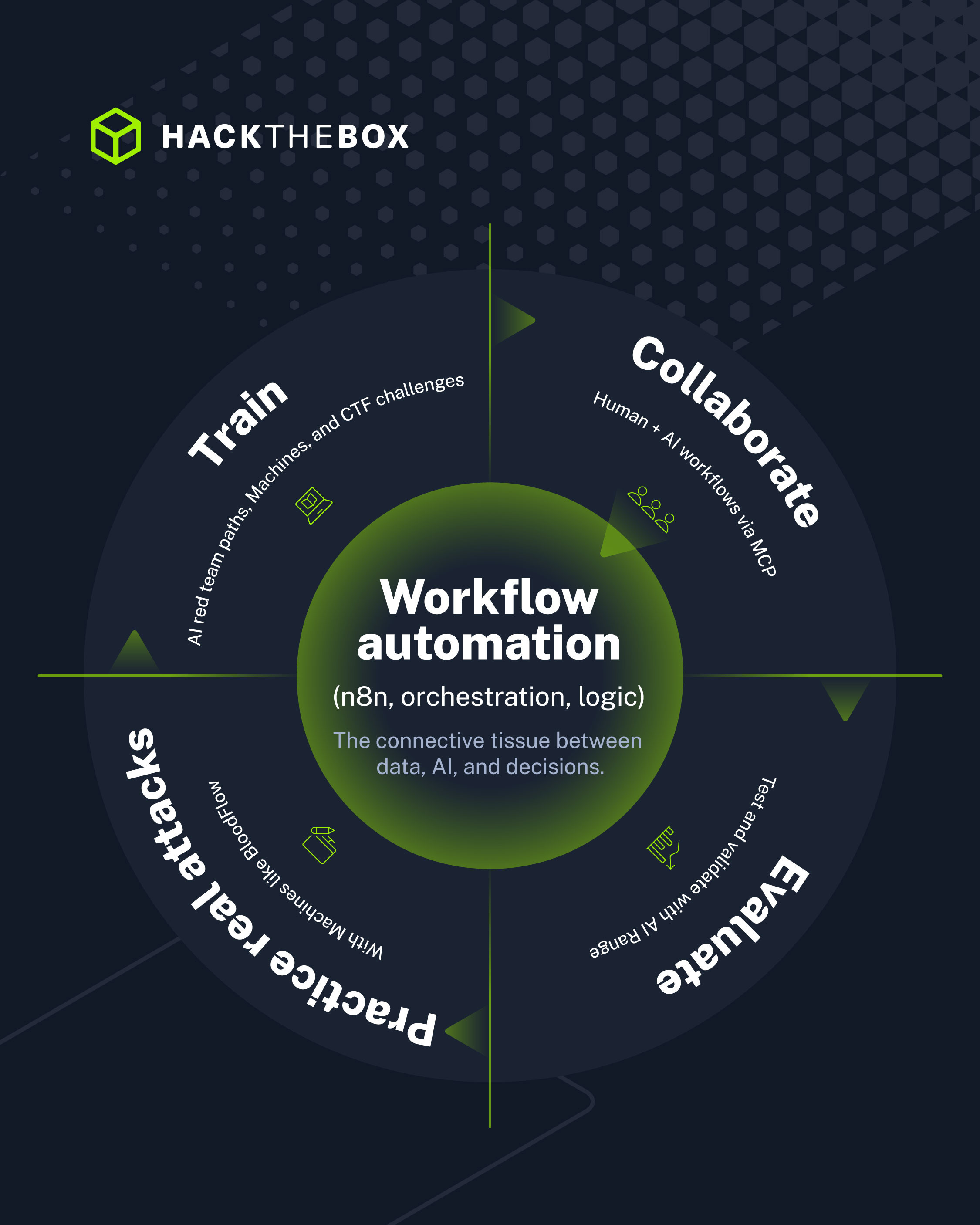
Why all this matters for your AI security
Workflow automation platforms like n8n are growing in popularity. They’re used to glue together things like AI pipelines, LLM calls, data preprocessing, and decision logic, which means vulnerabilities here don’t just threaten infrastructure. AI integrity, data leakage, and model abuse are very real risks.
Securing AI systems is not just about prompt injection or model alignment. It’s about the very real, very boring infrastructure that surrounds them. But that’s why everyone at HTB looks at AI security as a full lifecycle problem:
-
Training through AI red team paths, Machines, and CTF challenges.
-
AI + human collaboration via MCP.
-
Evaluation and validation using AI Range.
BloodFlow slots neatly into that strategy by highlighting exactly how traditional web and platform vulnerabilities can become AI‑scale nightmares.
Final thoughts on Ni8mare
Ni8mare isn’t scary because it’s clever. It’s scary because it blends in. It works quietly, predictably, and with very little friction.
So if you’re responsible for assessing, deploying, or defending automation and AI systems, this is a wake-up call. Ni8mare is precisely the kind of exploit chain you need to identify instantly, ideally before someone else weaponizes it.

















