Security 101
Mastering Nmap: Your ultimate cheatsheet for 2024 commands
Use our Nmap cheatsheet for essential commands including host discovery, network and port scanning, and firewall evasion.
Dimitris,
Apr 12
2024
Table of Contents
This post is based on the Hack The Box (HTB) Academy module (or course) on Network Enumeration with Nmap. The module teaches the fundamental skills needed for Nmap to perform effective network enumeration.
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
What is Nmap?
Network Mapper (Nmap) is an open-source network analysis and security auditing tool. It is designed to scan networks and identify which hosts are available on the network using raw packets, services, and applications.
Nmap can also identify the operating systems and versions of these hosts. It offers scanning capabilities that can determine if packet filters, firewalls, or intrusion detection systems (IDS) are configured as needed.
Every cybersecurity professional should use and understand Nmap to:
-
Gain visibility into networks: Paired with knowledge of network infrastructure and knowing which commands to use, Nmap provides a detailed view of a network’s landscape.
-
Assess targets during vulnerability assessment or pentests: Armed with OS and version data, you can pinpoint vulnerabilities specific to each host.
-
Make informed decisions to defend networks: Nmap empowers you to make informed choices—whether it’s tweaking firewall rules or fine-tuning IDS settings.
Haven’t used it yet? You can download it here.
💡Further reading: HTB’s 15 must-know Nmap commands in 2024. This blog covers how to use Nmap, top use cases, and some of the most essential commands.
Nmap commands cheatsheet for key use cases
Download our Nmap commands cheatsheet
Our Nmap commands cheatsheet PDF lists all of the essential commands, so you can quickly access them during your next scan.
Nmap is an essential tool for cybersecurity professionals to get comfortable with. Common use cases include:
-
Enumeration: uncover information including device types, reverse DNS (Domain Name System) names, MAC addresses, and IP addresses of all active hosts.
-
Auditing: survey the security aspects of a network.
-
Testing: simulate penetration tests using Nmap.
-
Find security issues: Scan servers and uncover paths attackers may use to exploit.
-
Detect vulnerabilities: Analysts and pentesters can use Nmap to detect vulnerabilities on the network.
-
Host discovery: discover live hosts within the network.
-
Identify open ports: Nmap conducts port scanning of target hosts.
-
OS version detection: discover the operating system (OS) and version of a target system quickly.
We’ve covered all of the commands you need to know, alongside their use cases below.
Learn Network Enumeration with Nmap
Nmap is an important part of network diagnostics and evaluation of network-connected systems. In this interactive module, we will learn the basics of this tool and how it can be used to map out internal networks by identifying live hosts and performing port scanning, service enumeration, and operating system detection.
-
An overview of Nmap.
-
Host discovery and port scanning.
-
Saving scan results.
-
Service enumeration.
-
Using the powerful Nmap scripting language.
-
Firewall and IDS/IPS evasion.
Types of Nmap scans
Nmap supports a whole host of scan types, however, the most common ones include:
-
TCP connect scans (-sT): Nmap sends a TCP packet to a port with the SYN flag set. This lets the user know whether ports are open, closed, or unknown. However, this isn’t the most reliable scanning method as firewalls can easily drop all incoming packets.
-
SYN scans (-sS): this scan is stealthier, as Nmap sends an RST packet, which prevents multiple requests and shortens the scan time.
-
UDP scans (-sU): this scan focuses more on speed over quality, working on the principle of “fire and forget”, rather than waiting for a returning handshake like the previous scans.
Host discovery
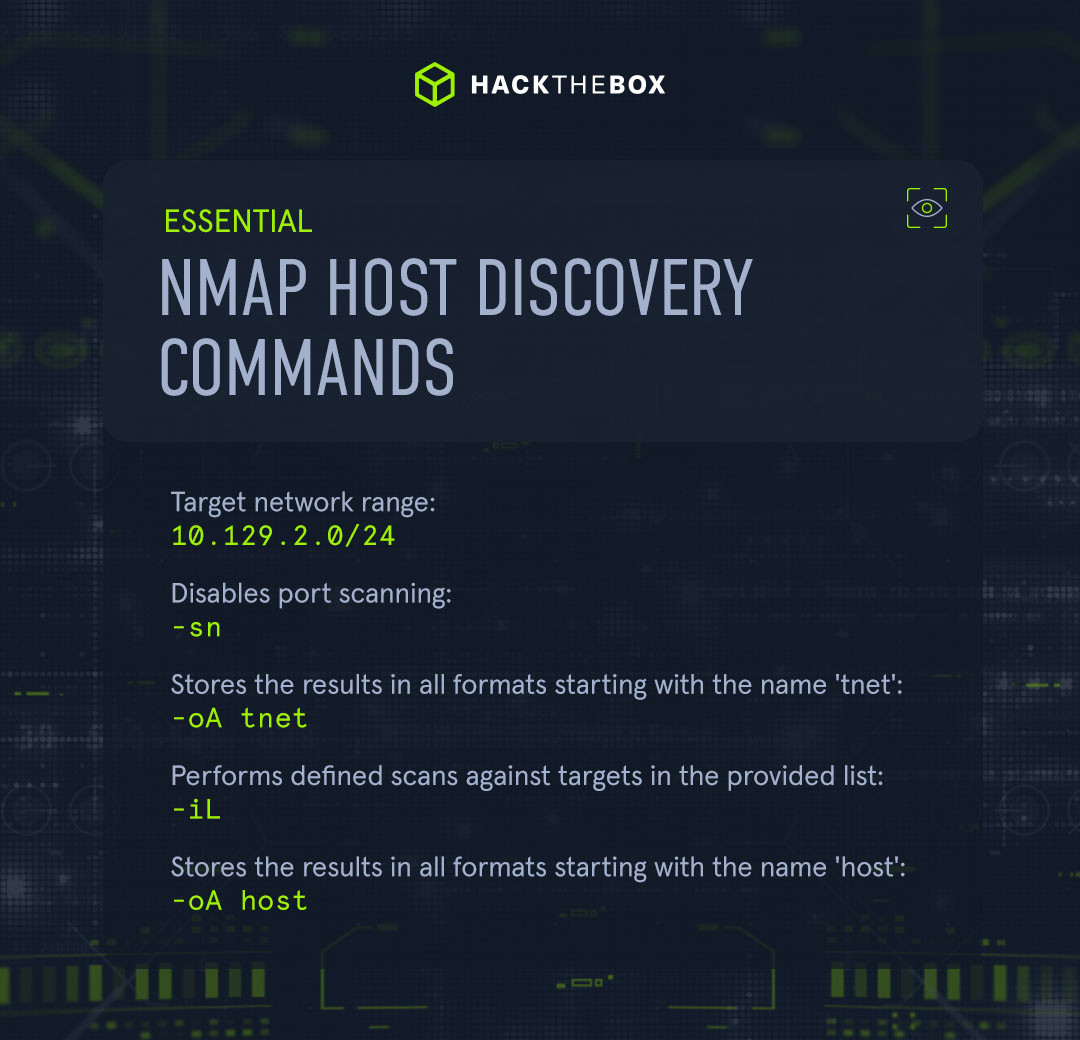
Host discovery is a key way many analysts and pentesters use Nmap. Its purpose is to gain an overview of which systems are online and some additional insight into how we can access these.
Here are the most essential host discovery Nmap commands:
|
Nmap command |
Description |
|
10.129.2.0/24 |
Target network range. |
|
-sn |
Disables port scanning. |
|
-oA tnet |
Stores the results in all formats starting with the name 'tnet'. |
|
-iL |
Performs defined scans against targets in the provided list. |
|
-oA host |
Stores the results in all formats starting with the name 'host'. |
|
-sL |
No scan but list targets only. |
|
-Pn |
Disables host discovery and only conducts a port scan. |
|
-PS |
TCP SYN discovery on the specified port. |
|
-PA |
UDP discovery on the specified port. |
|
-PU |
UDP discovery on the specified port. |
Service and version detection

When we enumerate using Nmap, determining the application and its version is vital. We can use this information to scan for known vulnerabilities and analyze the source code.
|
Nmap command |
Description |
|
-p- |
Scans all ports. |
|
-sV |
Performs service version detection on specified ports. |
|
tcpdump |
Analyze network traffic by intercepting and displaying packets |
|
Nc |
For reading and writing data between two computer networks. |
|
-A |
Enables OS detection, version detection, script scanning, and traceroute. |
OS detection
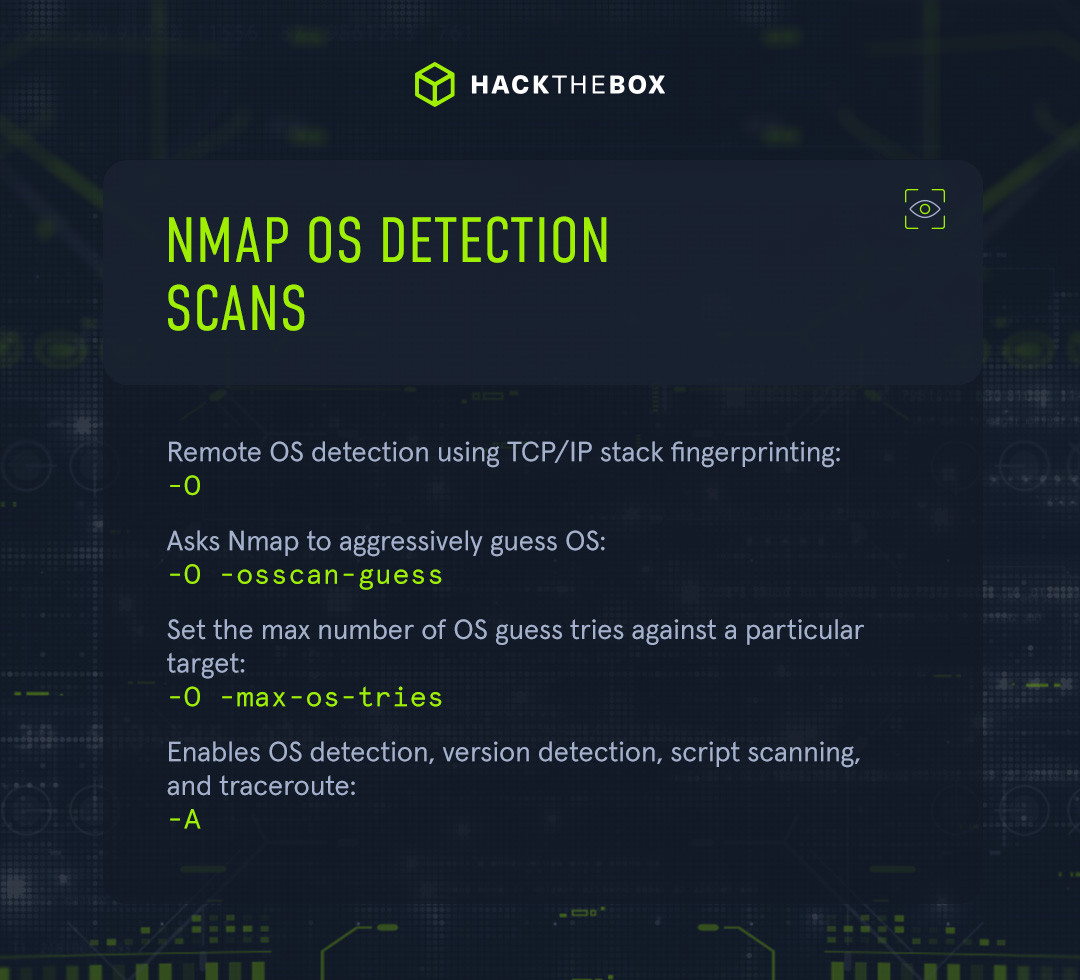
For more information during our Nmap enumeration, we may also want to discover what operating systems are being used.
|
Nmap command |
Description |
|
-O |
Remote OS detection using TCP/IP stack fingerprinting. |
|
-O -osscan-guess |
Asks Nmap to aggressively guess OS. |
|
-O -max-os-tries |
Set the max number of OS guess tries against a particular target. |
|
-A |
Enables OS detection, version detection, script scanning, and traceroute. |
Network and port scanning
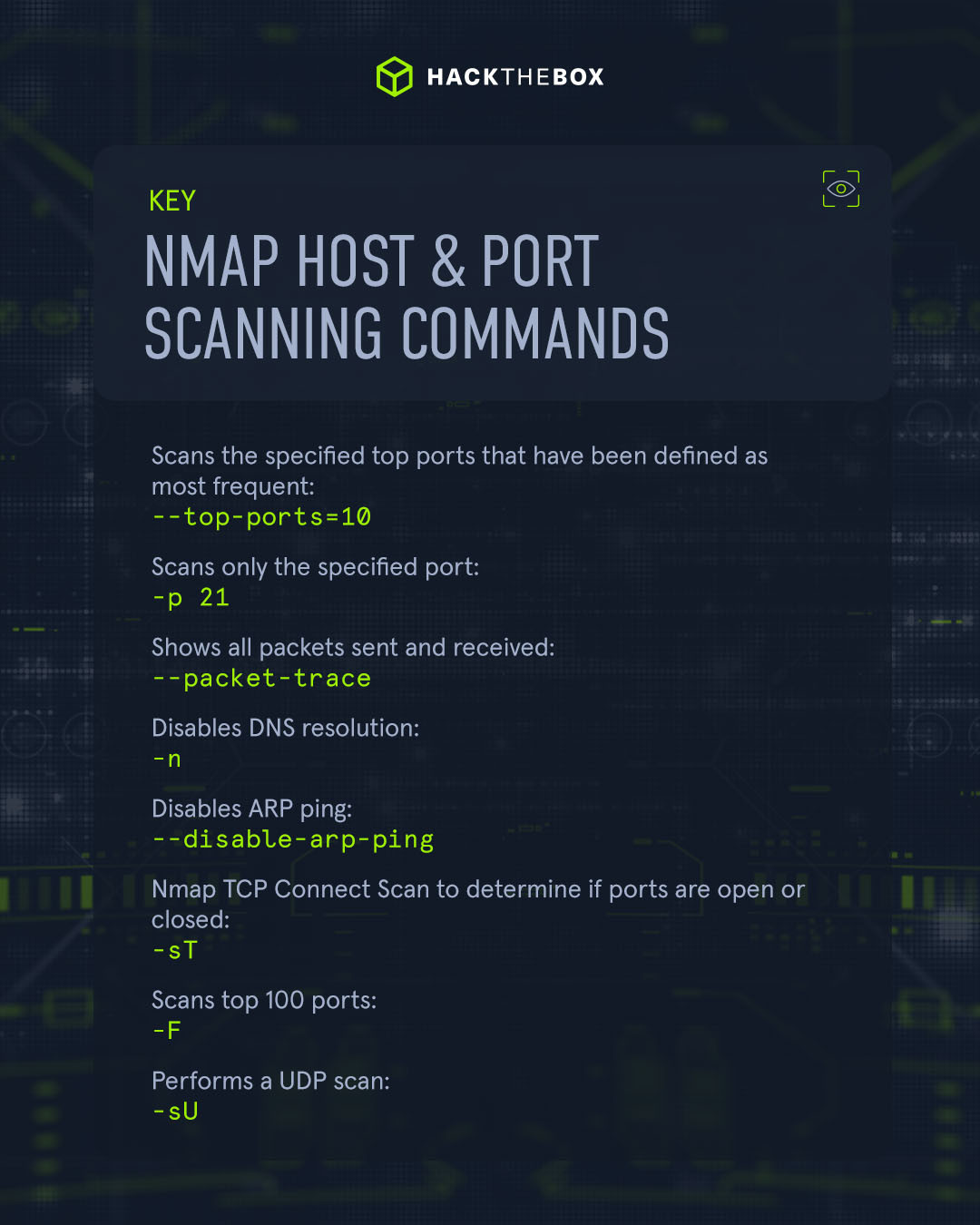
Once we’ve gathered whether a host is active or not, the next step is to understand what state the scanned port is in. There are six different states:
-
Open: a connection to the scanned port has been established.
-
Closed: the TCP protocol indicates that the packet we received back contains an RST flag.
-
Filtered: Nmap cannot correctly identify whether the scanned port is open or closed because either no response is returned from the target for the port or we get an error code from the target.
-
Unfiltered: the port is accessible, but it cannot be determined whether it is open or closed.
-
Open|filtered: this indicates that a firewall or packet filter may protect the port.
-
Closed|filtered: impossible to determine if the scanned port is closed or filtered by a firewall.
|
Nmap command |
Description |
|
--top-ports=10 |
Scans the specified top ports that have been defined as most frequent. |
|
-p 21 |
Scans only the specified port. |
|
--packet-trace |
Shows all packets sent and received. |
|
-n |
Disables DNS resolution. |
|
--disable-arp-ping |
Disables ARP ping. |
|
-sT |
Nmap TCP Connect Scan to determine if ports are open or closed. |
|
-F |
Scans top 100 ports. |
|
-sU |
Performs a UDP scan. |
Timing and performance

You can tweak Nmap’s timing and performance commands to run scans faster or slower based on your target or working environment.
This enables you to obtain the information you require most while adhering to certain timing constraints. This minimizes the risk of detection when performing a penetration test, for example.
|
Nmap command |
Description |
|
-T0 |
Paranoid (0) Intrusion Detection System evasion. |
|
-T1 |
Sneaky (1) Intrusion Detection System evasion. |
|
-T2 |
Polite (2) slows down the scan to use less bandwidth. |
|
-T3 |
Normal default speed. |
|
-T4 |
Aggressive (4) speed scans, which require a reasonably fast and reliable network. |
|
-T5 |
Insane (5) speeds scan, which requires an extra fast network. |
Generating reports (output)

When conducting any scan using Nmap, we’d always recommend saving your findings. This could be essential for later comparison, documentation, and reporting. After all, different tools may produce different results.
Here are some key commands to store your Nmap scans:
|
Nmap command |
Description |
|
-oN normal.file |
Normal output to the file normal.file. |
|
-oX xml.file |
XML output to the file xml.file. |
|
-oA results |
Output in the three major formats at once. |
|
-append-output |
Add a scan to a previous scan file. |
Firewall evasion

When conducting an Nmap scan, you’ll likely come across some security measures. To effectively perform a penetration test, for example, you’ll need to bypass these.
This is possible using the following commands:
|
Nmap command |
Description |
|
-sS |
Performs SYN scan on specified ports. |
|
-Pn |
Disables ICMP Echo requests. |
|
-n |
Disables DNS resolution. |
|
--disable-arp-ping |
Disables ARP ping. |
|
--packet-trace |
Shows all packets sent and received. |
|
-D RND:5 |
Generates five random IP addresses using decoy that indicates the source IP the connection comes from. |
Nmap scripting engine
Another handy feature of Nmap is the Nmap Scripting Engine (NSE). It provides us with the possibility to create scripts in Lua for interaction with certain services.
These scripts fit into the following categories:
|
Category |
Description |
|
auth |
Determination of authentication credentials. |
|
broadcast |
Scripts, which are used for host discovery by broadcasting and the discovered hosts, can be automatically added to the remaining scans. |
|
brute |
Executes scripts that try to log in to the respective service by brute-forcing with credentials. |
|
default |
Default scripts executed by using the -sC option. |
|
discovery |
Evaluation of accessible services. |
|
dos |
These scripts are used to check services for denial of service vulnerabilities and are used less as it harms the services. |
|
exploit |
This category of scripts tries to exploit known vulnerabilities for the scanned port. |
|
external |
Scripts that use external services for further processing. |
|
fuzzer |
This uses scripts to identify vulnerabilities and unexpected packet handling by sending different fields, which can take much time. |
|
intrusive |
Intrusive scripts that could negatively affect the target system. |
|
malware |
Checks if some malware infects the target system. |
|
safe |
Defensive scripts that do not perform intrusive and destructive access. |
|
version |
Extension for service detection. |
|
vuln |
Identification of specific vulnerabilities. |
Some useful NSE examples that you may use in your scans include:
|
Nmap command |
Description |
|
nmap -Pn -script=http-sitemap-generator scanme.nmap.org |
http site map generator. |
|
nmap -Pn -script=dns-brute domain.com |
Brute forces DNS hostnames guessing subdomains. |
|
nmap -script whois* domain.com |
Whois query. |
|
nmap -p80 -script http-unsafe-output-escaping scanme.nmap.org |
Detect cross site scripting vulnerabilities. |
|
nmap -p80 -script http-sql-injection scanme.nmap.org |
Detect cross site scripting vulnerabilities. |
Learn Nmap today
Nmap is an extremely powerful tool for all infosec professionals, whether you’re using it to protect your network or perform penetration tests, these commands are essential for all cybersecurity professionals to have at hand.
However, it’s important to not only rely on tools to do your job. You need to also understand how and why these tools work and what the information you find actually means.
Ready to dive in?
Find out everything you need to know about Nmap with our Academy module:
|
Author bio: Dimitrios Bougioukas (Dimitris), Senior Director of IT Security Training Services, Hack The Box Dimitrios has extensive experience in upskilling the IT security teams of Fortune 100/500 tech companies and government organizations. He enjoys analyzing the threat landscape as well as interpreting market and data analytics to assist Hack The Box in devising its training strategy and roadmaps, from go-to-market all the way to the syllabus level. Prior to Hack The Box, Dimitrios directed the development of training and certifications through eLearnSecurity/INE and was behind certifications like eCPTX, eWPT, and eCIR. You can connect with him on LinkedIn here. |















