Customer Stories
Enable powerful purple team security ops with HTB Enterprise
A detailed breakdown of how one savvy team tackles purple team security and upskills both red & blue teams.

Table of Contents
Training security teams to learn from one another is critical. Only a finite amount of time surrounds daily operations, and it should be treated as a valuable resource. So, when should training fit in?
How do you maximize the opportunity for individual growth, naturally foster an environment for purple teaming, and utilize our Professional Labs as a powerful team development intervention (TDI)?
In proper hacker fashion, the security team at Easi (European IT services partner) continues to take advantage of Hack The Box’s (HTB’s) Professional Labs to upskill its red and blue team.
If you’re even remotely interested in learning how to get more out of your HTB subscription for offensive or defensive security training, learn from Easi’s example below! 👏
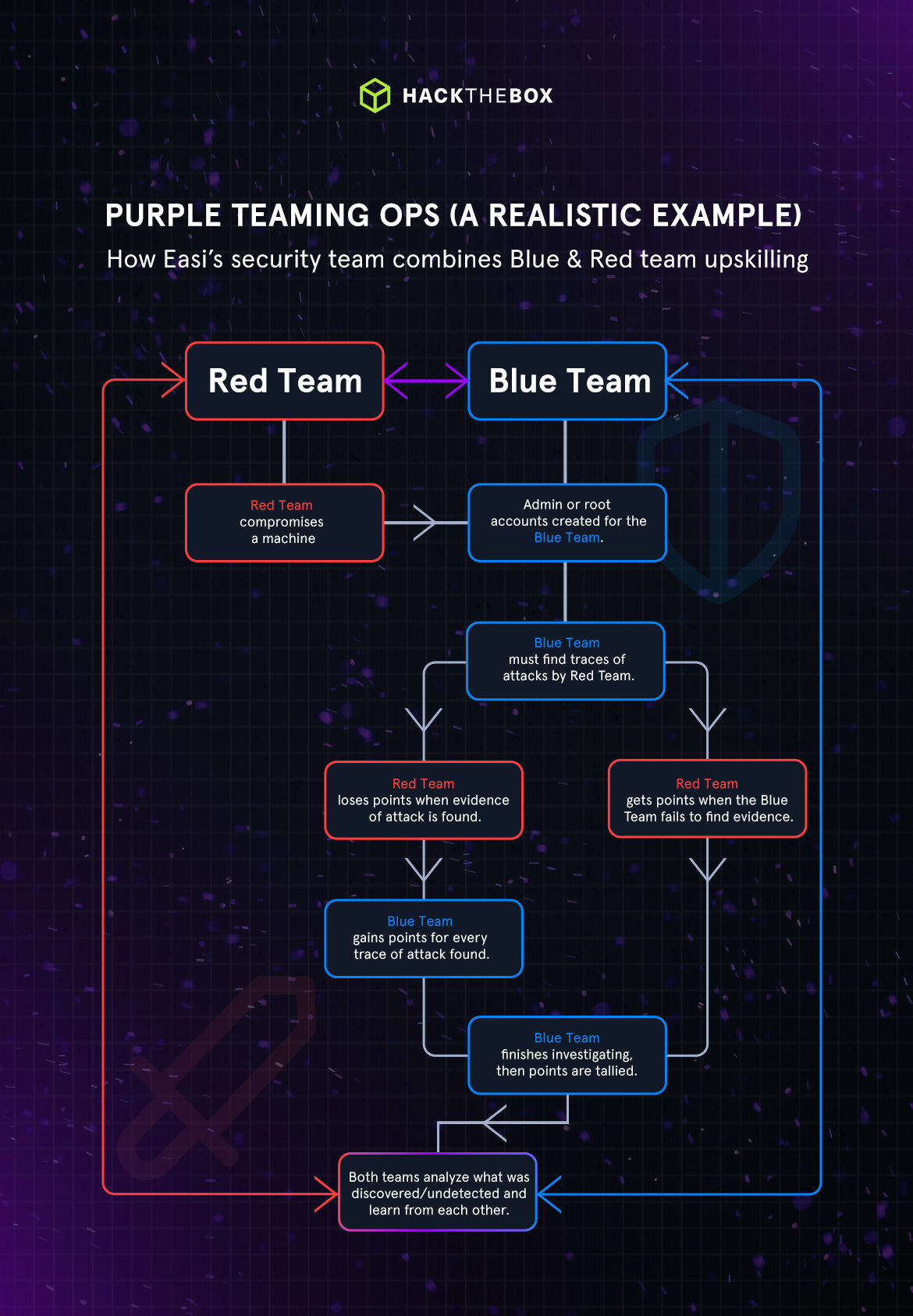
Purple team security path on Dedicated Labs
We’ll show you how Easi adapted Professional Labs to meet their purple team use case.
If you want to incorporate a similar approach and unite training for both blue and red teams, check out our new Purple Team Security Path on Dedicated Labs.
It combines offensive and defensive Machines, Challenges, and Sherlocks. And gives your team a firm grasp on the fundamentals of purple teaming.
Add this path to your lab and enable your team to exploit as well as detect, mitigate, and respond to cyber threats.
How to get started: Reach out to your account manager to get started, or click the button below to learn more.
Purple team security and TDIs
First, let’s define TDI in relation to purple team security practice.
A strong part of me disengages when I think about corporate “team building exercises.” The idea of pizza parties and trust falls begins to cloud my mind, and I lose perspective on the point of it all.
However, a TDI should stand as an activity embedded in the common flow of work to develop the immediate competencies and processes of a team (whether they’re red or blue).
It should solidify a practice that enables growth in a team’s ability to:
-
Debrief together.
-
Assist in reporting insights to senior management.
-
Provide accountability through the transparency of actions taken during the engagement.
The practical application and reflection of both a red/blue team’s methods should be a shared experience, not isolated to their own playbooks.
Easi accounted for this union of observable results by creating their TDI: A friendly competition that serves as a purple teaming activity. Both teams get to learn and practice both offensive/defensive security in a live environment.
They have incorporated the competitive spirit at the heart of this industry into their skills development with Professional Labs.
💡 Recommended read: Teaching security teams to think outside the box.
The red v.s. blue battle zone (powered by Professional Labs)
Here’s how Easi starts that cyber exercise.
First, they choose a Machine that everyone in the red team has compromised, attackers ensure they have initial access, do their privilege escalation, add the machine to their C2 framework, and have a backdoor.
Then, administrator or root accounts are created for the blue team. Blue teamers must investigate the Machine to find all traces of attacks conducted by the red team.
The blue team gains points for every trace of an attack they discover, which also causes the red team to lose points. Conversely, the red team is awarded points when the blue team fails to uncover an attack.
This scoreboard is central to simulating the competitive blue vs. red theme.
Who’s keeping score?
Using Professional Labs as a battle zone has produced a friendly rivalry between the two teams—four (4) offensive security pros and six (6) security professionals. If the blue team finds the red team's persistence, ten points to them.
If the red team can evade detection, throw ten on the board for them.
The exercise isn’t just for fun. It’s a cautionary tale that teaches from both perspectives. What better way to solidify skills, learn coworking habits, and teach new lessons than learning the hard way?
A great example of this comes from one of Easi’s lead Cybersecurity Consultants, Mickey De Beats, as he shares one of his recent triumphs.
Mickey used a Sliver beacon (A C2 tool created by Bishop Fox) that would trigger an action he could take when the Windows Management Instrumentation (WMI) subscription for Notepad.exe was utilized. Essentially, when a new process of Notepad.exe is created, a beacon executable can be generated with Sliver.
Here’s the kicker: when the blue team went to demo their findings, Mickey observed the opposing team had been reporting their findings in none other than Notepad!
Ten Points to Mickey!
(The red team will leave some low-hanging fruit for newcomers on the blue team. But it’s made clear that the teams make time to joust at each other just to keep the spirit of their developing rivalry.)
💡Recommended read: How Easi decreased onboarding times by 40%.
Bridging the skills gap between red and blue teams
Going back to what I stated before, your team is busy, and we’d assume often. So, the question of balancing this purple team TDI in tandem with daily work upkeep came naturally.
What we learned is that setup for the red team is relatively easy. The Professional Lab is already set to be vulnerable. So, the red team will focus on getting their persistence set. This was chalked up to “not much work.”
However, the onus of responsibility primarily falls on the blue team.
Mikey De Beats informed us that, “The most time goes to the blue team. They take about a month a box, just to give them enough time next to their day-to-day workloads.”
(Paths on HTB feature a combination of Machines, Challenges, or Sherlocks focused on a specific cybersecurity skill set or function.)
Regardless of the time taken to work through the material, he mentioned something unique about the teams themselves:
What we’ve noticed is our red team is a little more advanced than our blue team. I believe that, at the moment, a lot of teams are at this stage—and it is very hard for them to train without having these dedicated environments. So, that is why they have more time to investigate and get a meeting to discuss their discoveries. It gives us time to explain how we (the red team) did something, and then reveal where blue teamers should be looking.
In essence, this timeline allows the blue team to not only practice their current understanding of security, but also develop a perspective guided by the red team’s level of experience. Which sits at the core of a purple team approach to collaborative learning.
Helping blue teams master threat methods & processes
Mikey makes a great point that coincides with the blue team’s plight:
Offensive tooling often drops more often and impacts the workload of security teams—not to mention it gives red teams an additional edge. So, giving the blue team a larger grace period is important.
Otherwise, forcing defenders to keep up with the rapid adoption of new offensive techniques wouldn’t be fair. But what tooling does the blue team get?
The process of discovery is often left to a third-party “tool” that ingests information, assesses, and relays threats for the blue team. They will often spend most of their time involved in handling digestible reports and working to correct vulnerabilities with other teams.
Not to knock having an understanding of such tools, but it restricts a critical activity that gives the attackers their edge—building something from scratch.
The Professional Labs environment put the blue team in a situation where their daily drivers weren’t an option. Which forced them to focus on methodology over tooling.
I think there’s just so much workload for them (blue team). So then, you’re only focusing on tooling, not really methodology. This is something that I appreciate about the Professional Labs, the fact you cannot use any commercial tooling.
So, they are focused on using their own scripts and stuff—anything they create without the use of an internet connection.
This makes them more focused on methodology and overall approach instead of ‘I will use this commercial tool that will give me everything.’ Instead, they have a sliver binary, and you’ll have to do some investigation.
There is definitely a valid argument to be made about including more existing security tech stacks in Professional Labs for the learning utility. This would benefit the blue team and give them an edge in their response.
Getting leadership buy-in for purple team ops
So, why choose Professional Labs over other HTB products? What value did teams convey to sway leadership’s favor? What are the real differentiators?
The major factor, if it wasn’t clear by now, is the involvement of the blue team.
A valued part of this TDI is leadership’s ability to watch and understand visible results. It allows for leadership to grow, too.
Security is already a relevant topic amongst C-suite executives and management. The activities Easi’s security teams are engaging in are providing a top-down view for other integral stakeholders to gain more insight into how their company’s security posture is developing.
There’s less room to imagine how your security budget is being spent when you can watch teams develop the skills they will use to secure your company.
Mickey believes this also doubles as a competitive business advantage for Easi.
“If we’re at an event and need to demo our technical expertise, we’re able to say: ‘Oh, look how we’re approaching red team versus blue team over at Easi,’ it’s just such a quick win. So, for them (management), the visibility outweighs the cost.”
Easi's leadership understands the importance of such training initiatives. By investing in these exercises, they not only boost their team's capabilities but also enhance their organizational resilience against threats.
This commitment to continuous learning and development sets Easi apart and positions them ahead of not only threats but also competitors.
360 team development with purple team simulations

Easi has taken a forward-thinking approach to cybersecurity training by using Hack The Box's Professional Labs for purple teaming and Team Development Interventions (TDIs).
Their innovative approach combines competition and collaboration to create a dynamic environment where red and blue teams can learn, evolve, and thrive together. This method not only enhances technical skills but also fosters a deeper understanding and respect for each team's unique challenges and perspectives.
The red versus blue team exercises are more than just training; they provide invaluable insights into attack and defense strategies, encouraging teams to think critically and outfox their opponent. By doing so, the teams are engaged. Learning is continuous, relevant, and directly applicable to their daily responsibilities.
Easi's model serves as a blueprint for other organizations seeking to empower their security teams. It's a testament to the fact that the most effective learning occurs not in isolation but in the midst of action, collaboration, and healthy competition.
|
Author bio: Jesse Rivera (JXoaT), Product Marketing Specialist, Hack The Box Jexx is a digital alchemist who weaves narratives at the crossroads of technology and creativity. Known for demystifying the enigma of infosec and translating cyberspeak into the common tongue, Jexx bridges worlds—connecting the dots between companies and the clandestine circles of hackers. In the nexus of binaries and prose, Jexx finds their home. Once a systems admin, with a slew of foundational certifications (CySA+, PenTest+, Security+, Network+), they began to write about their curiosity surrounding threat hunting—which led them to where they are today. Jexx has established roles at security companies like Vonahi, Cobalt, and HackerOne. Channeling an innate curiosity into crafting stories that resonate with the heart of the hacking community, Jexx uses videos, blogs, and graphics as tools to have some fun. He advises, if you’re curious, don’t wait. Investigate. Their favorite line is still a quote from Rear Admiral Grace Hopper, “It’s easier to ask forgiveness than it is to get permission. |
|
Author bio: Hassan Ud-deen (hassassin), Content Marketing Manager, Hack The Box Hassan Ud-deen is the Content Marketing Manager at Hack The Box. Combining thought leadership and SEO to fuel demand generation is his jam. Hassan's also fascinated by cybersecurity, enjoys interviewing tech professionals, and when the mood strikes him occasionally tinkers within a Linux terminal in a dark room with his (HTB) hoodie on. #noob. Feel free to connect with him on LinkedIn. |















