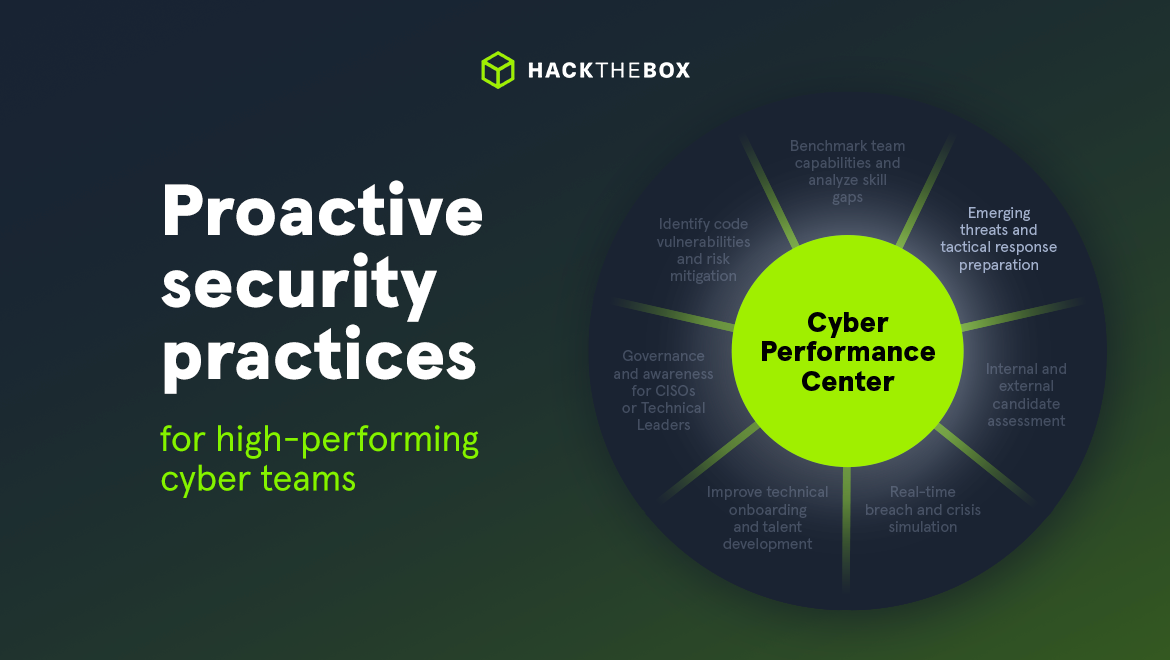
Cyber Teams
Proactive security tactics for high-performing cyber teams
Learn how to use Hack The Box to stay ahead of emerging threats and fully optimize your incident response plans.
Table of Contents
“How proactive is your security strategy?”
This seems to be the new hot question, with an emphasis on the keyword: proactivity.
The answer from many CISOs and executives to the above question isn’t exactly encouraging. 40% believe their organizations are poorly prepared to face a potential incident, breach, or crisis. Why so?
Basically, it all comes down to the time the cyber workforce takes to understand the threats they face, and how to deal with them. This requires:
-
Visibility. Insight on relevant threats that are emerging.
-
Prioritization. Knowledge of which threats to prioritize based on your unique attack surface.
-
Remediation. The skills and ability to identify and mitigate high-priority security risks.
HTB Enterprise Platform enables cyber teams to prepare for emerging risks and vulnerabilities that malicious actors exploit to compromise systems, data, or networks, while developing tactical response strategies to address them.
Uncertainty + complexity
Let’s think about it: cybersecurity incidents have become so common that when we experience service outage or downtime, many of us directly assume a cyber attack was behind it.
Oh, [insert business name] got hacked.
Security professionals are facing an increased feeling of uncertainty generated by attacks conducted with emerging technologies, which are making it difficult—now more than ever— to separate reality from fiction. An additional layer of complexity is now added by the growing trend in supply chain risks and the critical role of nation-state cyber crime, with over 60 countries staging elections throughout 2024.
Operation Shield Wall: A state-side cyber attack simulation
Jump into features realistic scenarios simulating procedures and protocols for large-scale incidents affecting critical infrastructure such as telecom networks, power grids, and federal services.

With our experience in providing security programs for more than 1,500 teams around the globe, we have identified the following challenges as the main obstacles for organizations to implement effective proactive security strategies:
Rapidly evolving threat landscape
New threats are constantly emerging. We are now experiencing an average of 1,900 critical Common Vulnerabilities and Exposures (CVEs) per month, with a 13% increase over 2023. Companies struggle to keep pace with evolving threats, leading to vulnerabilities and potential breaches.
Detection and response time
Timely detection and response are critical, but organizations may face delays in identifying and responding to emerging threats, increasing the risk of successful attacks. Currently, the remediation to an attack amounts to six days—against the four-day SEC rule—showing how attackers are outpacing defenders.
Integration of new technologies
New technologies, like AI and Machine Learning, are integral to modern cybersecurity. 2024 will likely see a rise in AI-based predictive social engineering and a disturbing convergence of AI and social manipulation techniques from attackers.
Meanwhile, defensive teams will use AI to automate detection, response, and support with predictive analytics. However, the truth is that many organizations may struggle with the integration and optimal utilization of advanced technologies for threat detection and response.
Based on our exclusive Cyber Attack Readiness report, a significant number of security teams are still not confident in handling blockchain and cloud-related tech, as solve rates for these challenges during our annual CTF competition for businesses are almost 30% lower than the average.
Based on this fundamental need from the industry to stay abreast of new tech, HTB Enterprise Platform offers a unique approach mapped to different technologies, environments, Operating Systems, and even use cases to ensure that no matter the technical infrastructure or tech stack, your cyber team keeps up with the latest CVEs & TTPs tailored to your unique attack surface.

Understanding CVEs and TTPs
CVE stands for Common Vulnerabilities and Exposures. Each CVE represents a unique identifier for a specific vulnerability or exposure, along with additional metadata such as a description, references, and solutions if available.
CVEs are used to track and manage vulnerabilities across different software and systems, allowing organizations to understand and mitigate potential security risks.
TTP stands for Tactics, Techniques, and Procedures. TTPs are used to describe the behaviors, strategies and methods used by an attacker to develop and execute cyberattacks on enterprise networks.
These two are the nemesis for every cyber analyst.
Understanding CVEs and TTPs in the shortest possible time can make a direct influence in the organizational business goals. Informed cyber professionals can proactively assess risk and drive effective decision-making by managers and executives.
Yes, sometimes it’s a race against time.
On HTB Enterprise Platform, cyber teams can practice newly discovered vulnerabilities or understand in depth TTPs before others with relevant hands-on scenarios simulating the specific attack vectors the adversary can potentially conduct to the infrastructure.
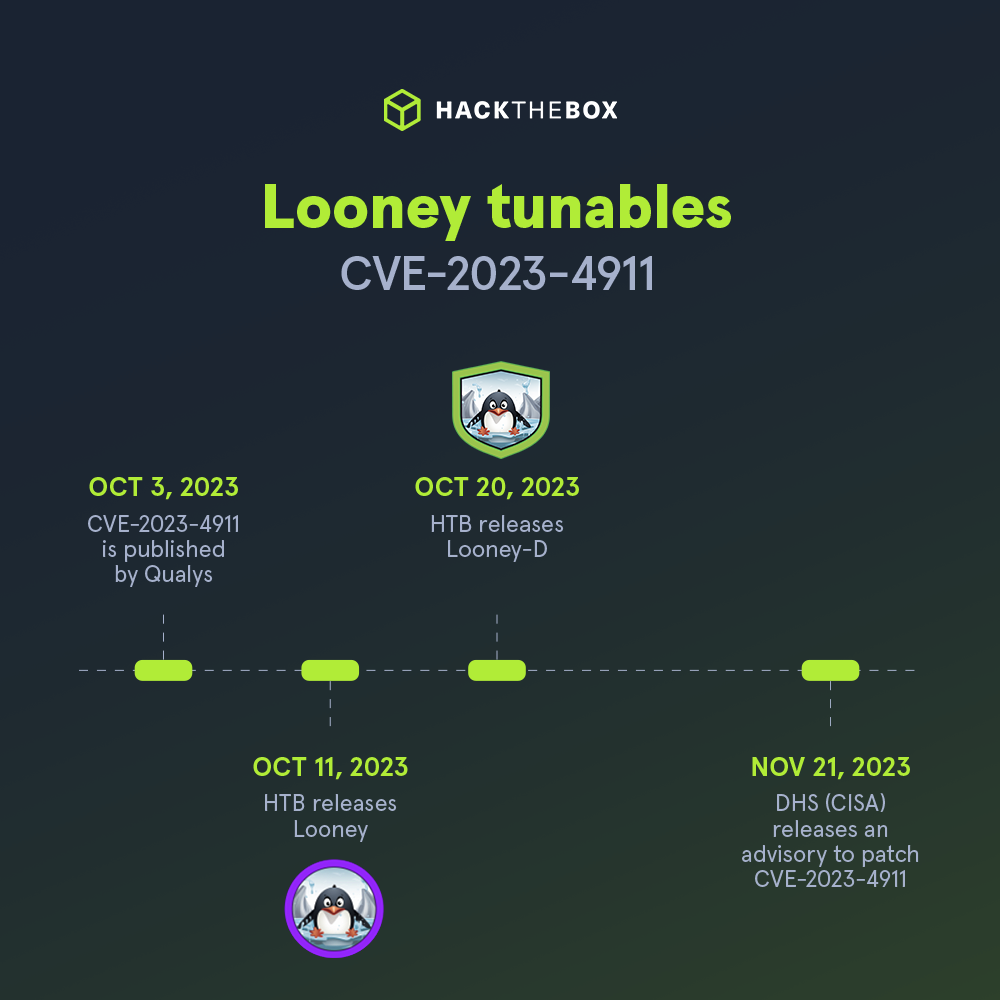
Let’s take the example of Looney Tunables. On October 3, 2023, Qualys announced their discovery of CVE-2023-4911 (otherwise known as Looney Tunables). The local privilege escalation vulnerability impacts the default installations of most major Linux distributions.
Within 10 days of the disclosure, a Machine replicating the vulnerability from the adversarial point of view was already available on HTB Enterprise Platform. The following week (October 20th) a defensive lab simulating the same attack path was released, providing HTB customers a complete view of the newly discovered CVE.
Cyber teams training with HTB had the chance to fully understand this critical vulnerability (and set proactive measures) before Homeland Security’s Cyber Defense Agency, even released the advisory to patch on November 21st, 2023.
HTB business customers can access a unique, and ever-expanding, pool of labs supporting them to make proactive security decisions:
CVE-based Machines
These labs, exclusive to business customers, are designed to mimic high-risk vulnerabilities and active threats exploited in the wild. Sometimes, they can be laser-focused on business logic vulnerabilities (e.g., misconfiguration in payment gateways, e-commerce exploitation, and more).
Searching and assigning CVE-based Machines is made easier than ever with our enhanced content categorization. Lab managers can easily search by CVE name or use the tags on each Machine to identify the scenarios to add to their team’s skills development plan.
D-logic Sherlocks
Blue team labs marked with -D are exclusive to HTB Enterprise Platform and offer a defensive view to offensive scenarios simulating the same CVEs or TTPs. This methodology is ideal to enable high-performing purple team operations!
Let’s take the example of MonikerLink vulnerability (CVE-2024-21413).
-
Moniker allows you to gain practical experience in exploiting the CVE, understand the insecure use of MkParseDisplayName() API, and learn how to handle links triggering the vulnerability.
-
Moniker-D prepares for attacks directed to valuable NTLM hashes to fortify the organization’s defenses and investigate security breaches to identify the attack path for an optimal vulnerability assessment.
The entire security team has the opportunity to work on the same attack scenario, getting to know in detail the risk and quantify the potential infrastructure damage based on the adversary’s behavior.
Threat connected job-role paths and certifications
HTB Academy course materials are mapped to the MITRE ATT&CK and NIST/NICE framework, making it easy for technical leaders to define a workforce development plan based on real-world techniques.
With job-role paths and certifications, cybersecurity staff have the opportunity to go through a threat-connected evaluation and become high-performing professionals ready to deliver all daily essential tasks.
Stop playing “catch up” with new technologies
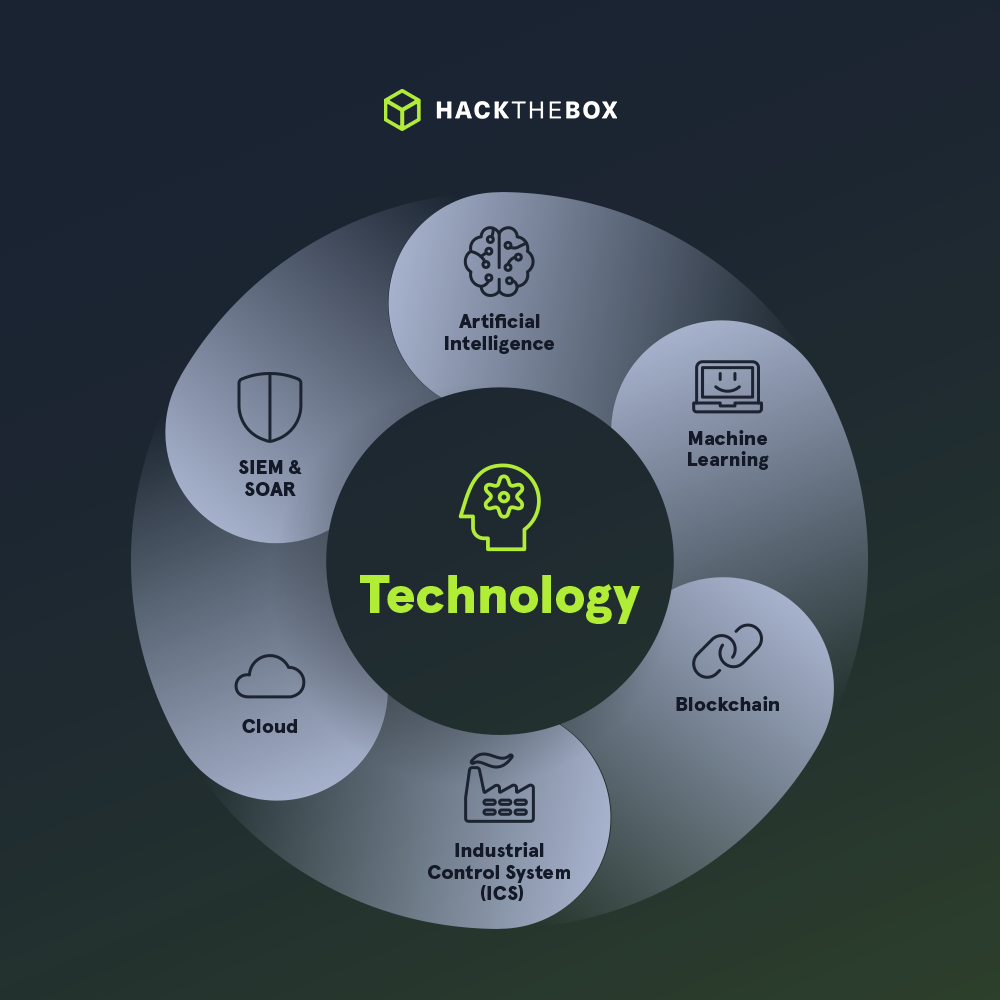
We've covered how HTB aligns your defensive & offensive security operations to emerging CVEs & TTPs. But what about new, cutting-edge tech that's not even on the radar for most defensive teams?
HTB Enterprise Platform builds threat-ready professionals by focusing on realism and providing a constantly updated supply of courses or labs covering the latest emerging technologies..
Only over the last couple of months, we provided technical leaders with:
-
A collection of hands-on labs focusing on Artificial Intelligence (AI) and Machine Learning (ML). Covering common attacks on AI/ML systems, insecure implementations, compromization of sensitive information, and more.
-
A new cutting-edge lab environment simulating AI bypass and exploitation and Blockchain exploitation in a simulated enterprise infrastructure.
-
A full ICS and SCADA security offering—from theoretical practice to enterprise simulation—highlighted by the latest release of Alchemy: Professional Labs scenario, replicating a brewery’s OT network infrastructure and production facility.
-
A series of Blockchain bite-sized scenarios highlighting smart contracts security and exploitation, which can cause companies billions of dollars in financial losses.
-
Defensive scenarios simulating malicious agents deployed in enterprise cloud instances, which is a critical tech today’s organizations.
These releases add up to our advanced Cloud Labs offering, based on the most important and business relevant technologies (AWS, Azure, and GCP). After surveying 400 active cybersecurity professionals in the HTB database, we found that over 40% believe cloud security skills will be a key priority for SOC analysts over the next five years.
Continuous Threat Exposure Management (CTEM)
Our methodology and platform features are designed to carefully oversee skills development and analyze potential gaps that could cost real dollars to the business.
Learning and understanding CVEs in a safe environment is crucial for the cyber workforce to quantify risk, identify the mitigation steps, and finally translate technical findings into business outcomes.
-
Understand your operational infrastructure.
-
Understand what the adversary uses in terms of TTPs.
-
Attempt to understand the collection requirements of the adversary.
-
Decrease your mean-time-to-detect (MTTD), mean-time-to-resolve (MTTR), and mean-time-to-contain (MTTC).
This is how HTB Enterprise Platform enables organizations to foster a dynamic Purple team approach and foster collaborative security practices, implementing predictive concepts within defensive or threat hunting operations.
Choose HTB to boost your cyber performance
Today’s cyber threats present a new challenge to organizations, and unskilled teams pose a real risk to the security of your business. This is why cybersecurity performance programs and continuous improvement are no longer a nice-to-have, but a necessity.
Start now to implement your proactive security strategy!
-
Risk mitigation: Timely content offers training on the latest CVEs in real-world environments, reducing risk and exposure to these vulnerabilities.
-
Employee retention: Cybersecurity teams that are offered upskilling opportunities are far more engaged and less likely to burn out.
-
Performance benchmarking: Conduct CTFs and gap analysis to identify weaknesses in your security posture.
-
Tailored training to industry standards: HTB content is mapped to MITRE ATT&CK and NIST NICE frameworks so you can assess your cyber preparedness in different areas.
-
Boost organizational awareness: HTB can assess cyber readiness and performance company-wide with effective practices like tabletop exercises (TTXs) or nearly practical assessments designed for security staff and non-technical teams.