Cyber Teams
How to prevent healthcare data breaches: Why spotting threats isn’t enough
Learn how healthcare can prevent data breaches. Why spotting threats isn’t enough—defense, IoMT security, and AI-driven risks demand action.

diskordia,
Sep 10
2025
Picture the scene: a surgeon scrubs in, the patient is on the table. Everything is prepped and ready to go.
But just as the surgeon is about to make the first cut, the entire hospital network suddenly locks up. Nobody can access the patient records.
The clock is ticking, not just for your security team, but for patient lives.
This isn’t a hypothetical. Healthcare is one of the most frequently targeted sectors on the current threat landscape, and the consequences aren’t measured in dollars alone, but in lives disrupted or even endangered.
The 2025 Global Cyber Skills Benchmark Report gets into the meat of exactly why this problem lingers. Healthcare teams scored well below average across 40 hands-on cybersecurity challenges, with a sector-wide solve rate of just 27.5%.
Overall, the sector seems to be experiencing something of an imbalance; they’re great at spotting threats but much weaker at stopping them.
Test. Measure. Improve. Repeat.
Let’s take a closer look at what the challenges are for healthcare cybersecurity, and how to be better prepared.
Table of Contents
The detection/defense discrepancy
Healthcare defenders are excellent at reconnaissance according to our data. Teams scored 76.6% in OSINT, showing they can map attack surfaces and detect suspicious activity. However, when it comes to prevention—secure coding, web security, cloud defense—the numbers plummet to <20%.
Explore cybersecurity training for healthcare providers
In a nutshell: while hospitals know attackers are knocking, the doors and windows aren’t reinforced. Once intruders find their way in, weak defenses against persistence and privilege escalation let them hang around, move laterally, and silently siphon off that sensitive patient data.
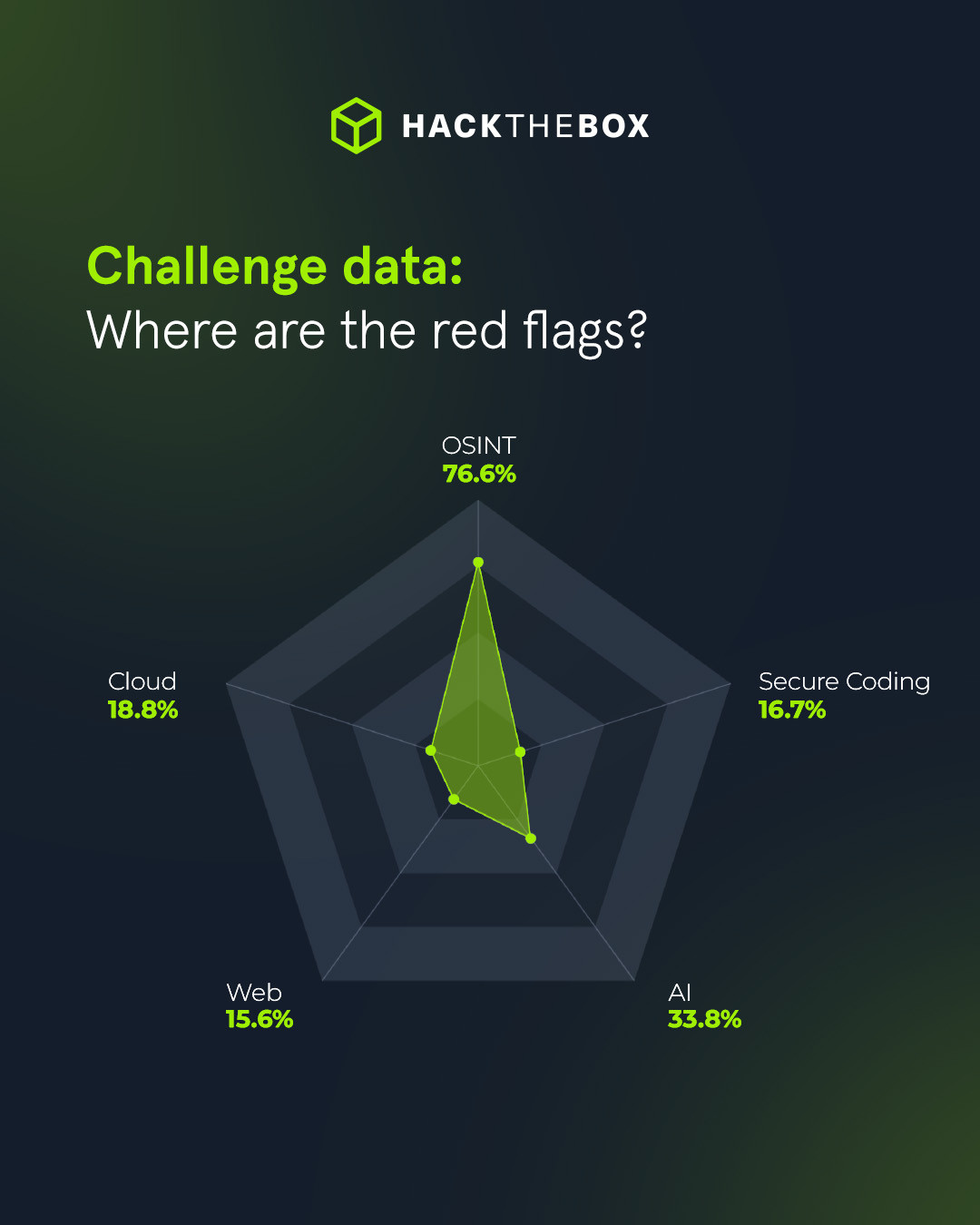
And that’s how ransomware blocks surgeries and how cloud leaks expose millions of records. And in an industry like this one, these aren’t just IT issues or GDPR concerns. There are lives at risk.
Healthcare cybersecurity: Key vulnerabilities
Part of the challenge is the sprawling complexity of healthcare IT. Many hospitals still run legacy systems never built to withstand modern attacks.
At the same time, the rush to digitize care has brought in patient portals, telemedicine, and massive cloud-hosted data sets, expanding the attack surface faster than security teams can keep up.
And then there’s the Internet of Medical Things (IoMT): every ventilator, infusion pump, and monitoring device is now connected. That connectivity saves lives, but it also opens up a buffet of new paths for attackers.
Throw in staff shortages, tightening budgets, and compliance-heavy workloads, and it’s no wonder attackers keep finding gaps.
There’s a straightforward starting point here: patching legacy systems consistently and enforcing MFA across staff accounts. It’s not fancy, it’s not glamorous, but it protects against a significant number of real-world threats.

The next wave of threats: AI and IoMT attacks
Two emerging trends are making the challenge for healthcare security teams steeper—and more urgent than ever:
AI-powered exploitation
Attackers are no longer leaning on generic phishing templates or manual reconnaissance to power their efforts. AI tools allow them to scan medical records, find patterns in protected health information (PHI), and generate highly targeted phishing emails that speak to specific clinicians, administrative staff, and even patients.
They can also craft malware that adapts its behavior to evade anomaly detection in connected devices, meaning attacks can fly under the radar for longer periods.
In short, AI is turning reconnaissance and exploitation from a slow, labor-intensive process into an automated, precision strike.
IoMT ransomware
The Internet of Medical Things (ventilators, infusion pumps, patient monitors) is becoming ever more popular as a target, likely because of its potential for disruption and as a strategic foothold.
-
Attackers exploit firmware vulnerabilities to gain persistence on these devices, then pivot into hospital networks, moving laterally to access critical systems.
-
For example: A compromised infusion pump isn’t just a broken device; it’s an open door to EHR databases, scheduling systems, and even medical imaging networks. Recent incidents show attackers using IoMT ransomware to force hospitals into paying quickly, knowing downtime directly threatens patient care.
Real-world incident: In June 2024, a ransomware attack on Synnovis, a pathology services provider to the NHS, caused nearly 1,600 operations and outpatient appointments to be canceled across London hospitals, including critical surgeries like cancer treatments and organ transplants. The encrypted systems left hospitals scrambling to redirect patients and restore care, showing just how quickly downtime in connected medical devices translates into real-world patient risk.
The implication for CISOs is this: AI and IoMT defense cannot continue to be niche initiatives or “special projects.” They need to be integrated into the core security strategy, with dedicated monitoring, proactive patching, and scenario-based drills that reflect these highly automated and device-centric threats.
Practical advice for breach prevention in healthcare
So, how do you move from spotting threats to stopping them?
Start by running simulations that mirror real-world attack chains—ransomware encrypting EHR databases, IoMT devices being hijacked, or phishing campaigns targeting staff. These exercises quickly show whether your defenses hold up when it matters.
From there, prioritize upskilling in the areas bad actors exploit most: secure coding for medical apps, cloud security for patient data, and defenses against lateral movement within networks. Here, don’t settle for generic training; target the skills your teams actually need to protect against costly breaches.
Finally, practice CTEM across your operations. Make it routine to measure exposures, remediate gaps, and validate improvements. Over time, this shifts the culture from firefighting after breaches to preventing them before they ever disrupt care.
The bottom line for cybersecurity in healthcare
Cybersecurity in healthcare goes way beyond avoiding fines or ticking regulatory boxes—it’s about protecting patients. Every data breach, ransomware delay, and minute of downtime could have a human cost. The security teams that succeed will be the ones that:
-
Invest in prevention, not just detection
-
Treat IoMT and AI security as mission-critical
-
Continuously test and adapt their defenses
One of the biggest traps is mistaking compliance for security. Passing an audit might satisfy regulators, but attackers don’t care about checkboxes.
Benchmarking skills shows you where you stand. CTEM keeps you ahead. Hack The Box Enterprise Platform enables continuous exposure management through hands-on attack simulations, labs mapped to MITRE ATT&CK, and real-world scenarios that test and harden defenses in practice.
Explore HTB Enterprise Attack Simulation Training
Think of it like patient care: benchmarking is the diagnosis, CTEM is the ongoing treatment. With Hack The Box, you get both the insight and the tools to act on it.
Download The Global Cyber Skills Benchmark Report 2025 for more insights















