Blue Teaming
Board-ready cyber resilience: How to track and prove readiness
Show measurable cyber readiness to boards and regulators. TRI gives CISOs clear insights into SOC and DFIR performance under real-world attacks.
Every CISO out there knows the awkward silence that follows the question: “But how can we know our team is actually ready?”
It’s a question that has echoed through boardrooms for years. We’ve got sprawling tech stacks, AI everywhere, automated detections, and hardened endpoints, but when the next incident comes knocking, readiness will always come down to people and their skills.
Can analysts recognize the first sign of intrusion? Will investigators trace lateral movement before exfiltration? Can leadership make containment calls fast enough to matter?
Most can’t answer those questions with data. They answer with confidence, culture, and guesswork. And that’s a problem, because guesswork is expensive.
According to IBM’s 2025 Cost of a Data Breach Report, the global average breach now tallies up to $4.88 million, and organizations taking more than 200 days to detect an attack pay $1.2 million more than those that contain it sooner. Dwell time is money, and dwell time is human. It’s the chasm between alert and recognition, escalation and action.
Table of Contents
Why you need more from your metrics
For a long time, security dashboards have revolved around familiar numbers: Mean Time to Detect, Mean Time to Respond, SLA adherence, false-positive rations. These metrics remain vital—and are captured directly inside Threat Range—but context is key.
A low MTTD looks awesome…until an alert stalls between analysts. A robust SLA record doesn’t necessarily mean smooth coodination when it’s crunch time. Because these numbers measure individual or process speed rather than how well your team is performing as a whole.
Threat Range bridges that gap by connecting traditional metrics to what actually matters in an incident:
-
Collaboration
-
Communication
-
Adaptability
By running exercises that test teams in their entirety—rather than just individual tools or playbooks—leaders have better visibility ow how those metrics look in the real world. That means getting a more complete picture of performance, reflecting both precision and people.
Remember: while all CISOs need to track mean times, the ones who win big know their team’s mean performance.
Inside Threat Range: Turning pressure into proof
This is where Threat Range comes in. It’s a live-fire environment that simulates advanced cyberattacks, from multi-stage intrusions to ransomware outbreaks, inside a sandboxed ecosystem. SOC and DFIR teams are dropped into the chaos and tasked with handling it exactly as they would in production: triaging alerts, escalating, investigating, containing, and reporting.
Every action, decision, delay, and handoff is captured and analyzed. The result is a clear, data-driven view of how your team actually operates when no one’s reading from a script.
And at the heart of it all is the Threat Resilience Index (TRI).
What is the Threat Resilience Index?
The TRI is a dynamic scoring framework that quantifies how prepared your team is across the full incident lifecycle. It combines the metrics you already know::
-
Mean Time to Acknowledge (MTTA): How fast alerts are recognized.
-
Mean Time to Detect (MTTD): How quickly threats are identified.
-
Mean Time to Investigate (MTTI): How long it takes to analyze and confirm malicious activity.
-
Mean Time to Respond (MTTR): How efficiently incidents are contained and remediated.
-
True/False Positive Accuracy: The quality of detection and triage decisions.
-
SLA Adherence: How well teams align to business-critical response timelines.
But it goes beyond that. These metrics are aggregated into a dynamic, live score (the TRI) representing your organization’s actual operational readiness. And crucially, this data is contextualized. It doesn’t just measure how long detection took; those times are correlated to fatigue, coordination, and decision quality.
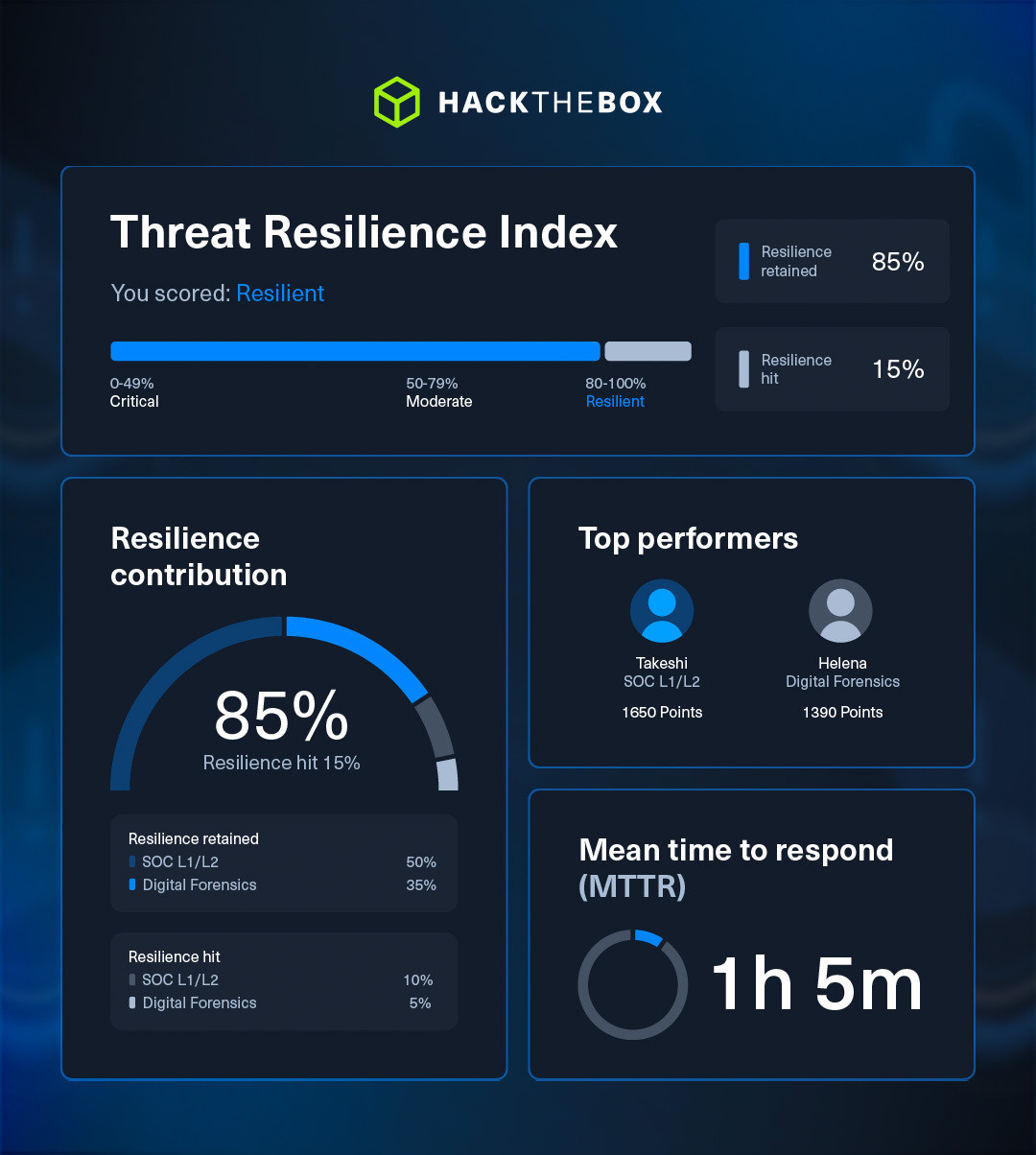
Think of it as a powerful fitness tracker for your SOC and DFIR teams, only it benefits your entire organization’s immune system and recovery. Just as athletes monitor their speed, endurance, and recovery to optimize performance, cyber teams can now track and improve their resilience with actionable, data-driven insights.
What you can learn from your own data
The value of this kind of insight is hard to overstate. For the first time, CISOs can correlate readiness metrics with real-world risks.
-
Skill gaps become quantifiable. If lateral movement consistently goes undetected, that’s a training gap, not bad luck.
-
Process bottlenecks become visible. If every escalation to DFIR adds 45 minutes, there’s a workflow problem.
-
Burnout becomes measurable. Rising false positives or longer investigation times signal analyst fatigue before it becomes turnover.
-
Investment decisions gain clarity. Instead of buying another platform “just in case,” you can see which capabilities deliver measurable improvement.
This level of transparency gives leaders something rare in cybersecurity: data-backed control.
The CISO formula: Cost, risk, proof
When the board asks for metrics, “just trust us” won’t cut it. Threat Range delivers quantifiable data that translates security readiness into financial and operational language that decision makers can understand quickly.
Improving mean detection and response times directly reduces potential breach costs. A more resilient team lowers downtime, regulatory exposure, and insurance risk. And because TRI results are mapped to frameworks like MITRE ATT&CK and NIST, they provide board- and regulator-ready evidence of due diligence. The business value stacks up:
-
Risk reduction through measurable improvement in detection and containment.
-
Cost savings via targeted upskilling instead of broad, inefficient training.
-
Stronger audit posture with quantifiable proof of readiness.
-
Improved retention as burnout decreases and team engagement rises.
For a CISO, that means more than operational progress alone. It’s strategic leverage and business resilience in action.
Real-world scenario: When weak spots come with a price tag
In early 2025, the ShinyHunters group (linked to Scattered Spider) executed a large-scale social-engineering campaign exploiting Salesforce integrations. By impersonating IT staff and distributing modified data-loader tools, they gained access to legitimate credentials and exfiltrated sensitive data across aviation, insurance, and retail sectors. No single organization was negligent, but the outcome was:
-
Data exposure across customer and business records.
-
Costly remediation and regulatory notifications.
-
Reputation management and trust rebuilding across global brands.
The attack reinforced a growing reality: today’s adversaries target processes and people, not just technology. This is where visibility really matters. Metrics tracked through the Threat Resilience Index (TRI), like:
-
Mean Time to Detect (MTTD): How quickly anomalies are spotted.
-
Mean Time to Investigate (MTTI): How long it takes to analyze and confirm threats.
-
True Positive Accuracy: How often analysts make the right call under pressure.
These insights reveal the hidden performance gaps that attackers exploit long before they become incidents.
The cost of missing them can be staggering. Following the MGM Resorts breach, the company disclosed around $100 million in disruption and recovery expenses, later agreeing to a $45 million settlement related to customer data exposure. Even a few hours of delayed detection or containment can result in weeks of downtime and tens of millions in losses.
Scattered Spider was also behind the recent cyber attack on UK retail chain Co-op, causing £206m in lost revenue alone.
With Threat Range, those weaknesses are made visible, measurable, and fixable, transforming team performance data into real financial and organizational resilience.
What’s next for cyber leaders?
The next wave of successful cyber leadership won’t be defined by how many tools a company deploys, but by how well it understands its own defenders.
AI-driven threats will continue to evolve, automating reconnaissance, evasion, and exploitation. The only sustainable countermeasure is an equally adaptive defense—one that learns from its people as efficiently as attackers learn from their data.
Threat Range makes that evolution measurable. It turns readiness from a periodic checkbox into a living, breathing metric that reflects the health, coordination, and confidence of your team.
Threat Range is available as an add-on for all Hack The Box business plans. Equip your defenders with the one environment where performance becomes visibility—and visibility becomes confidence.

















