Blue Teaming
18 SOC analyst interview questions (answered by an ex-analyst)
Former SOC analyst and HTB’s Defensive Content Lead, Sabastian Hague, shares important questions and answers for anybody looking to hire (or become) an analyst.

sebh24,
Jan 10
2023
Table of Contents
- What is SOC?
- What does a SOC analyst do?
- Interview questions and answers for a SOC analyst
- 1. How do you stay up to date with the latest security news?
- 2. Are there any high-profile security incidents that have interested you lately and why?
- 3. Do you have any experience in scripting or programming? If yes - what languages?
- 4. Can you describe the difference between UDP & TCP?
- 5. Will you talk us through the TCP handshake?
- 6. How much command line (CLI) experience do you have (on any OS)?
- 7. You open a browser and browse to hackthebox.com. What steps does your host take to resolve the address?
- 8. Can you describe a standard cyber security incident response process?
- 9. How would you approach a problem you’ve never seen before?
- 10. Once you’ve solved the problem not previously seen, is there anything you could do?
- 11. You are presented with a potentially malicious Windows binary, what are some steps you could take for basic analysis?
- 12. Have you utilized any SIEM tooling? If so, which one?
- 13. Have you used any EDR/XDR tools in the past? If yes - which ones? If not, don’t worry - can you explain what they exist for?
- 14. Can you explain the difference between true positive, false positive, and false negative?
- 15. Imagine you’ve joined our organization and a member of the IT admin team has recently set up a public-facing web server. What advice would you give to help secure it?
- 16. What event logs are available by default on Windows?
- 17. Imagine we have two remote assets that aren’t connected to any security tooling and we had to manually retrieve artifacts from them. One asset is Windows, the other is a Ubuntu host. Can you talk us through the forensic artifacts you would look at collecting from both assets? (bonus points for explaining why you’d collect them)
- 18. You are performing routine daily analysis and whilst checking failed logon activity you find the following (there are 2000 similar events within a small time frame):
Are you a manager looking for the best SOC analyst interview questions to ask candidates? Maybe you're a SOC analyst who's preparing for your next interview, but like me, you don't have an encyclopedic memory of all the technical questions you could be asked. Or perhaps you are curious about what kinds of skills go into being a SOC analyst?
Whatever camp you fall into, this blog post will help! Based on my experience as a SOC specialist, I'll list the top SOC analyst interview questions to ask and share answers that benefit both hiring managers recruiting SOC candidates, and anyone preparing for their next cybersecurity job interview.
What is SOC?
A SOC, or Security Operations Center, is a centralized location where an organization's security professionals monitor and analyze the organization's computer systems and networks to identify and mitigate potential security threats.
A SOC typically includes a team of security analysts and other security professionals who are responsible for monitoring network activity, responding to security alerts and incidents, conducting investigations into potential security breaches, and implementing security controls and protocols to protect against potential threats.
What does a SOC analyst do?
A SOC analyst is one of many security professionals that play a part in keeping an organization’s systems and networks safe from potential threats. The analyst's role is focused on actively monitoring network activity, responding to security alerts, and conducting investigations into potential security breaches. This is an important role as an analyst can often be the first point of contact in an incident or the first to spot a security event as it happens.
When I was a SOC analyst, an additional part of my role was leading planning for the configuration of logging on any monitored networks. A SOC analyst's input on the configuration of logging is extremely valuable as it may highlight gaps in granularity, which can be rectified with collaboration between both the SOC and System Administration team.
Related read: How to become a cybersecurity analyst
An interviewing tip for SOC managers:
The interview questions that you choose shouldn’t be strictly technical. In fact, a lot of the initial questions are (or at least should be) more about your candidate as a person.
This is important because you’re speaking to a potential colleague and this is your chance to break the ice, get familiar, and develop rapport. Personally, I’ve found myself to be more relaxed and ready for incoming technical questions after a casual, laidback start to the interview.
Hire and get hired for cybersecurity roles
With HTB Talent Search, professionals (who've proved their practical cybersecurity skills on the HTB app) can apply directly to roles posted by companies worldwide. This means that recruiters can access a growing pool of talented individuals looking for their next cybersecurity role.
Interview questions and answers for a SOC analyst
What to do if you don’t know the answer to a question:
First of all, be honest. If you don’t know the answer just say that you don’t know it (we can’t know everything can we?). Then, move on to explain how you’d find the answer.
Our industry is so vast that expecting someone to remember everything is simply unrealistic. Explaining how you’d find answers, however, shows (what I would strongly consider) a key skill for any infosec professional: The ability to quickly find answers to unfamiliar questions or problems.
Need help preparing for cybersecurity interviews?
-
Master complex concepts with free guided IT and cybersecurity courses on the HTB Academy.
-
Prove that you have job-ready cybersecurity skills by taking the CPTS penetration testing certification (you’ll have example reports and pentests to share in interview assignments).
-
Show your investment in your skills development and earn CPE credits by solving Machines, Challenges, Endgames, and real-world cybersecurity labs
Interested in landing a job as a pentester? Brush up on these 30 critical cybersecurity interview questions!
1. How do you stay up to date with the latest security news?
This is a great question! Where do we even start? I personally use a wide variety of sources such as:
-
Twitter: It's always been a great source due to the number of infosec professionals who exist on the platform. The list of excellent sources is endless, and top of my list is our very own ippsec.
-
KrebsOnSecurity: A blog that focuses on cybercrime and IT security written by Brian Krebs. The blog is known for in-depth investigative reporting on information security issues across the globe.
-
Darknet Diaries: Maybe not so good for the latest security news, but I find the podcast very interesting for some older large-scale compromises.
-
SANS ISC Podcasts: The podcast covers the latest news within information security. Episodes often feature interviewers with industry-leading experts providing valuable analysis of the latest threats and trends.
-
LinkedIn: Many infosec professionals use LinkedIn as a platform to share their knowledge, expertise, and insights on a variety of cybersecurity topics, such as current trends, best practices, and new technology.
-
Reddit: Reddit has a huge cybersecurity community, and there are a variety of subreddits I regularly browse through. I have detailed some of them below:
2. Are there any high-profile security incidents that have interested you lately and why?
Tip: The world is your oyster on this question, it's something I’ve been asked on numerous occasions in interviews.
The goal here is to show an awareness of what is going on within the industry. Because information security is changing so fast, keeping up with the latest news is an important part of being a defender. If I were to be interviewed today, a great example to speak about would be the recent LastPass breach. With a phishing email and insecurely stored cloud storage access keys believed to be the root cause, this breach highlights once again the need for even large-scale organizations to get the basics right.
3. Do you have any experience in scripting or programming? If yes - what languages?
While many entry-level jobs don’t require programming skills, more and more security roles are looking for at least a basic understanding of a scripting or programming language. Reasons for this can vary depending on the role, but in a standard SOC analyst role, a demonstrable understanding of PowerShell and Python could be incredibly beneficial during an interview. Working or striving to work in infosec you’ll have likely utilized a scripting language at some point - whether that is for the workplace or a home project - now is the time to bring that up.
Tip: This doesn’t have to mean that you’ve developed a brand new idea from scratch - taking someone else's idea and repurposing it can also count. SOC managers are not looking for polished developers, but rather the ability to use these tools to get the job done more effectively and efficiently. To summarize, showing a basic aptitude for or understanding of any scripting language will be to your benefit.
4. Can you describe the difference between UDP and TCP?
User Data Protocol (UDP) is what I like to call a “fire and forget” based protocol, meaning its connectionless and the retransmission of lost packets is not possible. Transmission Control Protocol (TCP) is a connection-based reliable protocol, which retransmits lost packets.
5. Will you talk us through the TCP handshake?
-
Syn: This is the first step of a TCP handshake when a client wants to establish a connection with a server. The client picks a sequence number, which is sent in the first SYN packet.
-
Syn-Ack: The server responds to the client request with both the SYN + ACK flags set. In this packet the server acknowledges the client's sequence number by incrementing it, this is called the acknowledgment number.
-
Ack: This is the final step of the three-way handshake in which the client acknowledges the response of the server and a connection is established.
6. How much command line (CLI) experience do you have (on any OS)?
Are you a command line ninja on both UNIX & Windows-based hosts? Have you got any examples of when you utilized these skills in a security incident?
CLI skill sets can sometimes be seen as a dying art; however, they’re invaluable when you need to quickly parse through data or navigate via a shell on a machine. It's also nice to highlight here that your understanding of the CLI assists in the thought process behind an attacker utilizing the CLI on a compromised endpoint.
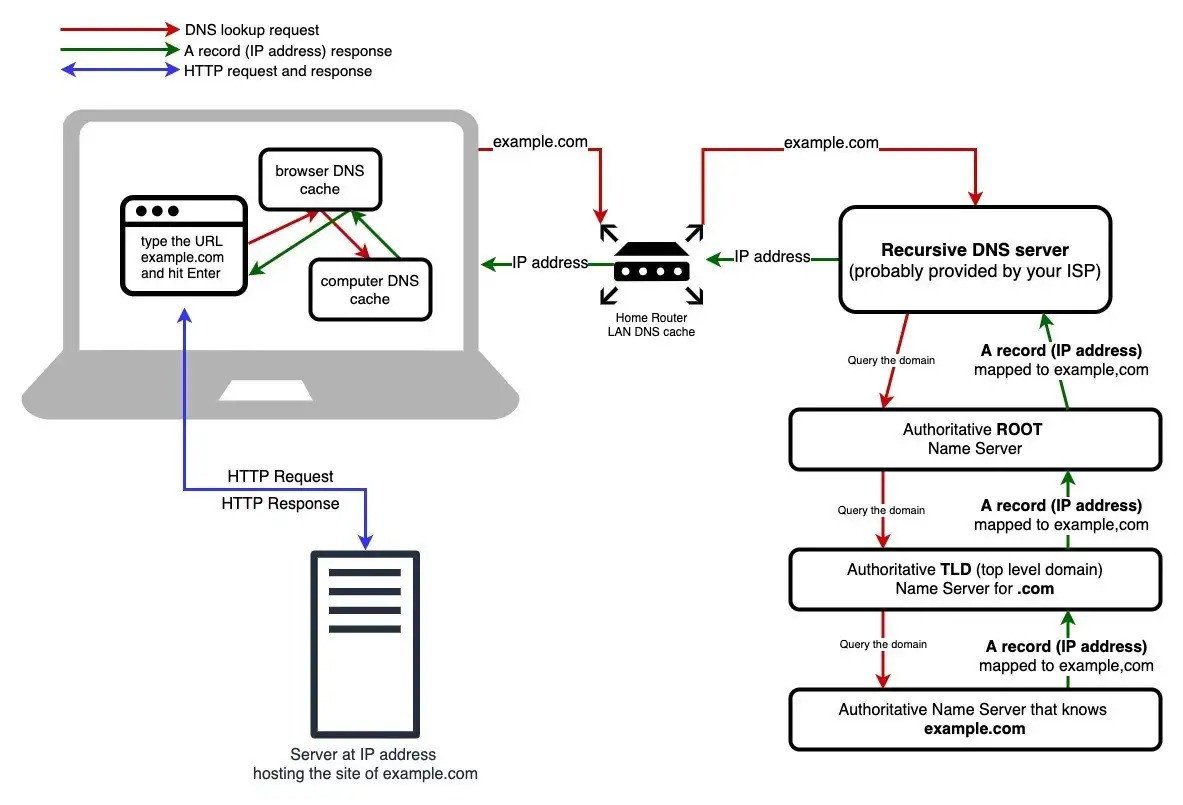
7. You open a browser and browse to hackthebox.com. What steps does your host take to resolve the address?
A picture paints a thousand words here, and there's an excellent Medium article that has gone into a lot of detail. (For the purposes of whichever URL the interviewer asks about, replace example.com with that URL.)
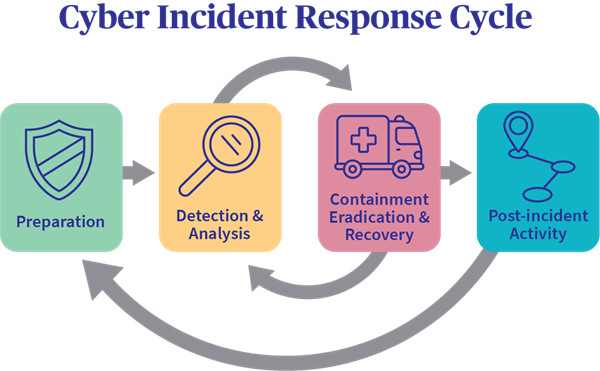
8. Can you describe a standard cyber security incident response process?
To answer this question, I usually speak about both the industry standard NIST cyber security incident response process and expand as to what actions are usually completed at each phase. But even if you don’t have the formal steps in mind, being able to talk through the process of understanding what’s happening, and taking action is valuable.
9. How would you approach a problem you’ve never seen before?
My first answer here is either Google it or ask a colleague. The chances are if there's a problem you haven’t seen before - someone else likely will have. Part of the package I try to “sell” in an interview is my ability to find and quickly learn new information - utilizing the internet at our fingertips is a big part of that (and is something hiring managers should actively seek).
Recommended read: how to gamify tabletop exercises for your team.
10. Once you’ve solved the problem not previously seen, is there anything you could do?
When anyone asks this question during an interview, they want to see candidates take some initiative by either documenting the answer or showcasing a new way of working to colleagues based on that solution. A great answer might be:
Using confluence, I’d produce a standard operating procedure document for the problem they came up with to ensure colleagues understand how to overcome this problem if it reappears. I’d also evaluate if there were any new alerts we could put in place to detect this kind of activity in the future (if appropriate), or any alerts that need to be tuned to reduce false positives.
11. You are presented with a potentially malicious Windows binary, what are some steps you could take for basic analysis?
Before we delve into an answer to this question, I’d like to highlight that in-depth malware analysis shouldn't be (or isn’t usually) expected as part of a SOC analyst job. However, looking into the future, with analysts utilizing tooling that interacts with endpoints becoming more common, an expectation of some basics is something that could become the norm.
A good place to start is searching VirusTotal (VT) for the malware’s hash, which allows you to see if someone else has uploaded the same binary without tipping to the threat actors that you are investigating this binary. If it isn’t already there, you could upload it, allowing VirusTotal to scan the binary against a database of known malware signatures and see if it matches any known threats. This can help you determine whether the binary is malicious or not.
As a SOC analyst, this is probably as far as you will be expected to go. However, if you’d like to delve deeper into this…
Another potential approach to analyzing a potentially malicious Windows binary would be to first run the binary in a controlled environment, such as a sandboxed virtual machine, to see if it exhibits any malicious behavior. This can help to prevent the binary from doing any damage to your host system. A great open-source tool for this is Cuckoo.
Next, you could use a tool like Process Explorer or Process Monitor to monitor the binary's activity and see which files it accesses, what network connections it makes, and what system resources it uses. This can give you an idea of what the binary is trying to do. You could also use a tool like strings or a hex editor to look at the binary's code and see if it contains any suspicious strings or anomalies that might indicate malicious behavior.
12. Have you utilized any SIEM tooling? If so, which one?
The answer to this question is heavily dependent on your experience. You've likely had some exposure to some kind of SIEM tool as you’re reading this post. So detail any exposure you have had. Whether that's in a home lab or production environment.
13. Have you used any EDR/XDR tools in the past? If yes - which ones? If not, don’t worry - can you explain what they exist for?
An endpoint detection and response (EDR) tool is a tool used to provide continuous visibility as to what is happening on endpoints in real time and assist in the forensic investigation and response on an endpoint if it is suspected of being compromised.
Having worked with a variety of EDR tools, I could go into depth with Cortex XDR, CyberReason, Tanium amongst many others. What I really like to highlight here though is that at the core of all these tools is the analyst who needs to understand what they are looking for. Understanding the UI of an EDR tool is fairly easy to do if you bring in the right staff who understand the operating systems the agents are deployed on.
Recommended read: Memory forensics with Volatility on Linux and Windows
14. Can you explain the difference between true positive, false positive, and false negative?
A true positive is a correct identification of a positive event, meaning that the event is actually happening and is being correctly identified as such by the system or process in question. For example, if a security system correctly identifies an attempted intrusion as a threat, that would be a true positive.
On the other hand, a false positive is when a system or process identifies a positive event that is not actually happening. In the case of our security system example, a false positive would be when the system incorrectly identifies a benign event, such as a legitimate user logging in, as a threat.
A false negative is when the system doesn’t identify an issue when there is one!
15. Imagine you’ve joined our organization and a member of the IT admin team has recently set up a public-facing web server. What advice would you give to help secure it?
-
Ensure that the server is running the latest version of the operating system and that all security patches and updates are installed. This can help to protect against known vulnerabilities and exploits.
-
Configure the server's firewall to only allow incoming traffic on the specific ports and protocols that are necessary for the server's operations. This can help to prevent unauthorized access to the server and to limit the attack surface.
-
Implement strong password policies to ensure that all user accounts on the server are protected with strong, unique passwords. This can help prevent unauthorized access to the server and protect against password-related attacks.
-
Implement access controls to restrict access to the server and its resources to only authorized users. This can help prevent unauthorized access to the server and protect sensitive data and resources.
-
Enable logging and monitoring to track access to the server and to alert administrators of any potential security threats or anomalies. This can help to identify potential security issues and to take appropriate action to prevent or mitigate them.
-
Regularly perform security assessments and penetration testing to identify potential vulnerabilities and to ensure that the server is properly configured and secured. This can help to identify and address any potential security weaknesses before they are exploited.
-
Place a Web Application Firewall (WAF) in front of the application. A WAF is a security tool that is designed to protect web applications from a range of potential threats, including malware, SQL injection attacks, and other types of malicious activity. WAFs typically work by inspecting incoming traffic to a web application and blocking or mitigating any requests that are deemed to be malicious or potentially harmful.
16. What event logs are available by default on Windows?
-
System log: This log contains information about the operating system, such as system start and stop events, driver events, and other system-level activities.
-
Application log: This log contains information about events related to applications installed on the system, such as when an application crashes or encounters an error.
-
Security log: This log contains information about security-related events, such as successful and failed login attempts, privilege changes, and other security-related activities.
-
Setup log: This log contains information about the installation and configuration of the operating system and its components.
-
Forwarded events log: This log contains information about events that have been forwarded from other computers on the network.
17. Imagine we have two remote assets that aren’t connected to any security tooling and we had to manually retrieve artifacts from them. One asset is Windows, the other is a Ubuntu host. Can you talk us through the forensic artifacts you would look at collecting from both assets? (bonus points for explaining why you’d collect them)
Windows host:
-
System logs: These logs contain information about the operating system, such as system start and stop events, driver events, and other system-level activities.
-
Security logs: These logs contain information about security-related events, such as successful and failed login attempts, privilege changes, and other security-related activities.
-
Application logs: These logs contain information about events related to applications installed on the system, such as when an application crashes or encounters an error.
-
Registry hives: The registry is a database that stores configuration information for the operating system and installed applications. Examining the registry hives can provide information about system settings, installed software, and other data.
-
Prefetch files: These files contain information about the applications and files that have been recently used on the system, which can provide insight into the host's recent activities.
-
MFT: The MFT is a system-level file in the NTFS file system that is used to store information about all the files on a disk. The MFT contains entries for each file on the disk, including the file's name, size, timestamp, and other metadata. Examining the MFT can provide valuable information about the files on a system, including deleted files and other data that may be relevant to a forensic investigation.
-
AmCache: The AmCache is a cache of information about installed applications on a Windows system. It contains entries for each installed application, including the application's name, version, publisher, and other metadata. Examining the AmCache can provide information about what applications are installed on the system, which can be useful for forensic investigations.
-
Memory dump: A memory dump is a snapshot of the contents of a computer's memory at a specific point in time. Memory dumps can be useful for forensic investigations because they can provide information about what was happening on the system at the time the dump was taken. This can include information about running processes, open files, network connections, and other data that may be relevant to the investigation.
-
Browser History: This can be extremely useful for forensic investigations because it provides information about the websites that a user has visited. This can provide valuable context for the investigation, allowing investigators to understand what the user was doing at the time of an incident and potentially identify any suspicious or malicious activity. For example, if a user's computer is compromised, examining their browser history can help analysts to identify any suspicious websites that the user may have visited, which could potentially have been the source of the initial compromise.
Ubuntu Host:
-
System logs: Linux systems, such as Ubuntu, maintain system logs that can provide valuable information about the host's activities. These logs can include information about system start and stop events, kernel events, and other system-level activities.
-
Application Logs: Linux systems like Ubuntu are often utilized to host applications, for example, Tomcat or Apache. Often these logs are in a differing location to /var/log and therefore additional concern should be held as to how these can be collected.
-
Bash history: This file contains a record of the commands that have been run on the system, which can provide insight into the host's activities and potential security threats.
-
Package manager logs: Ubuntu uses a package manager, such as apt, to manage installed software. Examining the package manager logs can provide information about what software has been installed on the system and when.
-
System-level configuration files: Linux systems have various configuration files that control system-level settings, such as network and security settings. Examining these files can provide information about the host's configuration and potential security vulnerabilities.
-
Memory dump: A memory dump is a snapshot of the contents of the server's memory at a specific point in time. Examining a memory dump can provide information about what was happening on the system at the time the dump was taken, including information about running processes, open files, and network connections.
-
The contents of the /tmp/ directory: The reason we collect the contents of the /tmp/ directory is that attackers often use this directory as a location to drop files.
18. You are performing routine daily analysis and whilst checking failed logon activity you find the following (there are 2000 similar events within a small time frame):
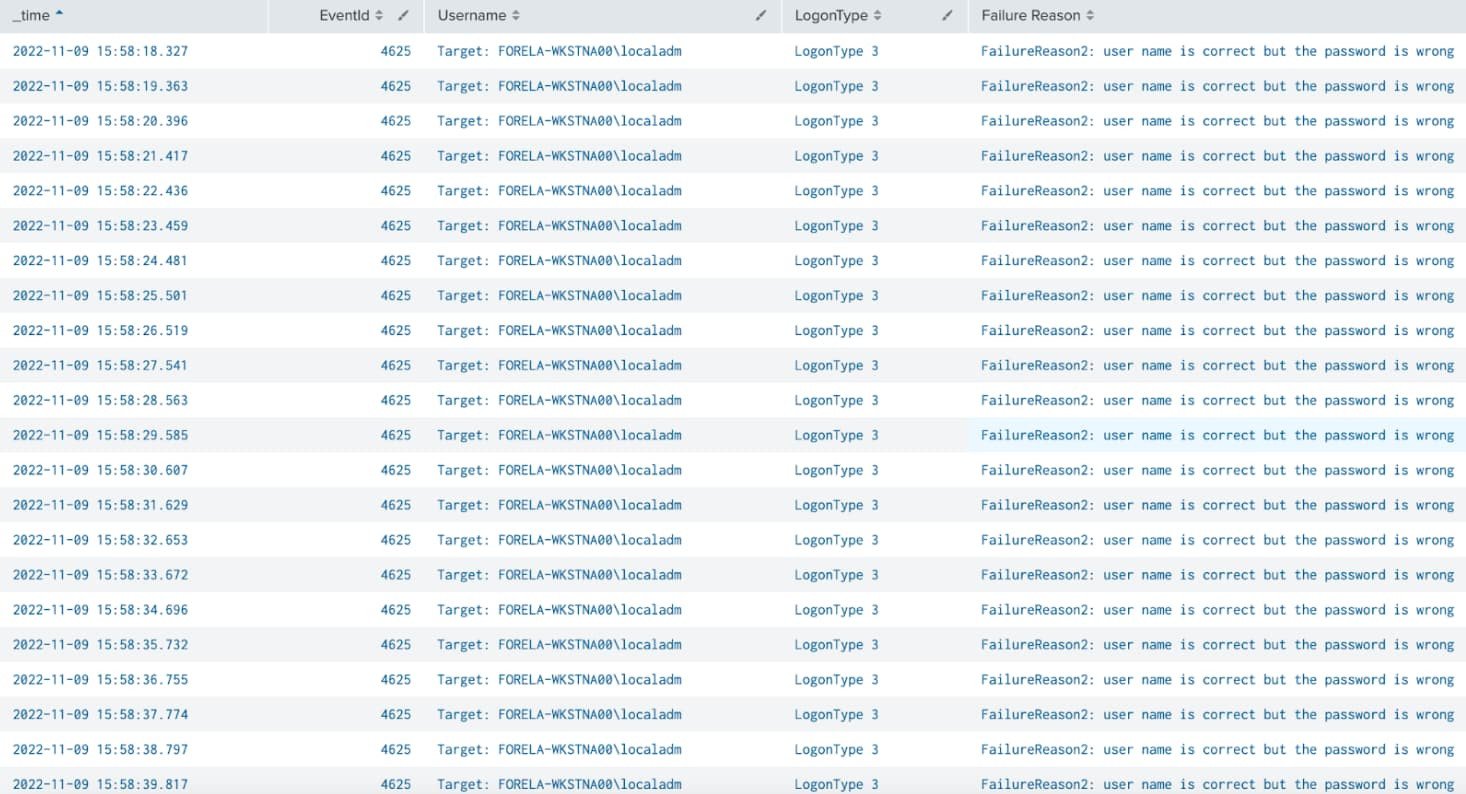
Please talk us through what you think may be happening and what your next steps are.
A. So immediately I recognized the event id 4625 as a failed logon, with a logon type of 3. This is the network logon type and can occur for a variety of reasons - one being a connection to a shared folder from elsewhere on the network; another reason could be the unsuccessful authentication with psexec, something commonly used by adversaries.
B. I then would point out that the one second of time between each failed logon and the fact that there are in excess of 2000 of these within a short time period show that this is not human-based activity and therefore is likely automated. This indicates attempted brute forcing of the user account detailed “localadm” on the FORELA-WKSTN00 host.
C. The username being “localadm” looks like a shortened name for “Local Admin”. I would like to confirm if this account is the local admin account used in the environment.
D. Now I’ve confirmed the username and the host attempting to be abused I would ensure that the host is placed into containment.
E. I would expand on the current search by performing a search for the event id “4624” or “Successful logon” within the time period of the brute forcing attempts. If a successful attempt is found this confirms that an attacker has likely gained access to FORELA-WKSTNA00 with local elevated privileges, I would:
-
Recommend confirming if any sensitive information exists on this host and notify the organization’s DPO if it does.
-
Also begin a search for any events that have occurred on FORELA-WKSTNA00. As a priority, I would look for evidence of password dumping as the attacker would likely now attempt to elevate to domain administrative access.
F. If EDR is present in the environment, I would utilize it to perform a sweep of the FORELA-WKSTNA00 host.
G. I would also expand the search to include the originating host attempting to make the connections.
H. Once we’ve confirmed the originating host, if it is an internal host I would immediately recommend containment. If it's an external host, I would recommend dropping all traffic to and from that host at the firewall.
I. Additionally, I would then expand our search in the SIEM platform to look at all events within the time period relevant to the originating host.
J. If the local admin account has been utilized for lateral movement, this indicates that the same password is likely used across the environment. Going forward I would recommend utilizing LAPS.
K. Additionally I would recommend the full rebuild of the FORELA-WKSTNA00 host.
|
Author Bio: Sabastian Hague (sebh24), Defensive Content Lead, Hack The Box Sabastian Hague is a seasoned cybersecurity professional with over eight years of experience in the field. After serving in the Royal Air Force as a specialist in all things SOC, he went on to work for Vodafone's global CERT team before taking on a role as a senior security consultant with SpiderLabs and working on numerous high-profile incidents. He is now the Defensive Content Lead at Hack The Box. Seb has numerous industry certifications including GIAC Certified Detection Analyst (GCDA), GIAC Continuous Monitoring Certification (GMON), GIAC Certified Incident Handler (GCIH), GIAC Certified Intrusion Analyst, Offensive Security Certified Professional (OSCP), Blue Team Level 1 (BTL1), Blue Team Level 2 (BTL2), Cybereason Threat Hunter (CCTH). |














