Threat Intelligence
Inside FireAnt: How UNC3886 used 15+ exploits to breach VMware ESXi and avoid detection
Discover how Chinese APT UNC3886 used 20+ MITRE techniques in the FireAnt campaign to exploit VMware ESXi hypervisors and evade detection.

Howard Poston,
Sep 10
2025
Table of Contents
In July 2025 Sygnia unveiled Fire Ant, a cyber attack campaign that the company had been tracking since early 2025. Based on various factors, including the malware used and the systems targeted, UNC3886 is believed to be behind the campaign. This APT group is affiliated with China and has been active since at least 2021 with a focus on cyber espionage.
Strengthen your security posture with HTB
Fire Ant was a sophisticated attack campaign exploiting virtualization to evade common endpoint security tooling. In this latest installment in our Attack Anatomy series, we’ll explore how it was carried out through the lens of the MITRE ATT&CK framework and identify HTB resources that can provide hands-on experience with the techniques used.
How Fire Ant compromised virtualization infrastructure
The Fire Ant campaign exploited vulnerabilities in the virtualization layer of VMware ESXi deployments and expanded their footprint from there. UNC3886 also deployed several malware variants and used multiple techniques to ensure persistent access to the compromised environment.
Initial access and lateral movement
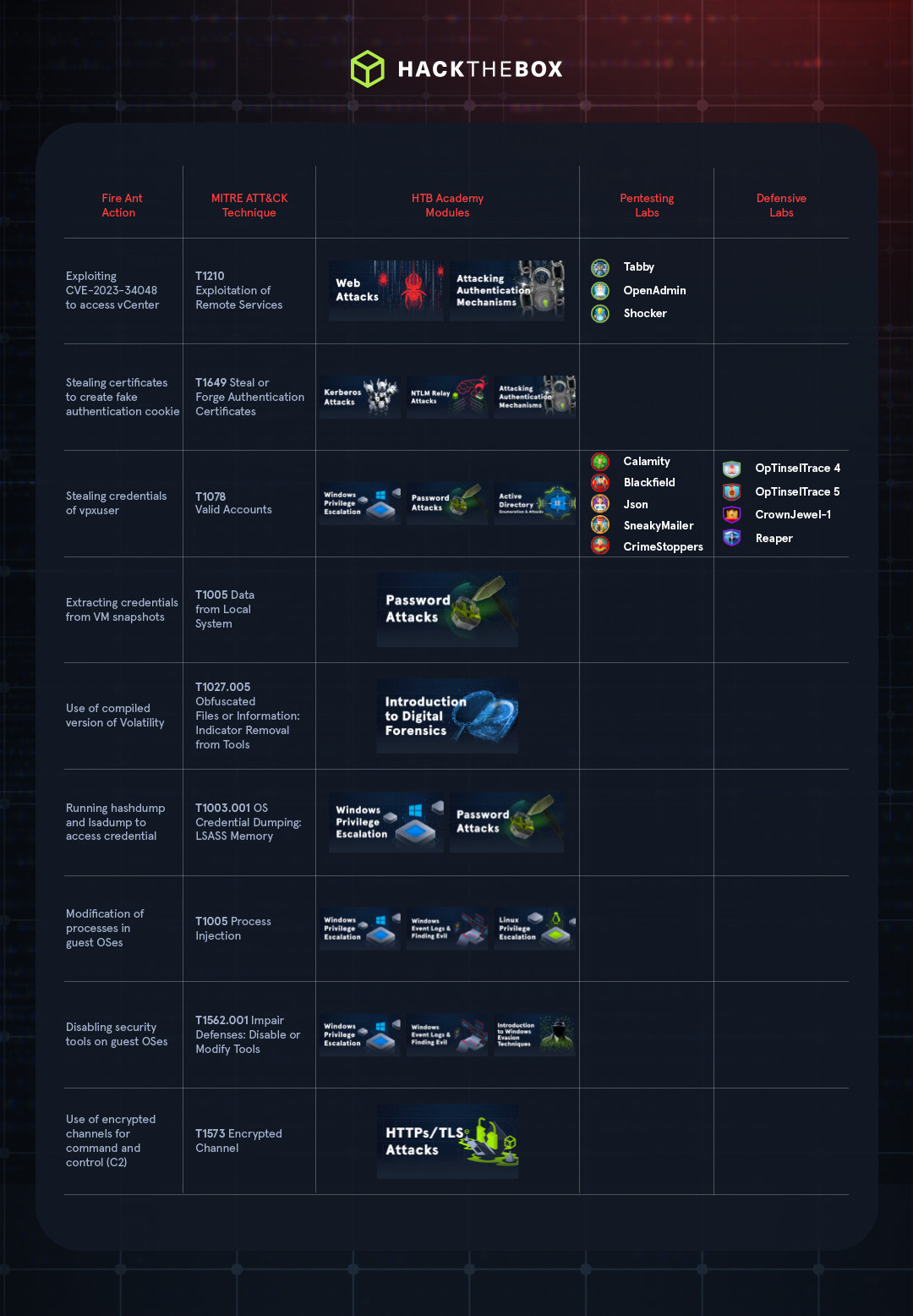
After achieving a foothold on the network, the attacker gained initial access to hosts running VMware ESXi and vCenter by exploiting CVE-2023-34048 (MITRE ATT&CK Exploitation of Remote Services).
This vulnerability permits unauthenticated remote code execution (RCE) within vCenter, allowing an attacker to run malicious code on the server and take control over the management of virtual machines. It has been active as a zero-day exploit since late 2021, with a patch issued in October 2023.
With access to vCenter, the attacker performed various malicious actions, including:
-
Generating forged authentication cookies using extracted certificates (MITRE ATT&CK Steal or Forge Authentication Certificates) for authenticated admin-level access to the vCenter user interface.
-
Extracting the credentials of vxpuser (MITRE ATT&CK Valid Accounts) to gain host-level access (MITRE ATT&CK Escape to Host) and control over all connected hosts running ESXi.
The APT group also accessed virtual memory (.vmem) files from suspended or snapshotted VMs (MITRE ATT&CK Data from Local System), parsing them for credentials cached in memory.
A compiled version of the Volatility Framework—named UpdateApp—was used (MITRE ATT&CK Obfuscated Files or Information: Indicator Removal from Tools) to run hashdump and lsadump (MITRE ATT&CK OS Credential Dumping: LSASS Memory) to extract user and domain controller credentials, which could be used for lateral movement.
By creating and deleting snapshots, the attacker concealed their credential collection and minimized potential artifacts on virtualized systems.
Guest VM control
The next step in the Fire Ant campaign was to access the various virtual machines hosted within vCenter.
This was accomplished by exploiting CVE-2023-20867 and using vmtoolsd (MITRE ATT&CK ESXi Administration Command) to modify processes in guest machines (MITRE ATT&CK Process Injection). This vulnerability allowed the attacker to run commands in PowerCLI without knowledge of the credentials of the guest users.
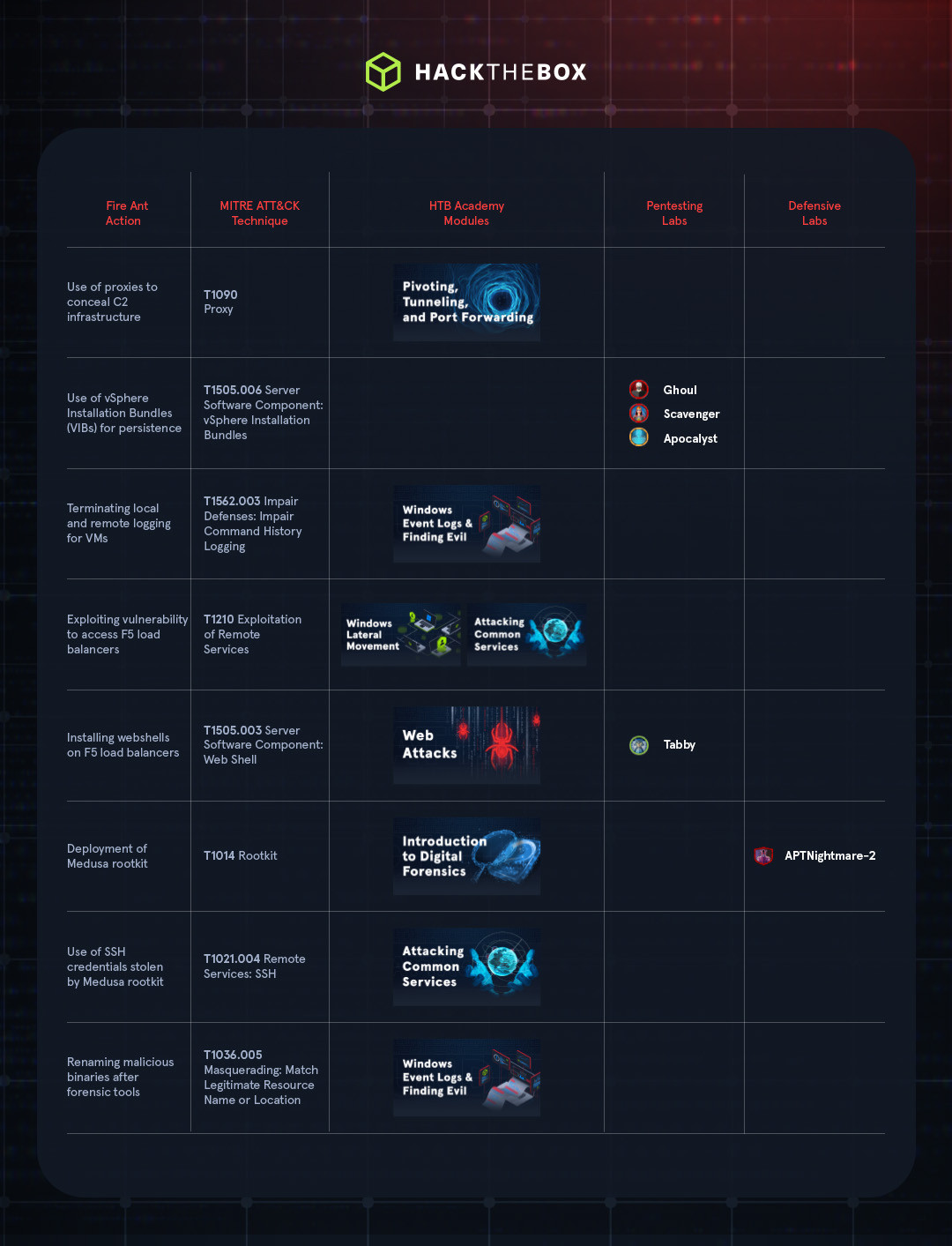
These commands were used for various purposes, such as disabling security solutions on compromised systems (MITRE ATT&CK Impair Defenses: Disable or Modify Tools) and running the V2Ray framework. This is a tool that creates encrypted tunnels for command and control (C2) communications (MITRE ATT&CK Encrypted Channel) and was configured to run on port 58899 and use proxies (MITRE ATT&CK Proxy).
Persistence and defense evasion
After achieving host-level access, the attacker implemented numerous persistence mechanisms to solidify their foothold. These included:
-
Deploying a backdoor at /usr/libexec/setconf/ksmd listening on port 7475.
-
Deploying vSphere Installation Bundles (VIBs) for persistent, backdoor access from the VIRTUALPITA malware family (MITRE ATT&CK Server Software Component: vSphere Installation Bundles).
-
Installing VIRTUALPIE, a Python, HTTP-based backdoor permitting RCE and file download/upload via a web server running on port 8888.
-
Terminating the vmsyslogd process to kill both local and remote logging to hamper forensic analysis (MITRE ATT&CK Impair Defenses: Impair Command History Logging).
-
Deploying unauthorized virtual machines directly so that they weren’t registered with vCenter, concealing them from its inventory tools (MITRE ATT&CK Hide Artifacts: Run Virtual Instance).
Fire Ant was a sophisticated and sustained campaign with the attackers using numerous methods to evade detection. Additional elements of the persistence strategy included:
-
Compromising F5 load balancers via CVE-2022-1388 (MITRE ATT&CK Exploitation of Remote Services) to deploy webshells (MITRE ATT&CK Server Software Component: Web Shell)
-
Installing open-source Neo-reGeorg tunneling webshells on java-based webservers
-
Running the Medusa rootkit (MITRE ATT&CK Rootkit) on Linux systems to collect SSH credentials (MITRE ATT&CK Remote Services: SSH) and provide backdoor access.
-
Implement port forwarding on compromised systems (MITRE ATT&CK Proxy: Internal Proxy) to route traffic to evade access control lists (ACLs).
-
Monitoring incident response efforts to reinfect systems, change tools and techniques, and rename malicious binaries, often after the forensic tools in use (MITRE ATT&CK Masquerading: Match Legitimate Resource Name or Location).
Protecting against the Fire Ant campaign with HTB
Fire Ant was a sophisticated cyberattack campaign performed by an established APT group. By targeting the virtualization layer, the attackers evaded many endpoint security solutions, which are typically deployed within the guest OS and lack downward visibility.
On top of that, the use of various exploits and persistence mechanisms provided deep, lasting access to compromised environments.
UNC3886, the group allegedly behind the campaign, was named as a serious national security threat by Singapore’s security minister due to its targeting of critical national infrastructure. The impact of this attack campaign has not just limited to the APAC region—it’s worldwide.
The Fire Ant campaign underscores the importance of going beyond traditional endpoint security to address advanced cyber threats. Key elements of a strategy to address this and similar campaigns include:
-
Identifying threats at the network level and in system memory.
-
Promptly applying patches for high-risk vulnerabilities, such as the VMware, Fortinet, and Juniper ones used in this campaign.
-
Monitoring for custom backdoors deployed for persistent access.
The sheer variety of tools and techniques used in this campaign is impressive, and Hack The Box has resources to provide hands-on experience with each of them.
By simulating the various elements of this campaign, teams can learn how they work and build the skills needed to design layered defenses and proactively search for indicators of compromise (IoCs) within their environment.
Want to go hands-on with the techniques used in the Fire Ant campaign? Explore HTB Enterprise Platform to simulate real-world adversary tactics like UNC3886’s, strengthen your defenses, and train your team to detect and respond to advanced threats.















