Blue Teaming
Beat SOC analyst burnout with better L&D
SOC analyst burnout is rife thanks to the “always-on” nature of the role paired with a lack of training. Tackle this major issue with effective L&D.
Table of Contents
Effective workforce development programs are a powerful ally for battling burnout.
In our Cyber attack readiness report, we found that 62% of managers rated “opportunities to learn new skills” as the best way to prevent burnout among security staff.
This insight empowers managers to invest in L&D to keep their analysts engaged, rather than spiralling into endless alert fatigue.
Burnout is a problem that extends beyond your team, damaging your security posture—83% of security professionals admit that burnout-induced errors within their department have directly resulted in a security breach.
But solving burnout isn’t as simple as increasing paid time off or upping salary. Our research, which surveyed security team leaders and security staff, shows career and skills development opportunities play a major role in mitigating burnout.
Let’s dive into our findings! (Featuring unique research from two reports from the last year: Cyber attack readiness report and Developing the modern SOC analyst).

1. Blue teamers want to explore red teaming

In our report on developing the modern SOC analyst, we found that hybrid blue and red teamers are on the rise, with many cybersecurity professionals wishing to pursue a career in both roles:
-
3 in 10 (30.8%) expressed an interest in pursuing a blue team career before moving into an offensively-oriented role.
-
27.8% of professionals planned their careers the opposite way around, showing an interest in offensive security roles before switching to a career path in defensive security.
-
Only 10.5% of professionals wish to pursue a career purely in defensive security.
By offering opportunities to upskill in offensive security, SOC analysts will not only get better at spotting weaknesses in their current defensive strategy, but will also be more likely to stay with an organization that supports their career and skill development.
We are already seeing companies adopt the purple team approach, with European IT services partner, Easi, using HTB to combine training for its red and blue teams. As a result, teams are more engaged and actively learning from each other, finding weaknesses, and developing critical thinking.
💡Note: Our Sherlocks Labs facilitate purple team upskilling with defensive and offensive versions of Machines for the full 360 learning experience:
|
Sherlocks |
Offensive |
|
There’s been a potential security breach within Forela's internal network. It’s your job to investigate, putting your digital forensics and network security skills to the test. |
Exploit an unauthenticated arbitrary file read vulnerability, gaining full administrative access to the machine. |
|
A critical alert has been raised over a newly implemented Apache Superset setup. You need to investigate and confirm the presence of any compromise. |
Test your web application skills as you attempt to exploit a vulnerability in Apache Superset. |
|
You have been tasked with the analysis of artifacts from a potentially compromised GitLab server. |
Explore how you can exploit and gain a foothold in a GitLab server. |
2. SOCs want hands-on development opportunities
Nothing leads to burnout quicker than a SOC analyst feeling as though they’re on the road to nowhere, repeating the same tasks day in and day out, without any opportunities to develop.
Break the day-to-day monotony by investing in your SOC team’s practical skills. This improves their performance, keeps them engaged, and boosts the overall defensive capabilities of your security function.
Our Developing the modern SOC analyst report revealed key areas analysts desire to upskill in:
-
Practical DFIR skills: 58.3% of analysts want to improve their practical DFIR skills with hands-on Machines.
-
Cloud security: Over 40% believe that cloud security skills will be a priority for analysts over the next five years.
-
Incident handling: Nearly a third (29.5%) of professionals rated Incident Handling Processes and Methodologies to be the most important knowledge domain for SOC analysts to master.
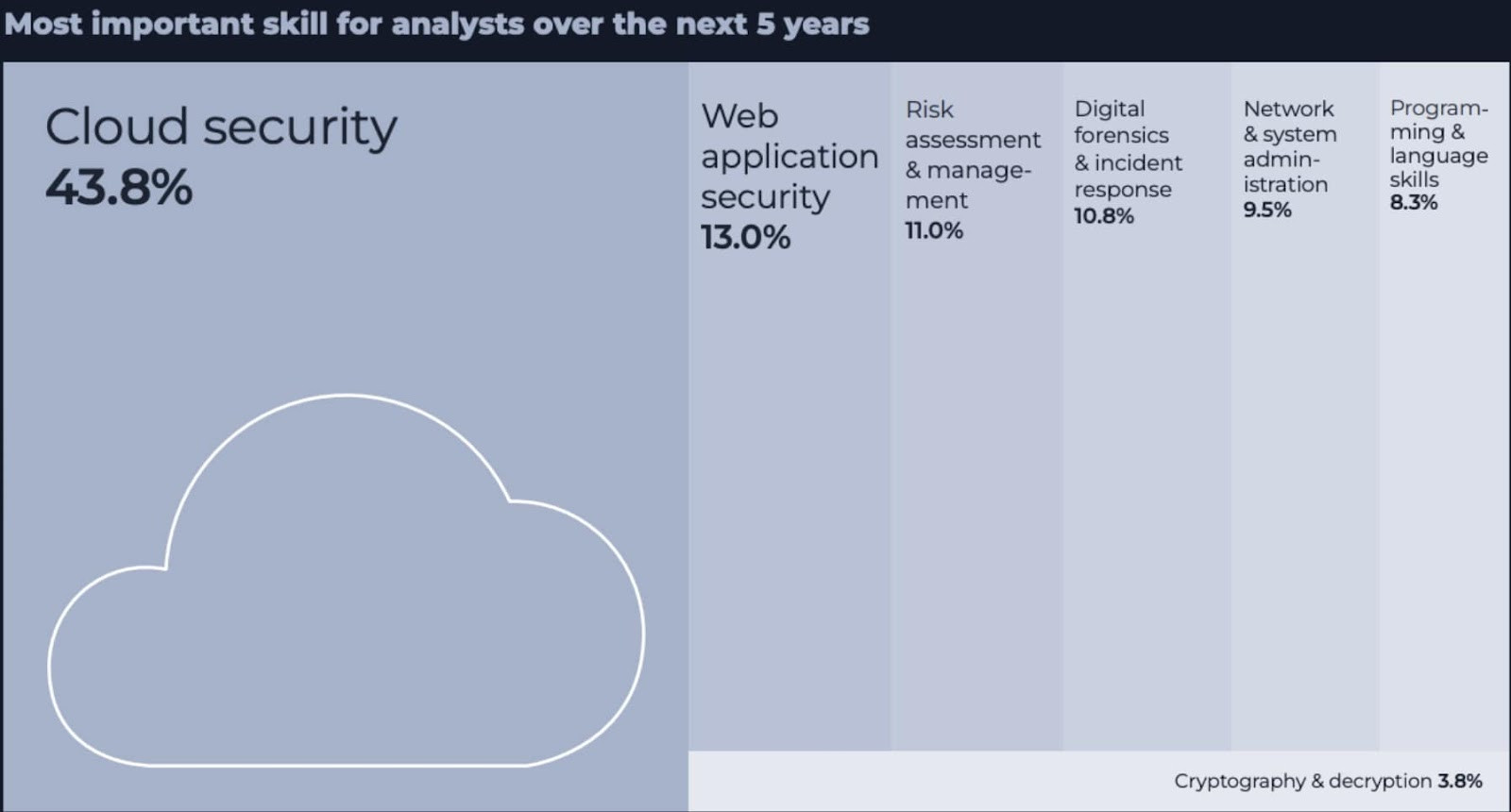
Set out a clear practical upskilling program, giving analysts something to work towards, and minimizing burnout due to monotony.
If you’re new to establishing a career pathway for SOC teams, try HTB Academy. We offer SOC analysts set paths to advance their careers and improve their practical skills:
|
HTB Certified Defensive Security Analyst (HTB CDSA) |
SOC analyst job role path |
|
|
3. Security staff value skills over salary
In our Cyber Attack Readiness report, we discovered that only 26.5% of security team members believed increasing compensation would keep them engaged at work. While 68% advocated for “opportunities to learn new skills” as the most effective way of staying engaged.
For managers dealing with strict security budgets, investing in skills development is much more effective than increasing salary, as the skills analysts learn will benefit your security posture, and improve their performance.
UnixGuy, GRC training professional, shared the same sentiment with HTB of providing upskilling to prevent burnout:
4. Regular events & challenges keep security teams engaged
Capture The Flag (CTF) events are a fantastic way to benchmark your team’s capabilities and identify areas of weakness. You can then focus your upskilling program on these key areas.
After surveying over 800 cybersecurity professionals in our Cyber Attack Readiness report, we found that more than 70% of managers view team events like CTFs as a viable way to boost employee engagement.
CTFs empower analysts to put what they’ve learned into practice, allowing them to track their performance and see the tangible results of their upskilling. This can help combat burnout and help them feel motivated to continue.
Looking for your next team CTF? Our Business CTF event features specific challenges tailored for defensive security professionals, including forensics and secure coding.
Overall the challenges were pretty realistic, which is a big plus for me. Would definitely recommend joining the CTF, as it lets you test your skills in realistic scenarios, and challenge yourself against the best specialists in the field. We will join again next year.
Lukasz Lamparski, Security Manager | Senior Incident Responder @ ING INGBank
Tackle burnout and transform your SOC team
Burnt-out SOC analysts are more likely to make mistakes and miss suspicious activity linked to a breach. This not only leads to financial damage and loss of customer trust, but can also have serious legal ramifications.
High employee turnover is also a huge consequence of burnout, meaning your already understaffed SOC team can jump ship, leaving you with a weakened security posture and a lack of talent.
Invest in your analysts with personalized development opportunities that’ll add real value to their careers. You won’t regret having a happy, healthy, and motivated SOC.
Boost employee well-being with HTB Enterprise Platform
At HTB, we provide a human-first platform creating and maintaining high-performing cybersecurity individuals and organizations.
How?
-
Clear skills development: Academy for Business offers defined job role paths mapped to MITRE ATT&CK frameworks, giving employees a clear goal and focus.
-
Work together: Dedicated Labs offer red and blue versions of Machines, encouraging teams to work together with purple exercises.
-
Engage and benchmark: CTFs allow cyber teams to practice skills while enjoying friendly competition, boosting morale.
-
Care for personal development: our reporting and tracking features give admins the chance to see how employees are developing, deploy cybersecurity reskilling programs, and reach out if they need more support.
|
Author Bio: Sabastian Hague (sebh24), Defensive Content Lead, Hack The Box Sabastian Hague is a seasoned cybersecurity professional with over eight years of experience in the field. After serving in the Royal Air Force as a specialist in all things SOC, he went on to work for Vodafone's global CERT team before taking on a role as a senior security consultant with SpiderLabs and working on numerous high-profile incidents. He is now the Defensive Content Lead at Hack The Box. Seb has numerous industry certifications, including GIAC Certified Detection Analyst (GCDA), GIAC Continuous Monitoring Certification (GMON), GIAC Certified Incident Handler (GCIH), GIAC Certified Intrusion Analyst, Offensive Security Certified Professional (OSCP), Blue Team Level 1 (BTL1), Blue Team Level 2 (BTL2), Cybereason Threat Hunter (CCTH). |
















