Red Teaming
What is penetration testing? (Explained by a real hacker)
The ins and outs of penetration testing from a hacker's perspective with insights from his fourteen-year cybersecurity career.

TreyCraf7,
Oct 25
2022
Table of Contents
- What is penetration testing?
- Why is penetration testing important?
- Different types of penetration testing (and their techniques)
- Common pentesting methodologies
- The 6-stage penetration testing process
- Pentesting vs. red teaming
- Qualities of great penetration testers or pentest teams
- Learn more about penetration testing
Breaching a military operations center under the quiet cover of nightfall was my first penetration testing experience.
When my Team Lead invited me to join the engagement, I was ecstatic. As a young IT and cybersecurity specialist in the Marine Corps, my natural response was: “You’ll pay me to do top-secret spy activities? Of course I'll help…”
My excitement was short-lived, however, and came to a crash when our team was spotted sneaking into the Operations Center compound.
We were aggressively apprehended by defenders and detained. This experience, and the many that followed it years later, taught me plenty of lessons (some more painful than others) about penetration testing and cybersecurity.
If you’re an infosec student, an aspiring penetration tester, or looking to work with or hire penetration testers, this guide will give you a comprehensive overview of what penetration testing is from an attacker's perspective.
You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. I’ll also share my personal insights on how to identify or become a great penetration tester (gleaned from years of military and contracting cybersecurity experience).
The ultimate pentesting certification
Accelerate your cybersecurity career with the HTB CPTS: The cost-effective, hands-on penetration testing certification that’s valued by employers, prepares you for real-world environments, and gets you job-ready.
What is penetration testing?
A penetration test (or pentest) is an organized, targeted, and authorized attack that tests IT infrastructure, applications, physical security, company personnel, and their defenders. The main goal is to determine susceptibility to legacy and bleeding-edge security vulnerabilities.
Mirroring the methods and techniques weaponized by real cyber attackers is critical. As penetration testers, we’ll do this by using various tools, tactics, procedures (TTPs), and personal insight to gauge the impact a particular vulnerability (or chain of vulnerabilities) has on the confidentiality, integrity, and availability (CIA) of data contained within information systems.
The steps in a penetration testing process vary from simple enumeration (information gathering) to making complex changes in an environment that enable our invasive actions. Such complex changes can trigger unintended consequences that we can’t predict (a quirk of each environment being unique).
So compared to something like a vulnerability scan, pentesting is a more intrusive, but comprehensive process with potentially unpredictable outcomes for customers. This requires relatively higher degrees of planning and caution when utilizing penetration testing tools and techniques within a customer environment.
Recommended resource: How to become a penetration tester
Why is penetration testing important?
Aside from the obvious advantage of identifying immediate security vulnerabilities and depicting an organization’s security posture, penetration tests carry multiple benefits.
A thorough test will:
-
Help pinpoint and prioritize the security flaws that need to be addressed.
-
Evaluate the effectiveness of existing security measures.
-
Reveal poor policy and malpractice.
Penetration testing is also a key part of maintaining regulatory compliance such as HIPAA, ISO/IEC 27001, PCI DSS, etc. This helps an organization or business prove that it takes serious measures to protect its infrastructure and any sensitive data it holds, which in turn bolsters product security and customer trust.
Different types of penetration testing (and their techniques)
Not all penetration tests are the same. A web application test, for example, will require different techniques and attack vectors for specific vulnerabilities when compared to a social engineering penetration test.

The type of tests we conduct will be determined by an organization’s needs and identified early with a detailed scope of work that clarifies testing parameters, the contract, and the rules of engagement. One organization may want an extensive test (Amazon Web Services) AWS pentest of their cloud-hosted infrastructure, another may want a physical test of their building's security. The most common types of penetration tests are:
-
Network penetration testing: Targets the design, implementation, and maintenance of a network’s infrastructure such as servers, firewalls, routers, and switches.
-
Web application penetration testing: Targets web-based applications and their security environments. This includes utilizing manual and automated testing methods to find and exploit code flaws, misconfigurations, and insecure software.
-
Mobile or Android penetration testing: Targets security weaknesses in mobile applications for common mobile vulnerabilities such as insecure data storage, authentication, or poor code quality.
-
Wireless penetration testing: Targets connections between devices via WLAN (wireless local area networks) and wireless protocols (such as Bluetooth) to identify vulnerabilities such as rogue access points and poor encryption.
-
Physical penetration testing: Targets physical weaknesses that are internal or external security implementations. This includes improperly installed sensors and cameras, poorly fitted doors, weak (or non-existent) locks, security personnel, etc.
-
Social engineering penetration testing: Targets the weakest link in any security chain: the human factor. People and processes are often probed with common workplace attacks such as phishing or spoofing.
Common pentesting methodologies
|
Black box (or external) penetration testing |
Black box tests simulate real-world cyber attacks by providing pentesters with little to no information about the IT infrastructure of a business. Penetration testers will “go in blind.” This forces them to closely follow the thought process and actions of an unprivileged attacker. |
|
Gray box penetration testing |
Gray box testing is a step up from black box testing. Instead of “going in blind,” attackers are granted some normal user-level privileges and might have some knowledge of a network’s infrastructure. |
|
White box (or internal) testing |
White box penetration testing involves sharing detailed information with pentesters that includes, network, system, and credential information. Testers are granted high-level privileges and are able to view source code. This helps them conduct a more comprehensive internal or behind-the-scenes assessment of one particular aspect of security. |
The 6-stage penetration testing process
During the penetration testing process, we as attackers will often follow the same cycle as a traditional malicious threat or “adversary,” albeit in a more targeted manner. This attack lifecycle can be summarized into the following stages:
1. Information gathering (enumeration)
Before any target systems can be examined and attacked, they must first be identified. This process is often called enumeration. Here a penetration tester will enumerate the customer, application, or system they are testing. The common things we are hunting during this early stage include anything from open ports (as seen in the GIF below), login credentials, DNS records, protocols on our target, and even publicly available information (via OSINT or Google Dorking).
(A scan of the open ports on a network. Executed on a live practice target via our Academy's in-browser tool, pwnbox. Click here to try it yourself.)
2. Vulnerability assessment
The vulnerability assessment builds on information gathered during enumeration. We’re probing for known vulnerabilities in the system or application; and will then test them with specialized tools and techniques to determine if there is indeed a method of exploitation.
3. Exploitation
Targeting the vulnerabilities identified in the previous step, an attack is crafted and executed. This could be anything from a crafted piece of code or malicious file used to exploit an OS or application vulnerability, to showing that file upload and execution capabilities exist within a web app.
Free guided cybersecurity courses
Learn cybersecurity skills from expert practitioners and specialists with free cybersecurity courses on the HTB Academy.
-
Interactive: Practice what you learn on live targets.
-
Browser-based: No tools or infrastructure needed. Train through your browser utilizing a web-based workstation.
-
Accessible: Courses for every skill level, ranging from fundamental to expert.
4. Post-exploitation
The post-exploitation phase is about diving deeper. An attacker will attempt to gather more information, elevate access (or privileges), and ensure they have a way to get back in if they lose access (this is called persistence). We’ll also revisit the information-gathering tasks performed earlier since we now have internal access.
5. Lateral movement
Signaling the end of the engagement, lateral movement focuses on moving closer to valuable assets. The goal is to “follow the trail” and extend access to other hosts and applications. Now that we have a solid access point (or foothold) within the customer’s network, it's time spread out and survey the environment to pursue highly-protected, precious intellectual property (IP), sensitive resources, or access to a host.
6. Proof of concept
The proof of concept phase is where specific vulnerabilities and security flaws are noted for reporting purposes. We are crafting the narrative that explains to customers how we gained access to their systems and how highlighted issues affect their security posture. This phase is key to tying everything together and ensures that the customer receives useful insights.
The six steps above describe the typical penetration testing process. Often the first four steps are repeated during an assessment. So if you’re an aspiring penetration tester, I’d advise you to keep a solid process for documenting your actions and findings! And if you’re looking to hire or work with a pentester, you should ask about these important stages.
Pentesting vs. red teaming
Penetration testing and red teaming are two terms that are often used interchangeably, but they aren't exactly the same. Both pentesting and red teaming:
-
Follow a normal attack cycle.
-
Look for vulnerabilities in organizations, applications, and systems.
Where these concepts differ is in the methods utilized and which type of organization deploys them. The purpose of a penetration test is to:
-
Identify vulnerabilities within a specific organization or application.
-
Prove that those vulnerabilities are exploitable.
-
Provide the customer with feedback and recommendations on how to fix the issue.
Red teaming, by comparison, is more clandestine and a bigger commitment for all involved parties. Red team penetration testers are no longer banging down the door trying to get in by all means; we’re picking the locks silently, monitoring from afar, and shadowing the target’s environment and activity while concocting extremely effective exploits.
This means maintaining a high level of stealth to avoid detection from an organization's security operations team while we craft custom payloads, utilize distributed Command & Control (C2) architecture to control access, and accomplish as much of the destructive mission as possible without being caught.
Red team tests are usually carried out on organizations with mature, well-developed security operations who wish to test their mettle against a representation of a sophisticated threat actor.
This engagement will attempt to emulate TTPs utilized by threat actors, ransomware groups, APTs, and even insider threats in order to hit a specific goal. That goal could be systems compromise, simulated disruption, simulated IP theft, and more.
Another key point here is that red team engagements are usually unannounced. Defenders will often work in their normal posture and will not be alerted or warned of an attack.
Qualities of great penetration testers or pentest teams
Now that you understand what a penetration test is, I’ll share the common qualities great penetration testers have. This will help both aspiring-intermediate pentesters (and even those looking to hire them).
Tenacity and out-of-the-box thinking
A degree from a prestigious college or a new training certification certainly helps one to become proficient in the knowledge, skills, and abilities required to work in this field, but they don't make up the core of who a penetration tester is.
A great pentester is an unrelenting problem solver. One with the tenacity to dig deep into the root of a problem, the continuous curiosity to interrogate seemingly imperceptible details, and the creativity to think outside the box.
Are these the only traits a pentester should have? Of course not. But they are character traits that describe many of the penetration testers I personally know.
Up-to-date knowledge
From new hardware and applications to new tech concepts such as artificial intelligence (AI) and quantum computing, it's often a challenge to stay current. With so much change, continuous learning is critical and common among all good penetration testers.
Luckily for us, between the many guided cybersecurity courses, numerous write-ups, CTFs, and blogs available, there is no shortage of training opportunities. Take advantage of them if you’re looking to grow your career.
And if you’re hiring cybersecurity professionals, actively seek evidence that candidates are continuously developing their skills.
It’s hard to match formal qualifications and CVs to on-the-job performance. That’s why I pay attention to a candidate’s attitude and extracurricular activities.
One example is HTB activity on a resume when hiring juniors. It shows that a candidate is deeply motivated and invested in developing their skills.
Jeremy Chisamore, Senior Penetration Tester, Oracle
For recruiters: Penetration tester job description template
Solid reporting skills
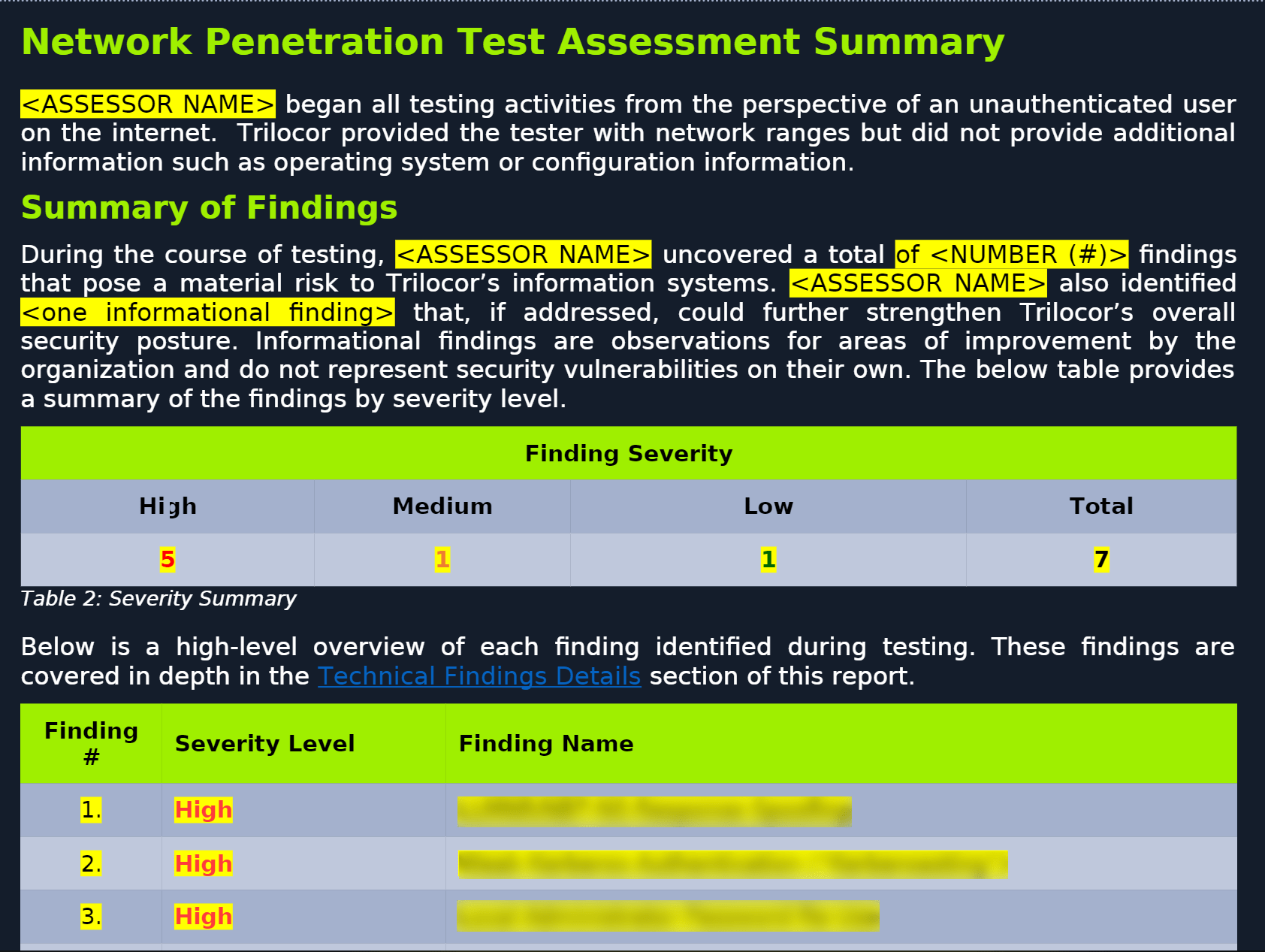
Documentation is often tedious and nowhere near as exciting as actually conducting or learning about a penetration test. But an organization needs a detailed explanation of how and why it got pwned and what it should improve to prevent security issues.
As a penetration tester, telling an organization that you were able to pwn their systems and leaving it at that is a quick way to lower the value you deliver to a client and ruin your reputation in the community.
As a provider of cybersecurity labs and training that prioritizes embedding practical, job-ready skills in our students, this is why we include a penetration testing reporting template in our CPTS penetration testing certification with a detailed explanation of how to report.
Learn more about penetration testing
Want to learn more about the awesome art of penetration testing or cybersecurity?
Get started for free with the HTB Academy’s guided and interactive courses.
|
Author bio: George Bilbrey (TreyCraf7), Academy Training Developer at Hack The Box. With fourteen years of cyber security experience spread across military service (United States Marine Corps) and private consulting, George is passionate about pentesting, ICS Security, and helping others grow and improve their knowledge by creating innovative and engaging content and supporting various non-profits helping bring security to the masses. Outside of content creation, he's a founding member of the cyber security community The Neon Temple in Tampa Florida, and holds several certifications that include CISSP, GICSP, GCIP, and more. |